FROM EQUATION TO EQUATIONS
FROM EQUATION TO EQUATIONS
Revealing the multi-platform operational capability of Equation Group
Antiy CERT

Draft: Jan. 15, 2014 16:43 (UTC+8)
Published: Nov. 4, 2016 10:00 (UTC+8)
Updated: Nov. 4, 2016 13:00 (UTC+8)
1 Background
From February 2015, Antiy has published two reports about Equation Group, both of which analyzed the code components for Windows platform, the persistent ability in disks and the use of encryption algorithms. In this report, Antiy will publish the analysis of Equation components for Solaris and Linux platforms for the first time. We can also be proud to say that this is the first report to prove the existence of these kinds of “Evils”. We actually finished the analysis several years ago, and Antiy has concerned with the Great Attack Group since 2012, and trying to analyze its operational in all invasion and persistence scenarios, where the core targets are the server operating systems, such as Linux, Solaris and FreeBSD. These loads are not usual script Trojans, but are binary components with an encrypted communication. These components act as Rootkits, and have strict encryption anti-analysis technique and trick. Therefore, Antiy has named attacks performed by super-attack organizations as A2PT, and make the capabilities to attack all platforms indicators.
Based on long-term experience in tracking and analyzing capability of advanced threats and malicious code, Antiy’s product PTD (Persistent Threat Detection System) can help users capture the payload delivery and lateral movement; IEP (Intelligent Endpoint Protection System) provide protection for traditional Windows hosts and Chinese Operating system, and assists PTA (Persistent Threat Analysis System) to analyze malware for various platforms. The deployment of these products also enables customers to support Antiy to get more threat indicators. Meanwhile, we have been paying attention on open-source intelligence and public information, also the information and development trends of relevant organizations.
After Kaspersky and Antiy released reports about Equation (called the Group for short) last year, the Group still launched a series of attacks. In August 2016, the malware used by Equation was disclosed in Equation Group Cyber Weapons Auction – Invitation [1], and this group was connected with attack weapon system named ANT for the first time. Based on this, we can also find its ability to inject and persist in products of Cisco, Juniper, Fortinet and other firewalls. On October 31, 2016, an article called Shadow Brokers reveals list of servers Hacked by the NSA [2] was published in The Hacker News, which contained more documents revealed by Shadow Brokers, including some of the foreign server list compromised by the Group. The related documents claimed that most of the infected servers are running Solaris, Oracle-owned Unix operating system, and some are running FreeBSD or Linux. With the mutual prove of public information and Antiy’s analysis conclusion of the samples, we can clearly figure out the powerful full-platforms attacking capability of this organization.
Our analysis work is continuously validated by ongoing information. During the past years, the analysis of this attack was sophisticated and challenging; whose analysis is more difficult than Stuxnet or Flame. The malware with this kind of highly complex and hidden capability is a huge challenge for both victims and analysts. Especially when the scope of its combat coverage of almost All computer architecture and operating systems, the traditional security team relatively good at analyzing the malware for Windows, Linux and Android and other mainstream operating system platform will feel much more pressure and challenges. If you use the name of Equation to do a parable about the difficulty of analysis, what we need to conquer is not an “Equation” but more complex“Equations”.
Antiy Labs released the Chinese version of this report on November 4th, 2016. Due to the lack of translation ability and experience, the English version was not released synchronously. Many colleagues in international cybersecurity field may read this report with the help of Google Translator. This version got finished until November 8th, and we welcome your advices and suggestions.
2 The multi – platform operational capability of Equation
Equation employs engineered and standardized attack weapons arsenals, including EquationLaser, EquationDrug, DoubleFantasy, TripleFantasy, Fanny and GrayFish. Antiy has found samples of EquationDrug and DoubleFantasy attacking on other platforms. The arsenal information is shown in the following table:
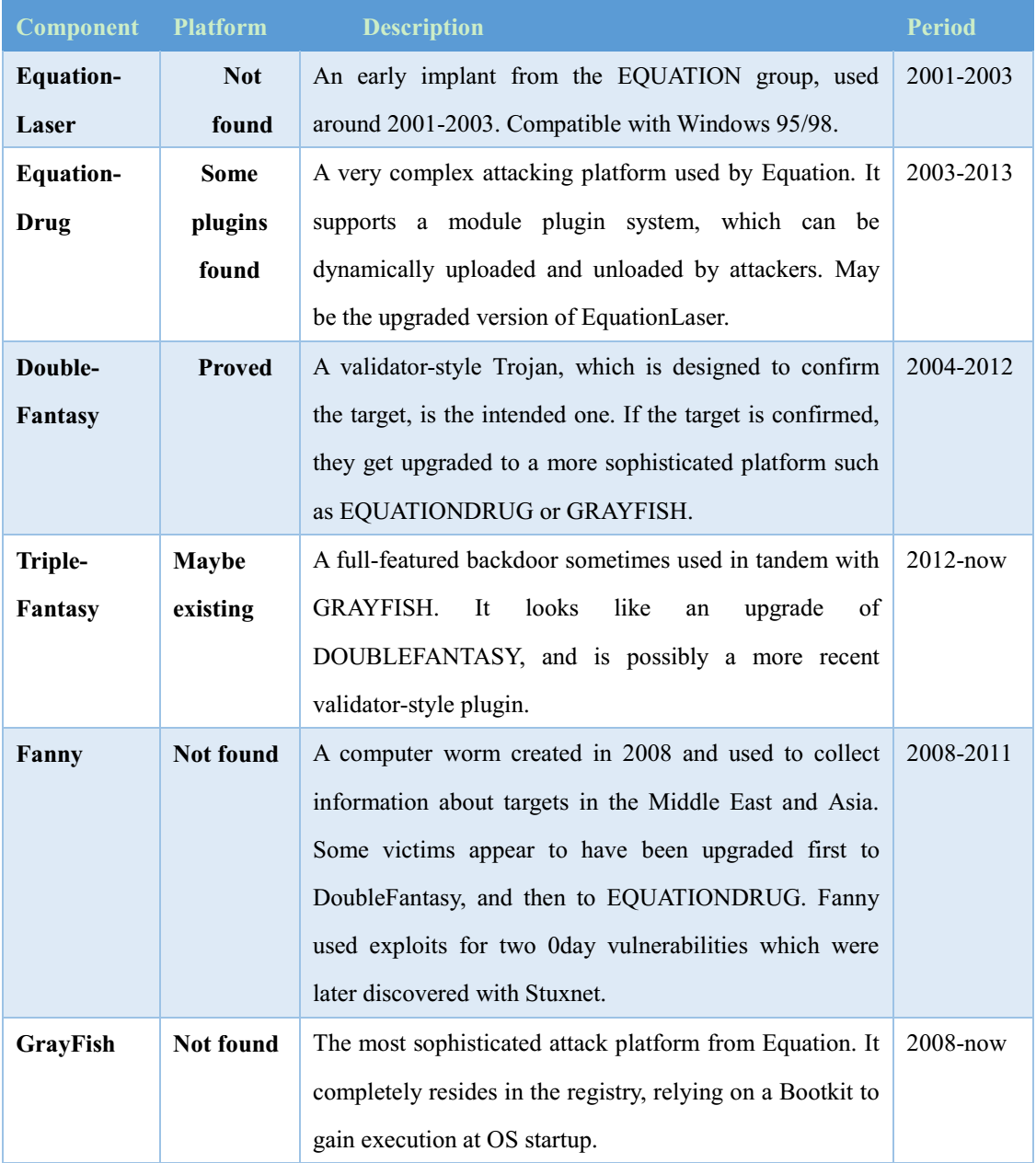
Based on the following table, readers can put together jigsaw puzzles of Equation attack.
