Special Analysis Report on the “SwimSnake” Cybercrime Group
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
The “SwimSnake” cybercrime group has been active since the second half of 2022, launching a large number of attacks against domestic users. This cybercrime group has attracted widespread attention from the domestic security industry this year due to its diverse malicious program variants, rapid updates and anti-virus methods, frequent infrastructure changes, and wide-ranging target industries.
The “SwimSnake” criminal group spreads malicious programs through instant messaging software, malicious search engine promotions, and phishing emails. They utilize methods such as “white-and-black,” “memory shellcode execution,” and “memory decryption payload” to ultimately implant remote control Trojans on victims’ computers. After gaining control of the victim’s computer, the group primarily manipulates the victim’s WeChat account to carry out subsequent attacks and profit. On one hand, the group uses the victim’s WeChat account to distribute malicious programs to their friends or groups, further expanding the scope of infection. On the other hand, the group controls the victim’s WeChat account and conducts fraudulent activities by impersonating their identities or maliciously creating groups, thereby illegally obtaining financial benefits.
Antiy CERT has been continuously monitoring and tracking the “SwimSnake” cybercrime group, and discovered the operating model of cybercrime groups mainly composed of the “SwimSnake” cybercrime group. Based on the analysis of samples, it has summarized the attack methods and technical characteristics of the cybercrime groups, revealed the common fraud routines used by the cybercrime groups, and summarized effective protection suggestions to help users understand and identify the common tricks of the cybercrime groups, avoid being harmed by their remote control Trojans, and avoid suffering economic losses from fraud by cybercrime groups.
For more detailed information about the group, please refer to Antiy Virus Encyclopedia.

Long press to identify the QR code to view the detailed information of the “SwimSnake” group [1]
It has been verified that Antiy Intelligent Endpoint Protection System (IEP) can effectively detect and kill this remote control Trojan.
Antiy Security Threat Detection Tool can detect systems infected with this type of “SwimSnake” Trojan.
2.Sample Analysis Reveals the Attack Methods of Cybercrime Groups
Cybercrime groups primarily spread malicious programs through instant messaging software, malicious search engine promotions, and phishing emails. The initial malicious program is typically a malicious downloader. After execution, it accesses trusted websites or the attacker’s server, retrieves the malicious payload files hosted there, loads and executes them, and utilizes a combination of “black and white” methods, “memory shellcode execution,” and “memory decryption payload” to evade antivirus detection. Ultimately, the malware executes the Gh0st remote control Trojan in memory and typically achieves persistence, allowing it to reside on the victim’s host for a long time.
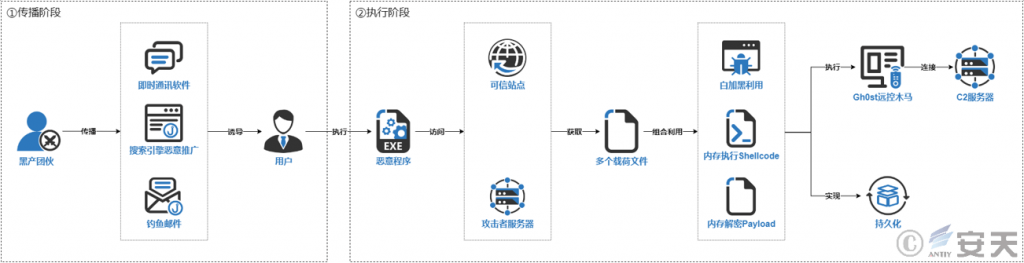
Figure 2‑1 Typical attack process of a cybercrime group
2.1 Malicious Program Spread
Cybercrime groups mainly spread malicious programs through instant messaging software, malicious search engine promotion, phishing emails and other channels.
2.1.1 Instant Messaging Software
In the “Analysis of the “SwimSnake” cybercrime group’s Activities of Spreading Malicious Codes via WeChat” [2] , Antiy CERT detailed the cybercrime group’s operation model of recruiting a large number of members by recruiting “agents” to help them complete the large-scale spread of malicious programs. In addition, Antiy CERT found that the malicious programs spread by the cybercrime group through instant messaging software have some specific behaviors after execution. According to their behaviors, they can be divided into three categories: double-click malicious programs, image-jumping malicious programs, and damage malicious programs.
2.1.1.1 Double-Click Malicious Programs
After executing a double-click malicious program, the mouse cursor will often spin in a circle for a few seconds. Attackers use instant messaging software to trick users into executing the malicious program and determine whether the malicious program is executed based on user feedback (text, screenshots, or screen recordings).
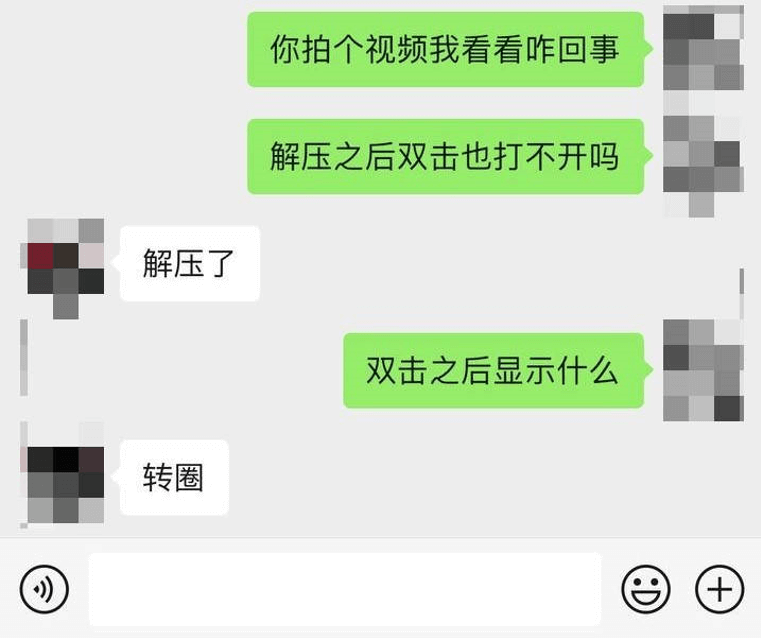
Figure 2‑2 Chat logs related to double-click malware
2.1.1.2 Image-Jumping Malicious Programs
C2 server, image pop-up malware also retrieves and opens an image file. This method can confuse the user, and the attacker can also determine whether the malicious program is executed by judging whether the image pops up in the user’s feedback.