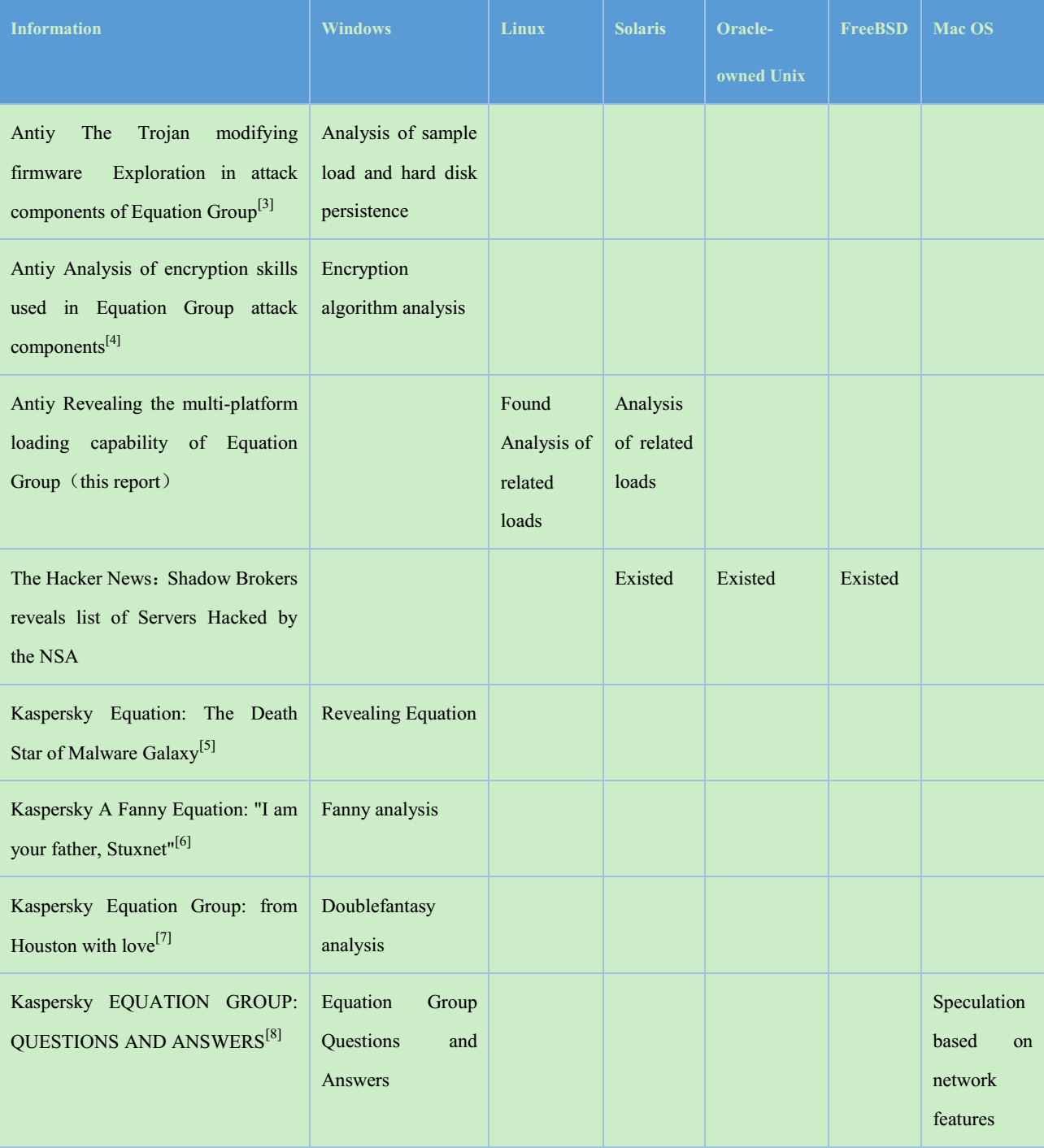
Note: Antiy has found User Agent with Solaris logo during the analysis of samples, and Kaspersky released a series of reports, revealing the Equation Group; one named as “Equation Group Questions and Answers”[8] publishes the capture information of the Mac OS X Agent. So far, both Antiy and Kaspersky or other vendors have not yet capture Mac OS X samples, but the payload for Mac OS X does exist.
3 Analysis of Partial Load for Linux in X86
We have captured the samples on Linux platform and confirmed that the sample is DoubleFantasy component after analyzing. The component is used to perform incipient detection on targets with Linux platform. It is a sample of the Linux platform, so it has different features with others.
3.1 Preceding Module——DoubleFantasy
3.1.1 File Tag

3.1.2 Running Process
On Linux platform, samples execution is divided into two cases, with parameters or no parameters. If the parameter ‘-c’ engages in, only system information can be obtained and it can be regarded as scene detection. The process is following:
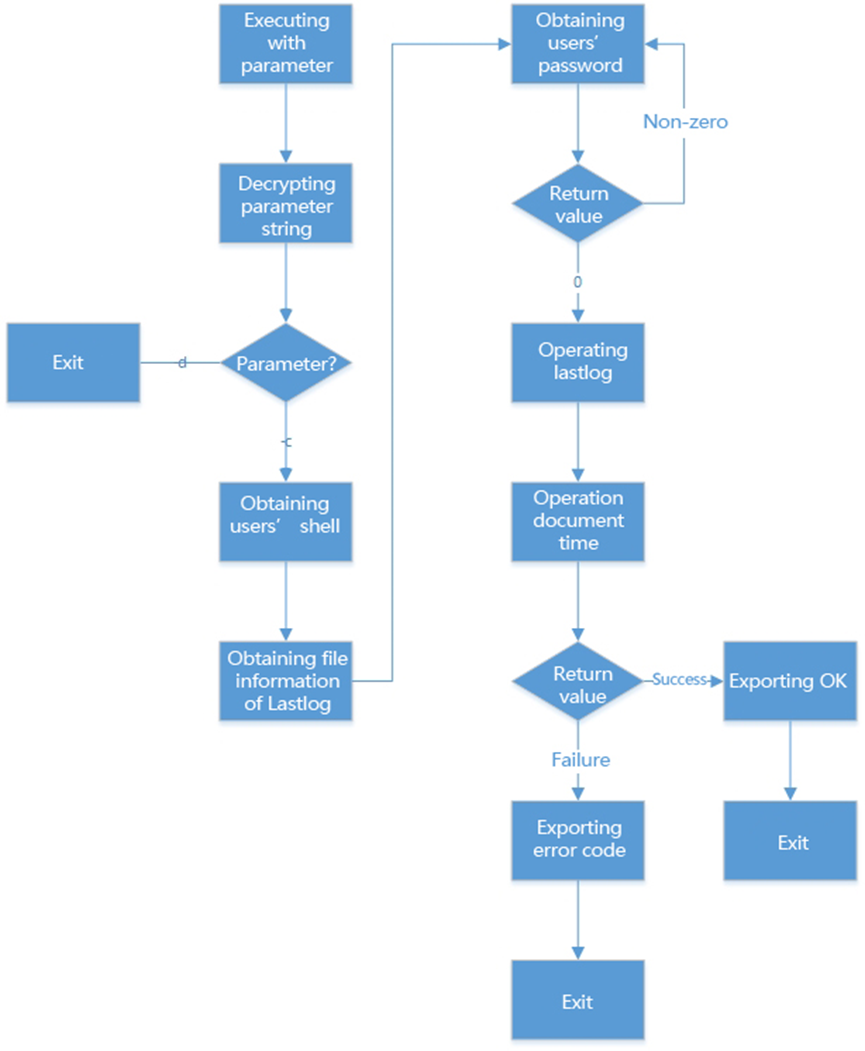
Figure 1 Operational process with parameter–c
In the case without parameter ‘-c’, the process is following:
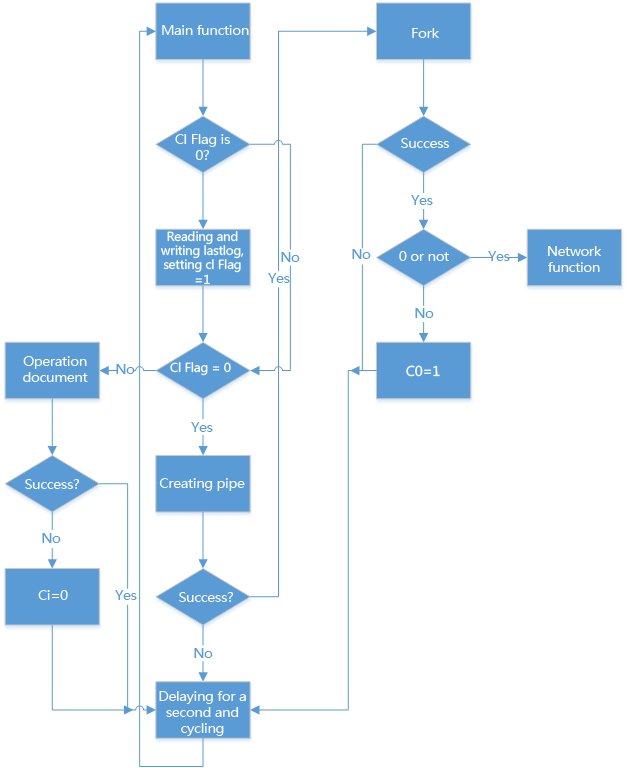
Figure 2 Running process without parameter–c
3.1.1 Basic functions
· Traversing system files, clearing / var / log / lastlog records, obtaining system account password information.
· Connecting Google to determine network connectivity.
· Connecting remote sever and making different operations based on remote control instructions.
· Many encryption algorithms used in communication and information.
· Starting itself with a linked file, and the proc /% d / exe file pointing to the files of the sample.
· Opening three PID threads (two of them are consecutive) after running.