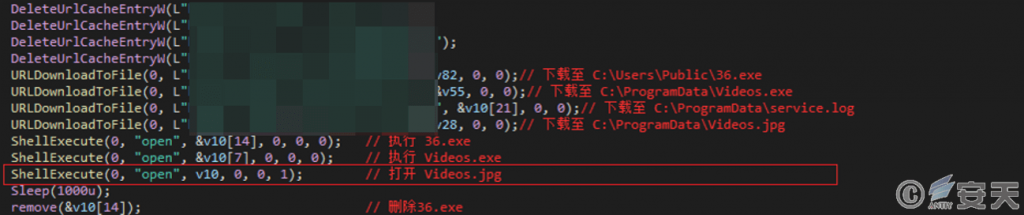
Figure 2 ‑3 Download and open the image file
2.1.1.3 Damage-Related Malicious Programs
After obtaining and executing the required malicious payload file, the corruption malware will pop up a constructed error message, which generally contains the words “The file is corrupted” as well as the machine’s GUID and current time.

Figure 2 ‑4 Pop up a constructed error message window
When the victim user executes a malicious program and sees an error pop-up window, he or she often thinks the file is damaged and actively sends a screenshot to the attacker for inquiry. The attacker can then determine that the malicious program has been executed.
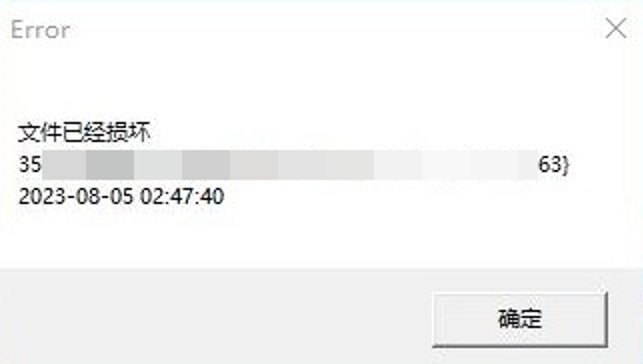
Figure 2 ‑5 Error pop-up window
2.1.2 Malicious Search Engine Promotion
Cybercrime groups forged download web pages for commonly used application software such as WeChat, DingTalk, WPS, and PDF Converter, and purchased advertising space on mainstream domestic search engines to maliciously promote their fake download sites, thereby inducing users to download and execute malicious programs.
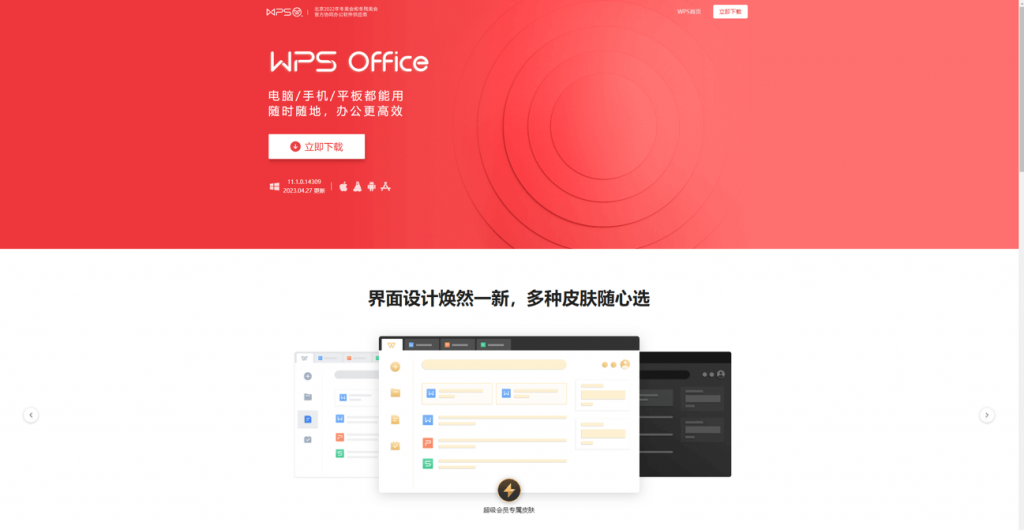
Figure 2‑6 A fake download site forged by a cybercrime group
2.1.3 Phishing Emails
When delivering malicious programs through phishing emails, cybercrime groups will send phishing emails to users with subjects and content related to “invoices” and “subpoenas”, and the emails usually contain hyperlinks.