· Collecting information about infected computers, including system directory, file extension, and other information. As shown below:
Collecting information about infected computers, including system directory, file extension, and other information. As shown below:
Figure 3 Collecting basic system information
- The malware starts process fork() and determine the PID number of its child process. If the execution succeeds, then the main function will exit and cannot debug. Debugging process is shown as below:
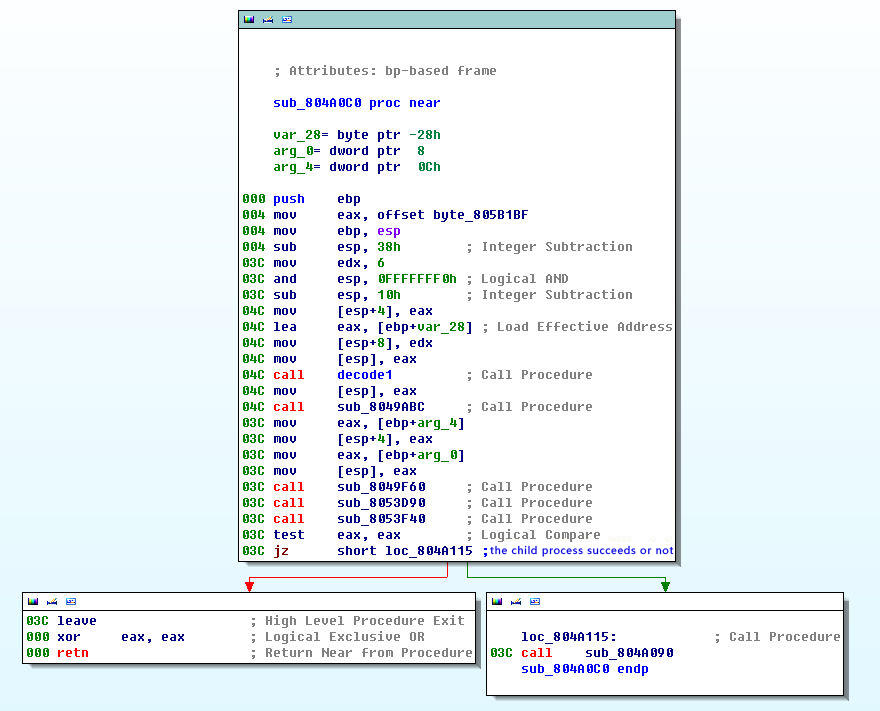
Figure 4 Sub-process judgment
- Decrypting various strings, obtaining user’s information including the system version
- Obtaining user’s login information getpwnam
- Viewing file /bin/fast /sbin/login /usr/sbin/nologin
- Getting user’s login password getpwuid
- Read user’s logvar/log /lastlog
3.1.4 Dynamic Loading of Function and Data
The function and data called by this sample is dynamically loaded and debugged, dynamic debugging is wanted in the analysis. We explain the calling addresses through dynamic analysis decryption, and the details are shown as bellows:
Figure 5 Function call address
3.1.5 Decryption and Analysis of String
In the sample, a self-defined encryption algorithm is used to encrypt the internal string information. The algorithm is called 115 times. The encryption algorithm is as follows:
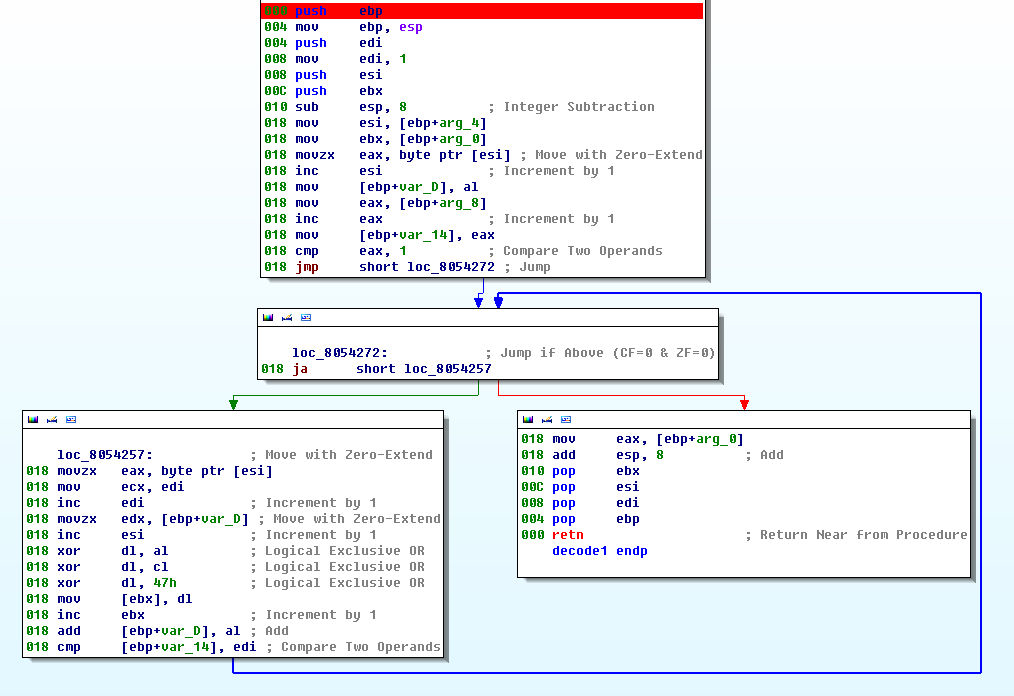
Figure 6 String encryption algorithm used in Linux samples
3.1.6 Network Communication Encryption
During the period of network communication performed by Linux samples, the 16-bit key hardcoded in the sample is the same as the 16-bit key in the Windows platform DoubleFantasy sample that encrypts the registry:
66 39 71 3c 0f 85 99 81 20 19 35 43 fe 9a 84 11
The calculated subkeys are:
E9 BE CD E0 A8 9F 4D DB C3 42 AC 2B 24 77 AB CB 5A C1 52 F8 5B 3E F0 78 CB 01 0A 69 29 8F 85 8C
03 9C 7C EF 5E 36 0E 8B C0 40 76 28 9C 9C F2 24 81 9D 02 72 4F 6A BB B5 5B 42 73 14 88 F2 73 75
8B F9 37 98 3B 9F 64 2B A3 C4 FF C7 8A 40 67 C1 25 9F 65 54 45 36 48 FF E2 86 05 1A F4 94 AC 2B
08 D5 E5 83 BE 2C AD EE D0 A6 98 CB 8D 35 ED EE C4 F0 8C F2 CD BA 87 03 54 27 3D 13 A7 9B 6A 05
C7 02 30 21 05 67 58 3B E6 A1 44 0A 37 16 3C 86 E9 BC 8B 20 1A 98 7E 28 E6 7F F7 CA F7 9E 38 31
7F F0 2F 93 11 2B 28 F0 FF 11 B7 FC 1C 63 86 CB
The custom algorithm for Linux samples is the same as for Windows, and there is only one encryption key to use (Because the Linux system does not have a registry, there is no registry encryption function). It uses the Windows platform Key for encryption and decryption, and we can see that both platforms use the same secondary key transformation algorithm (Specific details can be seen in the Windows encryption algorithm analysis part).