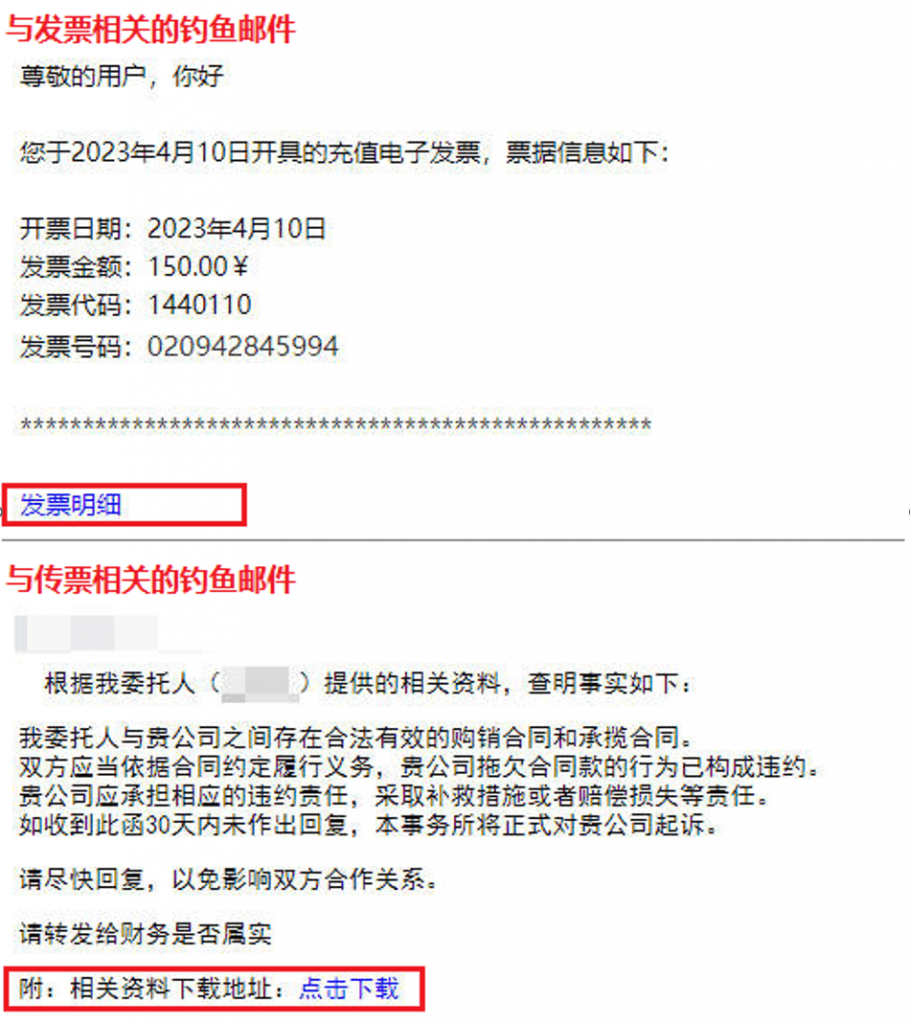
Figure 2 ‑7 Phishing emails related to “invoice” and “subpoena”
When users click on the link, they are redirected to a phishing website disguised as providing billing services or posing as a tax authority. Cybercrime groups use bill-related phishing emails and phishing websites to trick users into downloading and executing malicious programs.
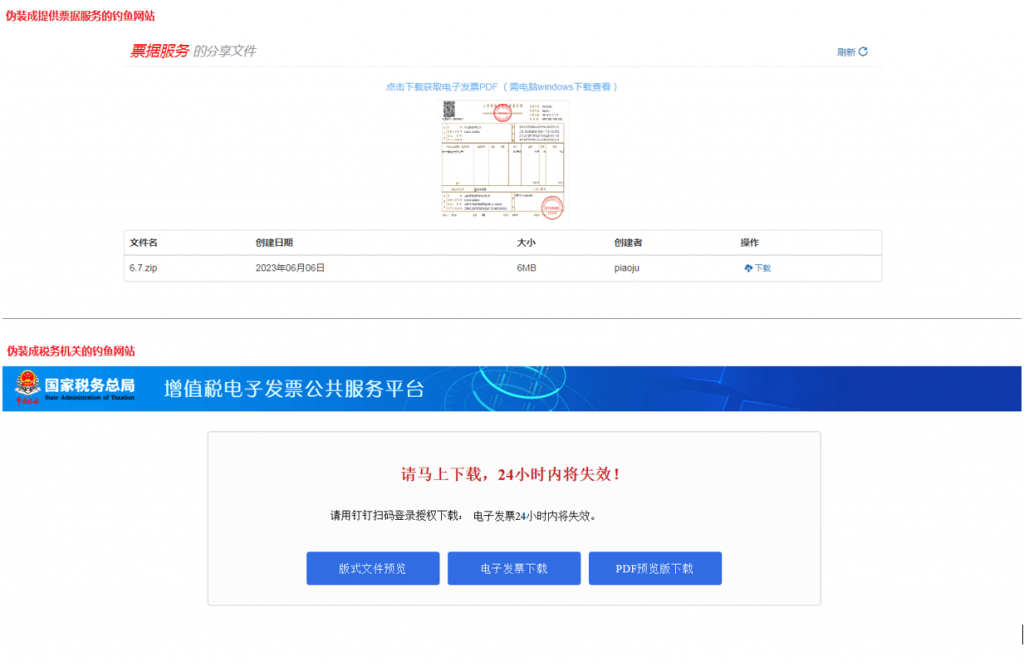
Figure 2 ‑8 Phishing websites
2.2 Malicious Program Execution
The initial malicious program spread by cybercrime groups is usually a malicious downloader. After execution, it obtains the next stage of malicious payload files by accessing trusted websites or attacker servers, loads and executes them, and combines “white and black”, “memory execution of shellcode”, “memory decryption of payload” and other methods to ultimately execute the Gh0st remote control Trojan in memory.
2.2.1 Malicious Payload Hosting Method
2.2.1.1 Trusted Sites
In “Analysis of Attack Activities Using Cloud Note Platforms to Deliver Remote Control Trojans” [3] , Antiy CERT introduced the attack activities of cybercrime groups using cloud note platforms to deliver remote control Trojans. The attackers packaged the malicious payload files into a compressed package and hosted it in the created cloud note sharing platform, with the aim of using trusted sites to evade security products on the traffic side. After the malicious program it spreads is executed, it obtains the malicious payload file from the shared link, thereby completing the subsequent attack process. Currently, multiple cloud note sharing platforms used for attack activities have been observed, the earliest of which was created in January 2022.
Table 2‑1 Cybercrime groups create cloud notebook sharing to host malicious payloads
| Username | Shared folder name |
| vip0418123000 | 签名正版 |
| quanshiyu2022 | GUDUO |
| quanshiyu2022 | XSD |
| Ireallycanth | Endless sea of bitterness |
| m15529105475 | wx |
| m15529105475 | kky |
2.2.1.2 Cybercrime Group Infrastructure
When cybercrime groups host malicious payloads in their own infrastructure (such as HFS servers, FTP servers, etc.), they will try their best to avoid detection of the malicious payloads. In addition to encrypting the payload files, they may further remove or encrypt the PE file headers, split the payload files, and other operations to evade detection by security products.