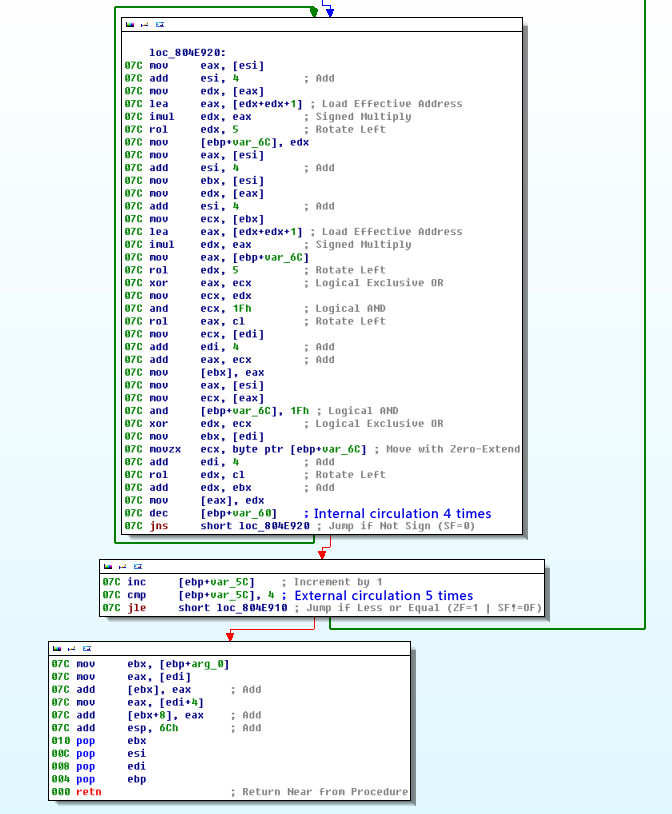
Figure 7 Secondary key transformation algorithm
3.1.7 Network control instruction
Instruction branch of Linux sample is basically the same as Windows. There are a total of nine instruction branches, and the function is also roughly the same. The instruction codes are: 0x4A, 0x4B, 0x60, 0x70, 0x75, 0x76, 0x78, 0x79, 0x80.
Figure 8 Instruction branch code for Linux samples
The function of instructions for Linux system is the same as the Windows sample function, only with the difference between obtaining system information. The following shows Linux sample accessing to information format:
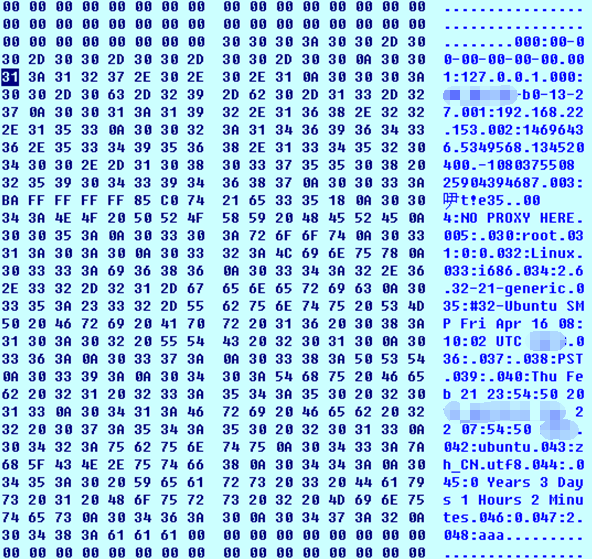
Figure 9 Linux sample accessing to information format
The description of obtaining information format:

4 Attack Payload for Solaris SPARC
Equation may have created the first malware with Rootkit features in SPARC architecture, and provide cover for DoubleFantasy targeting Solaris.
4.1 Solaris and SPARC
Solaris is the computer operating system which is developed by Sun Microsystems. It adopts SPARC or X86, and is mainly used for workstations, servers, operating systems. The malicious code on Solaris platform is rare. From Antiy’s statistic, there are no more than 60 kinds of malicious code variants which are binary compiled form even in the period of SUN OS. They are almost based on X86 platform.
The full name of SPARC is Scalable Processor Architecture, one of microprocessor architecture. Its instruction set is significantly differ from X86 and has its own unique window, delay slot, the process call features.
The computer which has SPARC is generally used for industrial, space-related areas. It is seldom used in similar IDC and general IT scenario.
4.2 Hidden Rootkits
This is a rootkit program on the Solaris platform of the SPACR architecture. It is primarily responsible for hiding the main function sample files like other rootkit programs, as well as the associated derived files and itself, including process, file, and service information. It runs on the target computer firstly, investigates system environment, configuration information, network status of the target computer, and hides the specified files and processes.
4.2.1 File Tags
4.2.2 Main function
The samples have 249 functions, as shown in the sample main function flow. Some of the functions are relatively complex. There are a variety of encrypted data in the samples.