2.2.2 Malicious Payload Loading Method
During the malicious payload loading phase, cybercrime groups often use methods such as “white and black”, “memory execution of Shellcode”, “memory decryption of Payload”, etc., and use these methods in combination.
White and black: Cybercrime groups exploit the flaws of some normal programs that do not perform strict verification when calling required modules or script codes, construct malicious DLL files or add malicious script codes, and thus use normal programs to execute malicious codes.
In “Analysis of the Large-Scale Attack Campaign Launched by the “SwimSnake” cybercrime group Against Domestic Users” [4] , Antiy CERT introduced the cybercrime group’s method of using the NetSarang series of tools to update the program to launch attacks. When the program is executed, it loads the dat file with the same name in the same directory and parses the script code in it. The attacker takes advantage of this to add malicious code to the original script, thereby executing malicious shellcode. It has been observed that the cybercrime group has used this method to implant remote control Trojans in multiple attack activities.
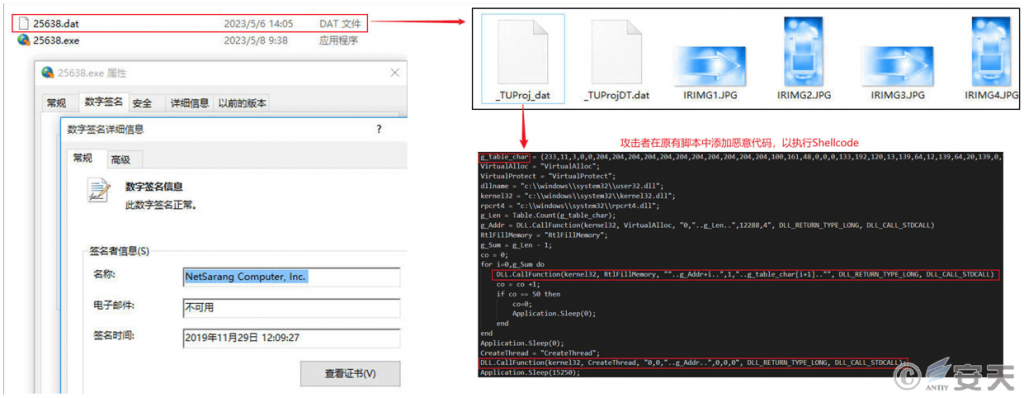
Figure 2‑9 Using the NetSarang series of tools to update the program and execute malicious Shellcode
Memory executing shellcode: Cybercrime groups typically save their shellcode to text files, use a loader to read the contents of the text, and execute the shellcode in memory. There are two main types of shellcode written by cybercrime groups: one type is used to detect the presence of security products in the system and create a scheduled task for the loader to achieve persistence on the victim host; the other type is used to retrieve, decrypt, and load remote control Trojans for execution.
Memory decryption payload: Cybercrime groups usually encrypt the remote control Trojan payload in advance and use the corresponding decryption algorithm to decrypt it during execution, thereby loading and executing the final remote control Trojan in memory.
2.2.3 Memory Release Gh0st Remote Control Trojan
The Gh0st remote control Trojan consists of two parts: a controlled terminal and a control terminal. The controlled terminal, implanted in the victim’s host, collects various information from the host, including basic system information, window information, and antivirus product information. It then constructs an online packet and sends it to the C2 server, establishing communication with the control terminal. The communication is encrypted and decrypted using a custom algorithm.
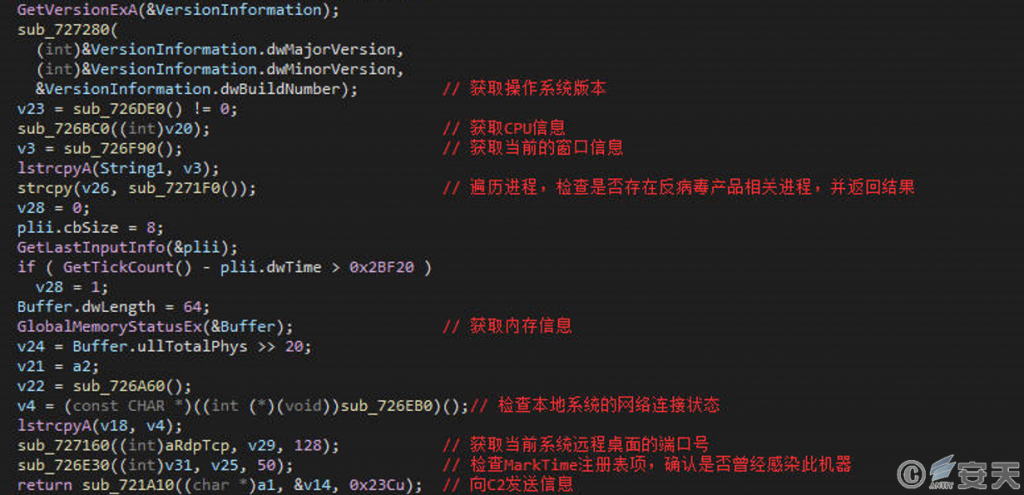
Figure 2 ‑10 A variant of the Gh0st remote control Trojan collects information and structures an online package
The Gh0st remote control Trojan can receive remote control commands to execute corresponding functions and supports expansion of its functional modules by downloading and executing plug-ins. The captured control program shows that this remote control Trojan has multiple functions, mainly including displaying the controlled terminal’s online information, monitoring the controlled terminal’s screen, managing the controlled terminal’s system files, and remotely controlling it.