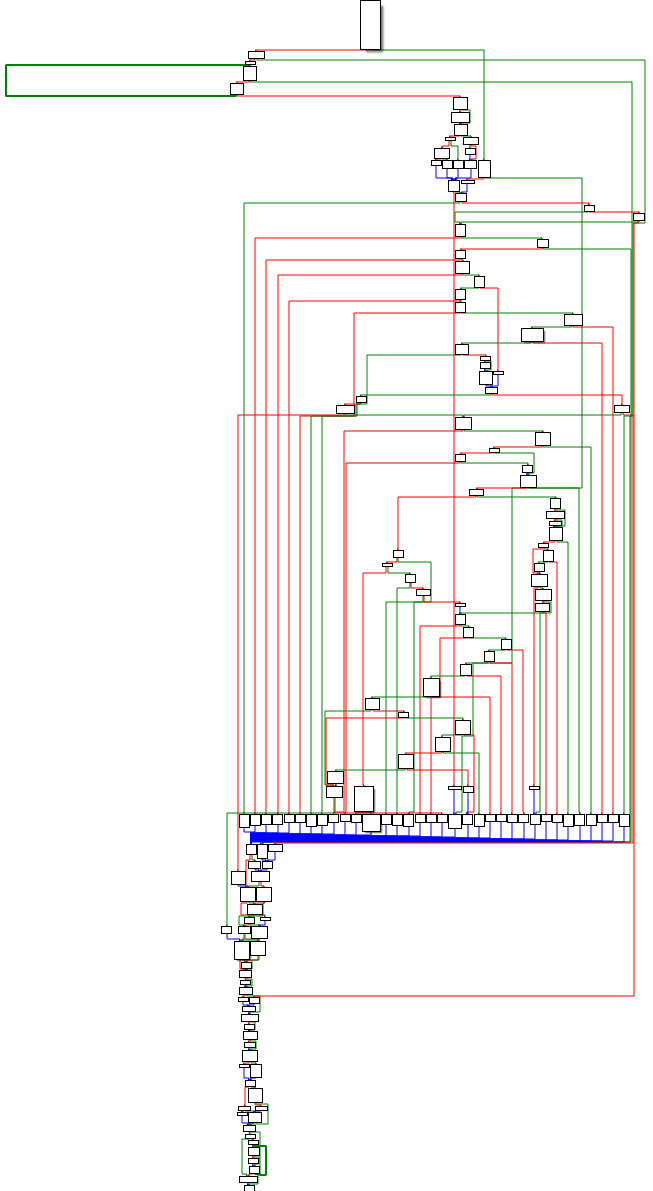 Figure 10 Main functions of the samples
Figure 10 Main functions of the samples
4.2.3 Derived file name and path
After running, it can combine two sets of strings which are according to the internal configuration to generate file name as its own new file name, and copy itself to the / sbin / directory.

We can find that these words are highly frequency words or suffix used in system files and system command. Thus, the file name of the sample is carefully structured and confusing. The general administrator is also difficult to detect abnormal situation in the system files.
4.2.4 Starting script
The script realizes the startup by using the service. It creates the script in the etc / rc.d / directory (S85s%). This script will run with the start parameter as the service which is executed when open the computer.
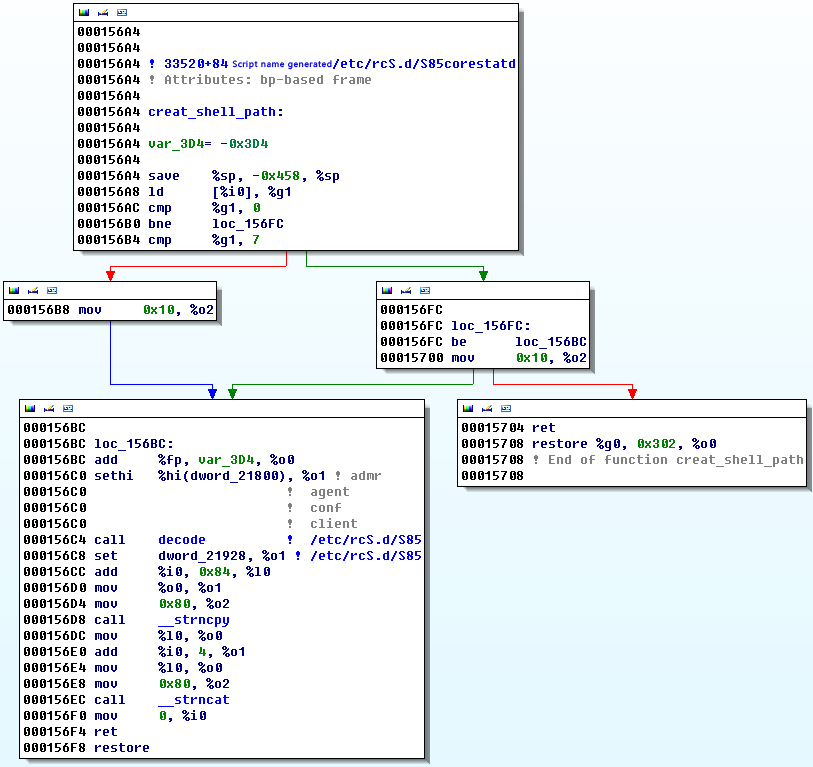
Figure 11 Service script
The content of S85s% document is encrypted. After running, it can call its own function to decrypt, and modify the variable of the file name. Then it can write into /etc/rc.d/ directory (It will be modified to the path of the sample in figure below % E).
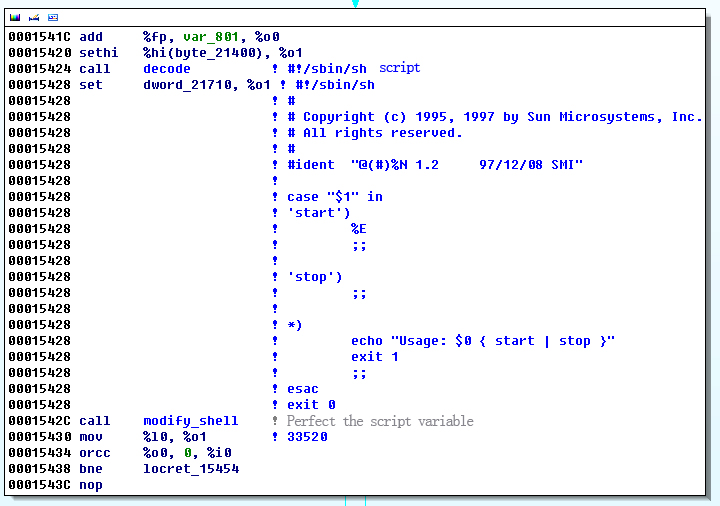
Figure 12 The content of the script after decryption
4.2.5 Hidden directory and files
The sample will generate MD5 based on HOSTID of the target computer, then calculate class base64 algorithm, take the first six bits finally. It can splice .tmp with the first six bits into a folder name and create the folder.
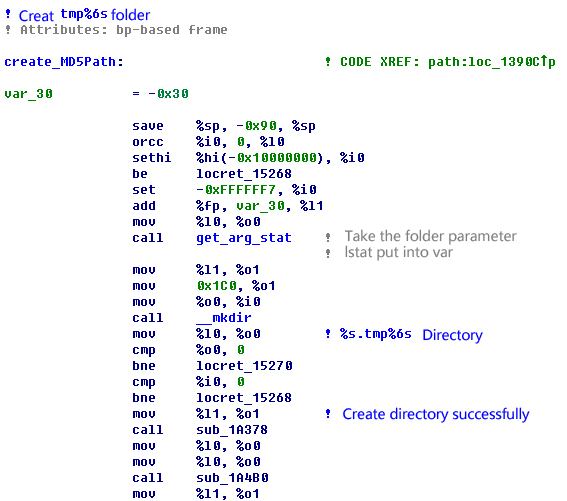
Figure 13 Folder name created by samples
The sample will also copy other files to execute according to the running parameters. It is responsible for hiding all the files in this folder.
4.2.6 Version judgement
The sample can determine that the system is not sun4m, sun4d version through the uname function. And it can determine the system architecture by reading / dev / ksyms files: i386, ia64, sparc, sparcv9. It is sparc architecture. Make sure that the release version is 5.1.
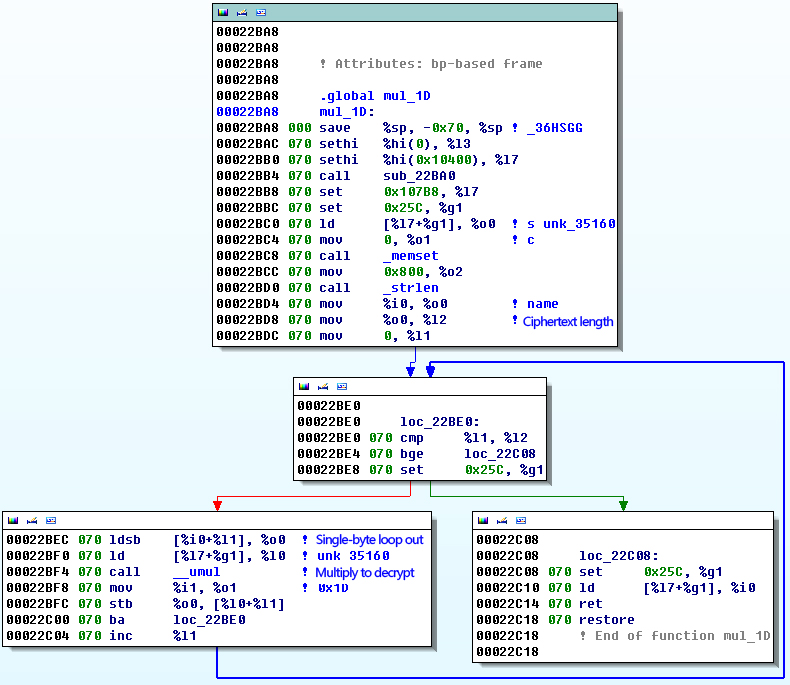
Figure 14 Version judgement
4.2.7 Encrypting the configuration data
There are multiple encryption algorithms inside the sample. One of the encryption algorithms was called multiple times. We analyzed and decrypted the data.
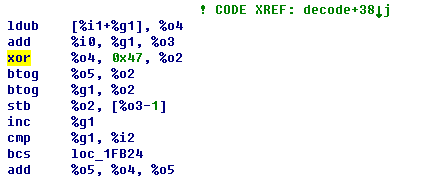
Figure 15 Encryption algorithm
Decrypting encrypted data as follows:

4.2.8 Decrypting and executing other codes / samples
The sample adds the encrypted data at the end of the file. After running, it can decide the size of the encrypted data through the end data, parse and read the data through the defined format. It may load and execute after decrypting the data.
4.3 DoubleFantasy modules in SPARC
The function of the sample is the same with the one on Windows and Linux platform. The main differences are CPU architecture, assembly instructions, storage location of the configuration information and obtained system information.
4.3.1 File Tags
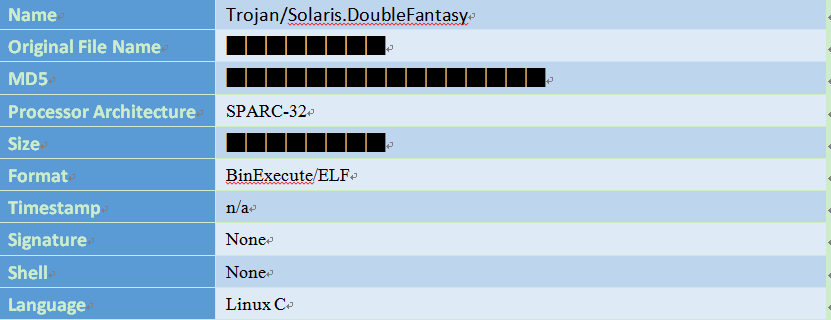
4.3.2 Basic functions
- Initializing the string, dynamic array, decrypt the internal configuration information.
- Connecting Google or Yahoo URL to determine network connectivity.
- Connecting remote URL address. Its remote C & C server address is xxxech.com. The corresponding IP is xxx.xxx.235.237 (One IP of Windows:xxx.xxx.235.235. xxx.xxx.235.235. It belongs to the same network segment. It’s basically determined as the same attack source). It will collect the host information, back to the above address, and wait for the remote host to send instructions.
- Have the function of reading the system account password file. You can steal the user information and password.
- Run with the daemon mode in the sample, achieve the function of self-protection.
- Use a variety of encryption algorithms to encrypt string information.
- Get a lot of system information and back to the server (such as computer name, IP address, process information, account information, etc., the details can be seen in detailed analysis later in this chapter).
- Have 7 network instructions, same functions with Windows version, execute the corresponding instruction operation. The detailed functions of the corresponding command can be seen in detailed analysis later in this chapter.