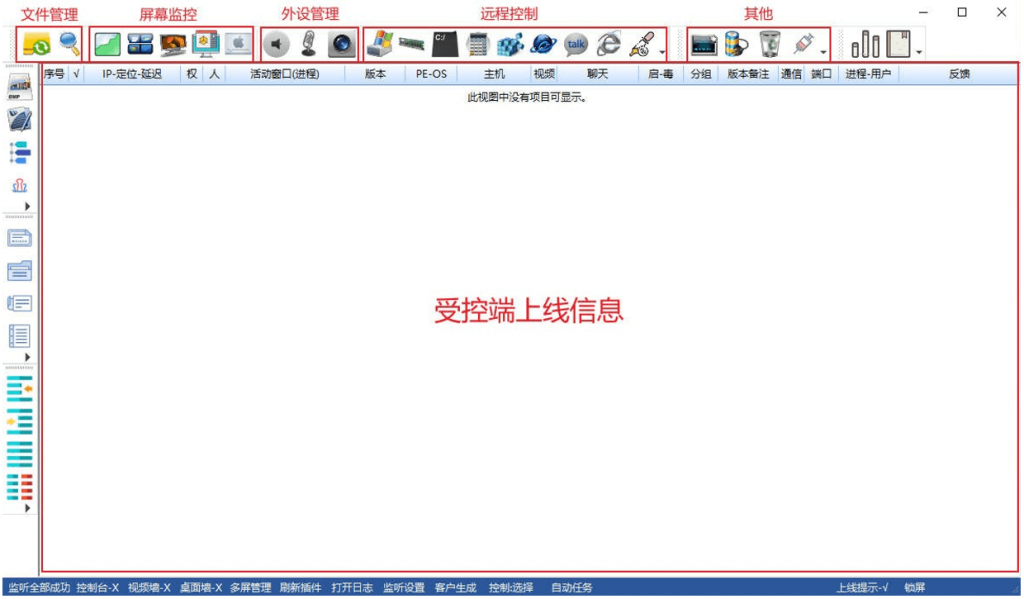
Figure 2 ‑11 Gh0st remote control Trojan control terminal program
It has been observed that while the control-end programs used by cybercrime groups vary, they are generally consistent. Because the source code for the Gh0st remote control Trojan has been open source for many years, and the Trojan and its numerous derivatives have been widely circulated within the cybercrime, cybercrime groups can quickly build control-end programs and their corresponding controlled-end Trojans, and then evade anti-virus software on the controlled-end Trojans.
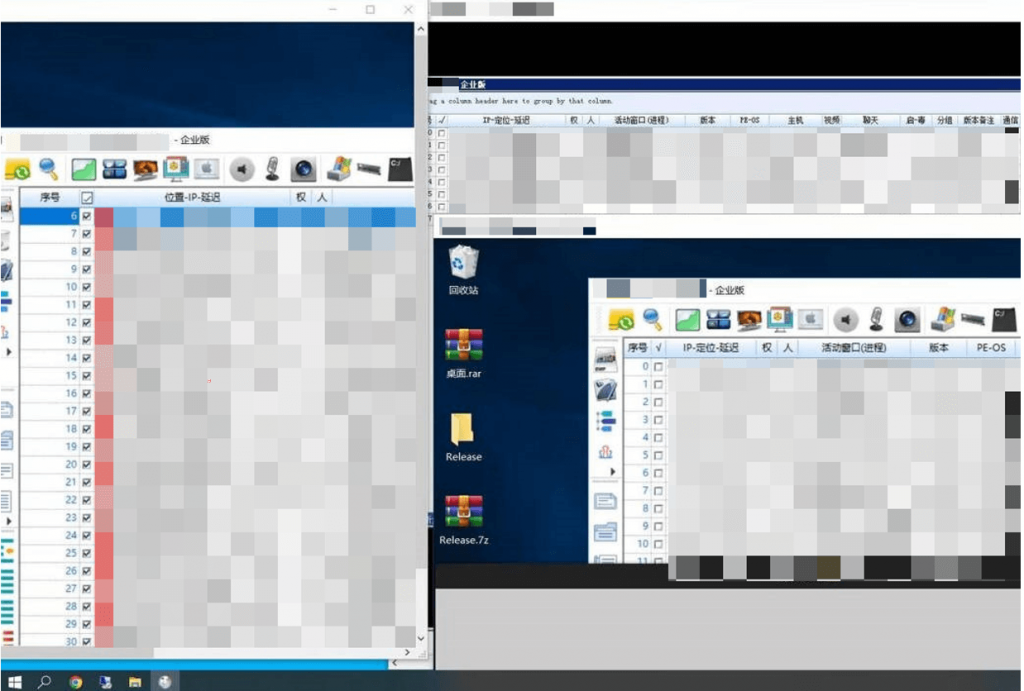
Figure 2‑12 Control-end program used by cybercrime groups
3.Several Ways for Cybercrime Groups to Monetize
Implanting the Gh0st remote access Trojan, the criminal group primarily controls WeChat and WeChat for Business accounts on the victim’s computer to carry out subsequent attacks. On the one hand, the criminal group uses the victim’s WeChat to distribute malicious programs to their friends or groups, further expanding the scope of infection. On the other hand, the criminal group controls the victim’s WeChat account, disguises themselves as someone else, and defrauds the victim or their friends, or maliciously groups the victim’s friends and then conducts fraud.
3.1 Committing Fraud After Disguising One’s Identity
Cybercrime groups use remote control Trojans to remotely control the victim’s host, control the victim’s WeChat, and pretend to be the victim to defraud their friends; or they control the victim’s WeChat to delete one of their friends, and then add an attacker’s WeChat account with the same avatar as the friend, thereby pretending to be the friend and defrauding the victim.
3.2 Fraud Committed After Maliciously Inviting People to Join a Group Chat
The criminal group adds the victim’s WeChat account to a pre-created WeChat group, controls the victim’s WeChat to add their friends to the group, and then removes the victim’s WeChat account from the group.
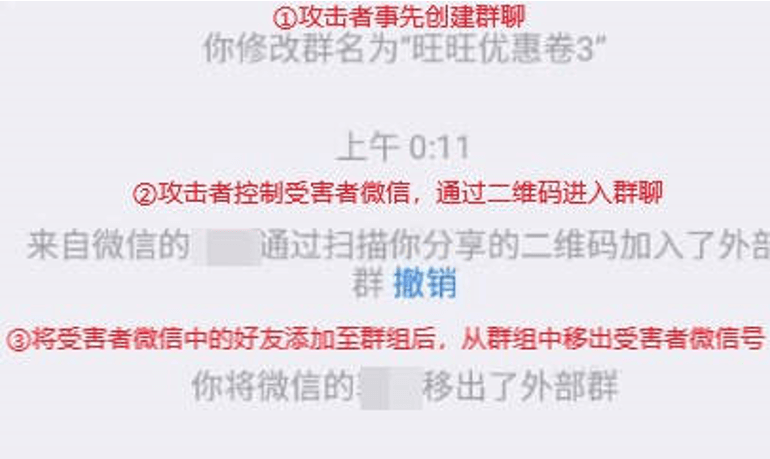
Figure 3 ‑1 The steps taken by the cybercrime group to control the victim’s WeChat and maliciously create a group
In order to prevent being discovered by victims, cybercrime groups will carry out activities between 12 am and 6 am. The names of the groups they create are usually related to lectures, exchanges, coupons, benefits, etc., and the relevant groups are marked with numbers.
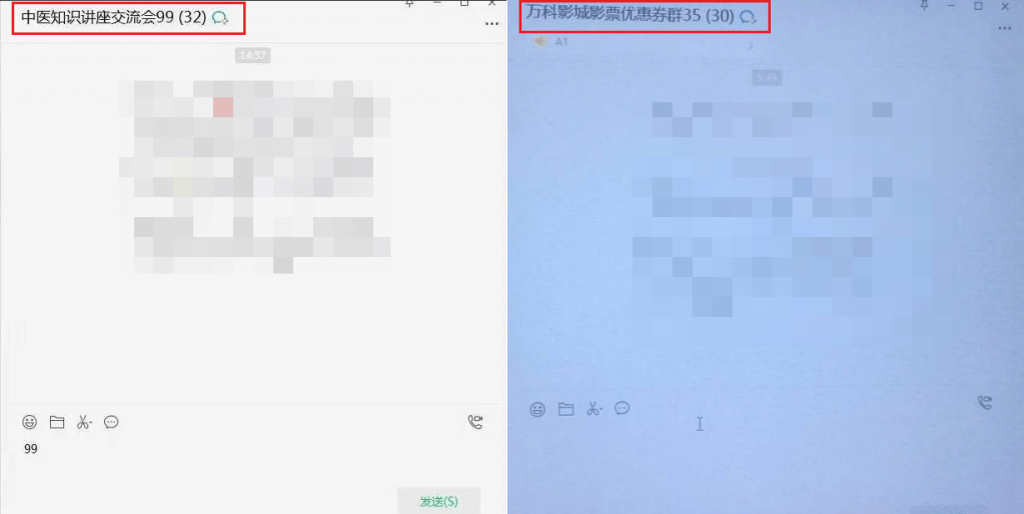
Figure 3‑2 Groups created by two cybercrime groups
Cybercrime groups will lower users’ vigilance by sending red envelopes in groups, induce users to join large groups, add receptionists on WeChat, and usually send text messages in the form of pictures.
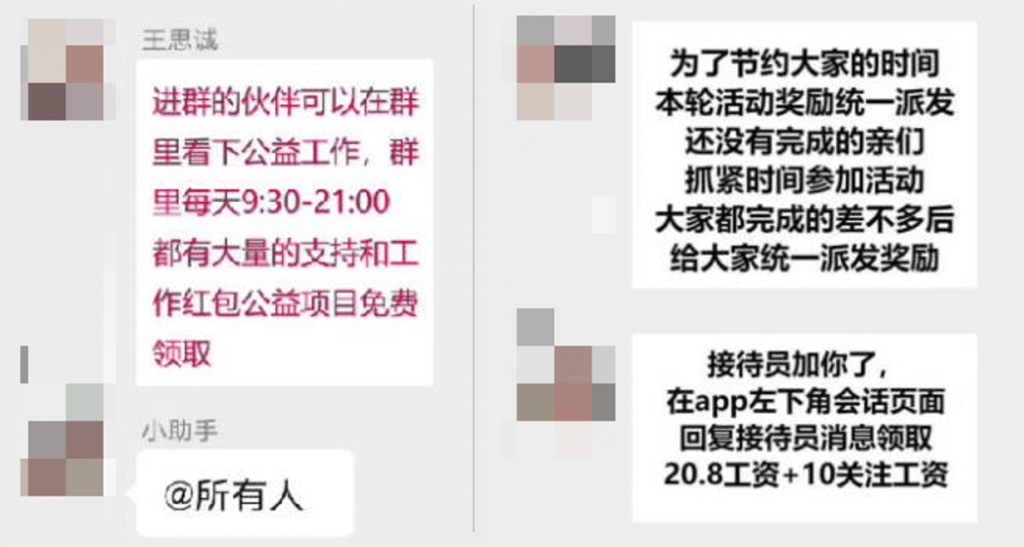
Figure 3‑3 Cybercrime groups sending text messages in the form of pictures
Finally, the cybercrime groups will defraud the selected victims, induce them to transfer money, and will no longer contact the victims after the fraud is successful.
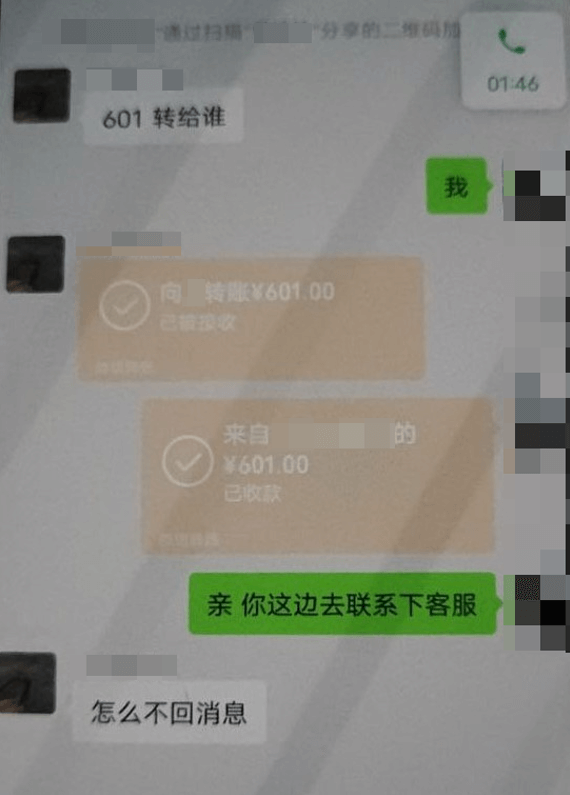
Figure 3‑4 Cybercrime groups induce users to transfer funds
4.Protection, Investigation and Disposal
1. Enhance the security awareness of business personnel
Enhance business personnel’s security awareness and reduce the organization’s vulnerability to attacks. Customer service and sales personnel using desktop instant messaging apps like WeChat and WeChat for Work should avoid being tricked into downloading and running files from unknown sources due to the nature of their work or personal interests. Organizations can strengthen their “first line of defense” by opting for security awareness training services.
2. Antiy Security Threat Detection Tool to detect the SwimSnake payload
If you discover or suspect that you have been attacked by the “SwimSnake” cybercrime group: For the Gh0st remote control Trojan launched by the “SwimSnake” cybercrime group in its attack activities, download the Antiy Security Threat Investigation Tool [5] (http://vs2.antiy.cn , tool name: “SwimSnake” special investigation tool ) from the Antiy Vertical Response Platform to quickly detect and investigate such threats in the face of sudden security incidents and special scenarios.
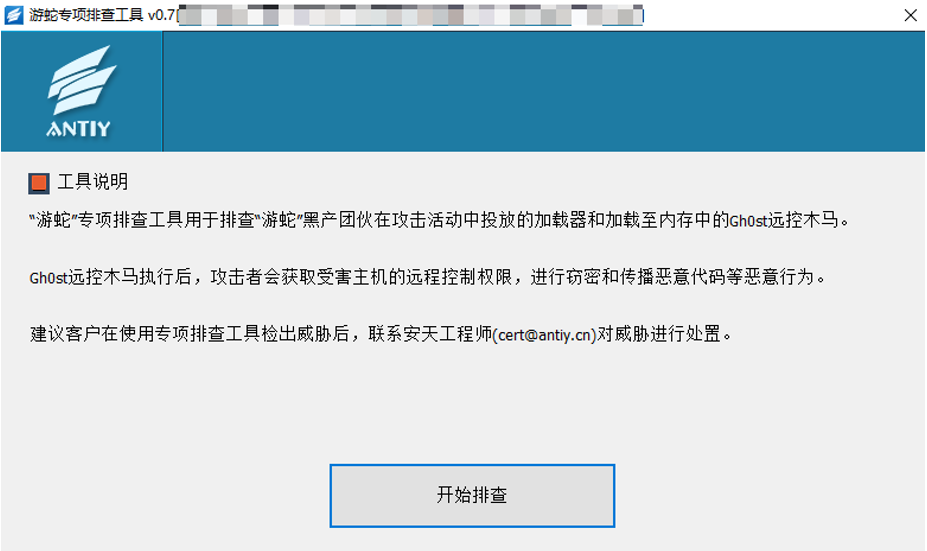
Figure 4 ‑1 Special inspection tool for “SwimSnake”
The “SwimSnake” special troubleshooting tool is used to detect loaders and the Gh0st remote access Trojan loaded into memory by the “SwimSnake” cybercrime group during their attacks. Once the Gh0st remote access Trojan is executed, the attacker gains remote control of the victim’s host, enabling them to steal secrets and spread malicious code.
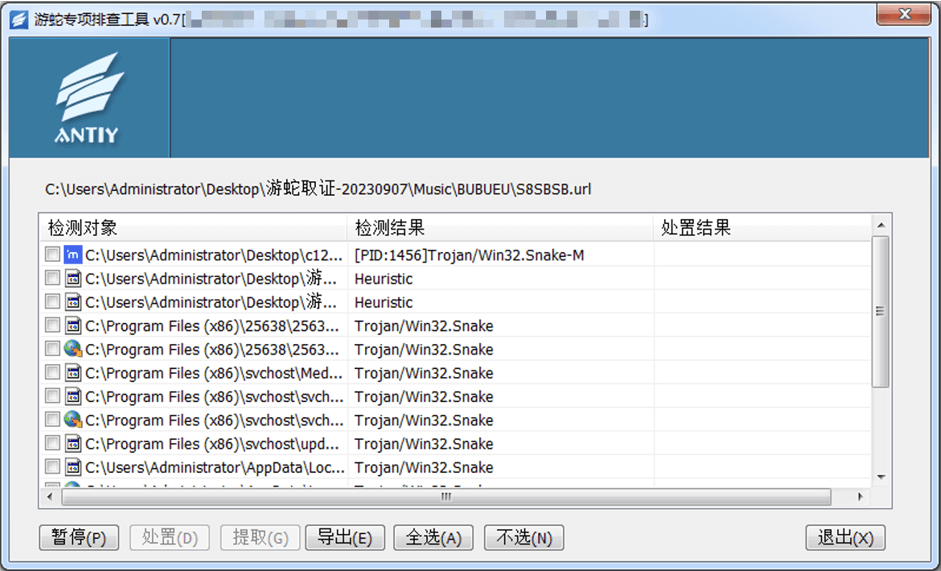
Figure 4 ‑2 Troubleshooting threats related to “SwimSnake”
Since the attack payloads used by the “SwimSnake” cybercrime group are iterating rapidly and their anti-killing technology is constantly being updated, in order to more accurately and comprehensively eliminate threats existing in the victim host, it is recommended that customers contact the Antiy Emergency Response Team (cert@antiy.cn) to handle the threats after using special troubleshooting tools to detect them .
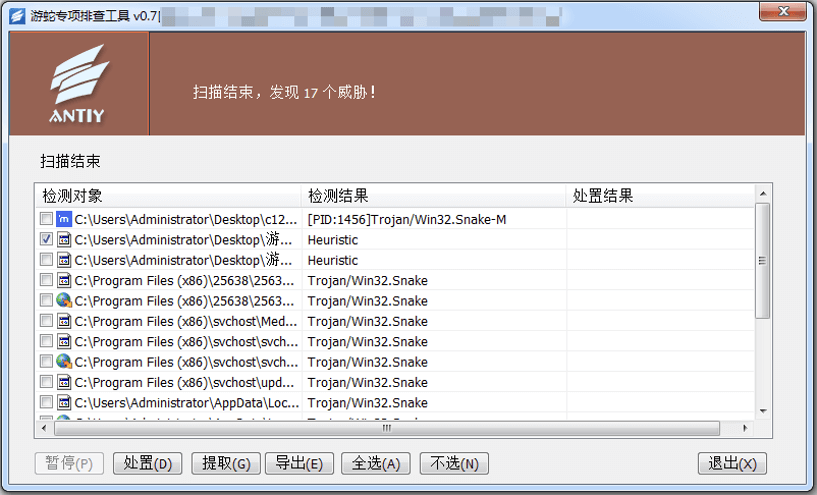
Figure 4 ‑3 Discovering threats related to “SwimSnake”
Call Antiy’s 24/7 service hotline at 400-840-9234 for help: If you are attacked by malware, it is recommended to isolate the attacked host in a timely manner and secure the site while waiting for security engineers to investigate the computer.
3. Strengthen terminal file reception and execution protection
Deploy an enterprise-level endpoint defense system to provide real-time detection and protection against unknown files received by instant messaging software. Antiy IEP’s endpoint defense system uses Antiy’s next-generation threat detection engine to detect files from unknown sources and prevent them from landing and running through kernel-level active defense capabilities.
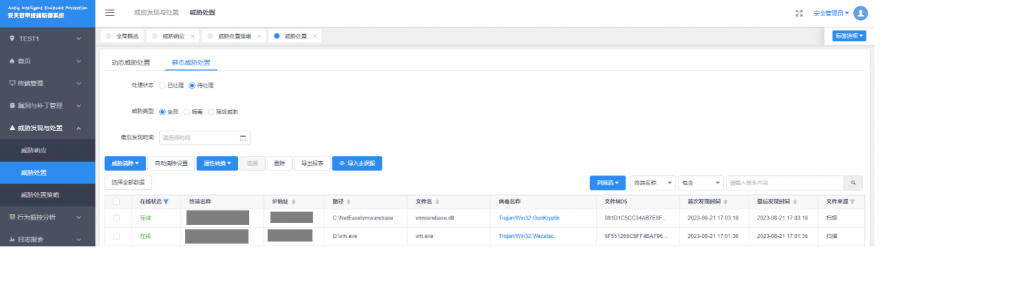
Figure4‑4 Antiy Intelligent Endpoint Protection System effectively protects against attacks by the “SwimSnake” cybercrime group
To combat the attacks of the ” SwimSnake ” (a Chinese cybercriminal group) , IEP has upgraded its “Infected Environment Detection” and “Scheduled Task Defense” modules. When the “SwimSnake” group distributes malicious programs to target terminals through phishing and other means, inducing users to execute them, IEP monitors scheduled tasks in real time. Once a task with the “SwimSnake” signature is detected, IEP immediately analyzes its running parameters, assembles the complete path of the malicious program, terminates the malicious program process, and deletes the file, effectively identifying and blocking malicious code while it is running. Once the blocking is complete, a pop-up window alerts the user, ensuring a secure business environment.
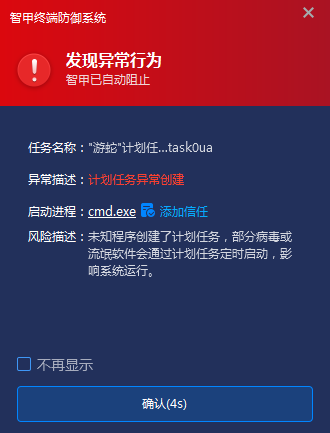
Figure 4 ‑5 Antiy Intelligent Endpoint Protection System intercepts the abnormal creation of the planned task
Finally, in response to this type of attack mode that ultimately targets the terminal through induction and malicious construction, Antiy recommends that customers promptly update the feature libraries and rule libraries of products such as Intelligent Endpoint Protection System and Persistent Threat Detection System, configure security management and alarm strategies, and continuously respond to such attacks.
Appendix 1: References
[1] Antiy: For detailed information on the “SwimSnake” group, please refer to the Antiy Virus Encyclopedia
https://virusview.net/malware/Trojan/Win32/SwimSnake
[2] Antiy: Analysis of the “SwimSnake” cybercrime group’s activities of spreading malicious code via WeChat
https://www.antiy.cn/research/notice&report/research_report/SnakeTrojans_Analysis.html
[3] Antiy: Analysis of Attack Activities Using Cloud Note Platform to Deliver Remote Control Trojans
https://www.antiy.cn/research/notice&report/research_report/20230324.html
[4] Antiy: Analysis of the large-scale attack activities launched by the “SwimSnake” cybercrime group against domestic users
https://www.antiy.cn/research/notice&report/research_report/20230518.html
[5] Antiy: Antiy Security Threat Troubleshooting Tool (Download the “SwimSnake” special troubleshooting tool)
Appendix 2: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