4.3.3 Configuring Information Encryption
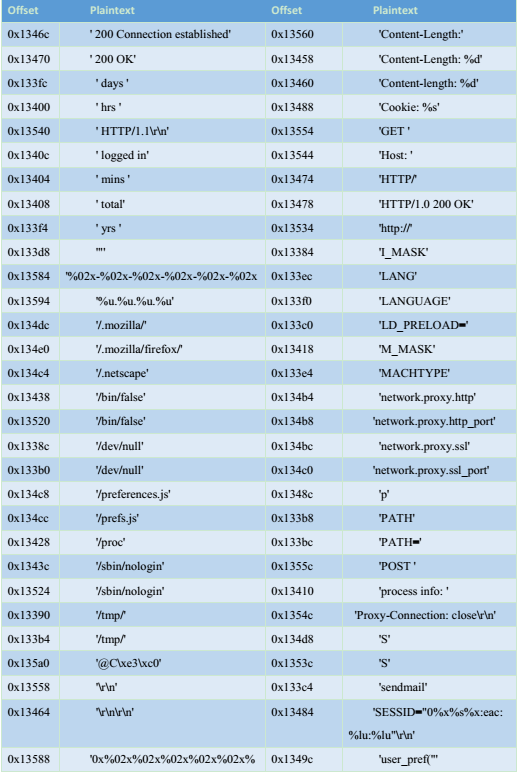
Due to Solaris system does not have the Windows registry, the configuration data will be directly used after decryption. We can see one of the decryption algorithms as follows. The decryption function is called for 63 times.

Figure 16 Strings decryption
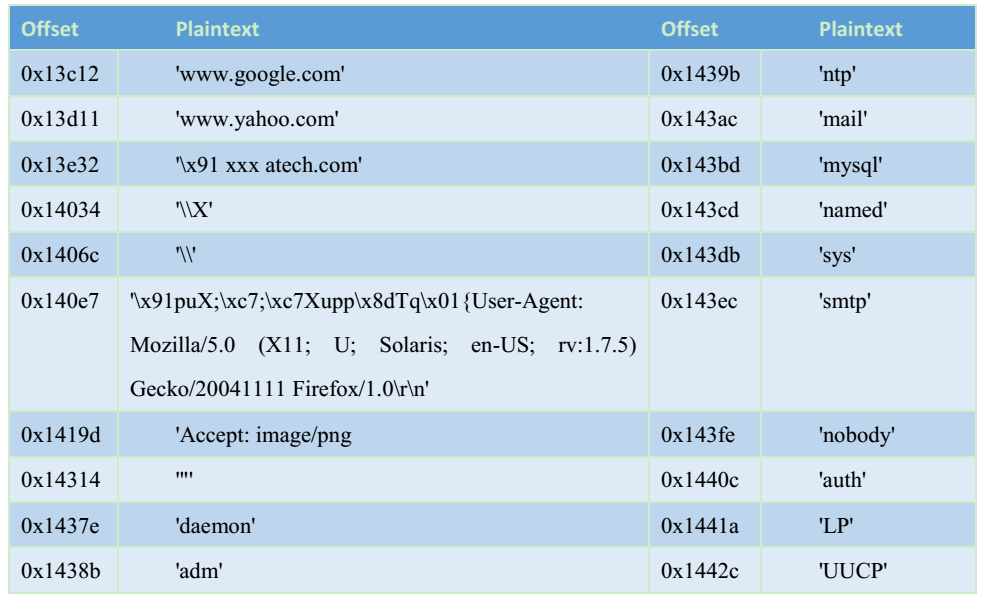
Decrypted string information can be seen in the table below:
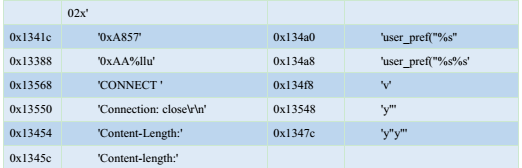
Another encrypted string algorithm is as the required configuration information when encrypted sample is running. The decryption algorithm is as follows:
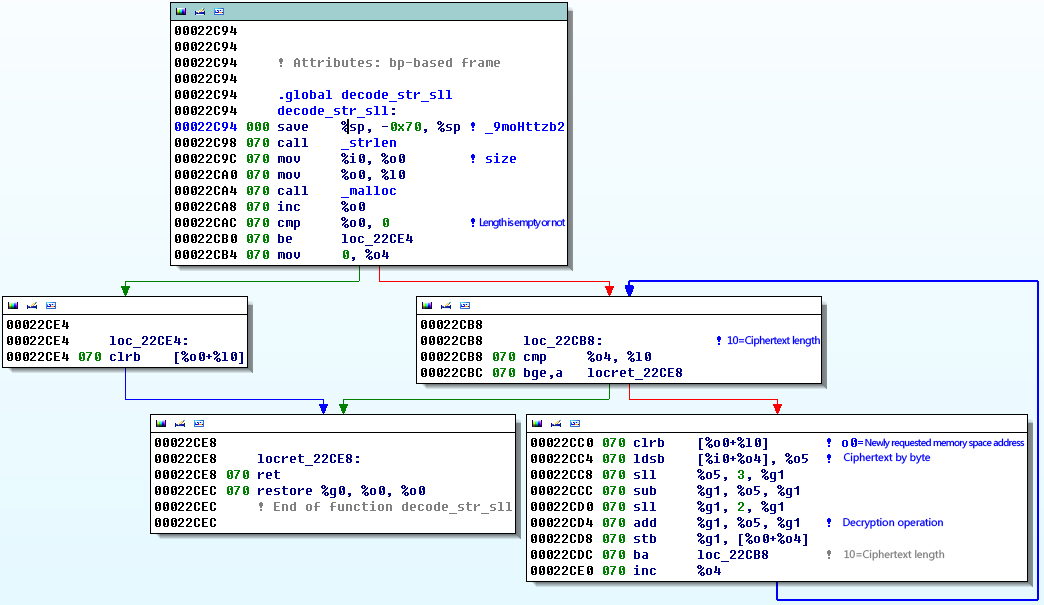
Figure 17 Another decryption algorithm
The content of decryption is shown in the table below:
4.3.4 Network communication encryption
The custom algorithm for the Solaris samples is the same as the one on Windows. There is only one encrypted key (Solaris system does not have a registry. There is no registry encryption function). The key is the same as the one of registry encryption data on Windows platform. The custom encryption algorithms of the two platforms are the same (the specific algorithm can participate in 3.1.6 encryption algorithm analysis).
After analysis, the original 16 key of samples on Solaris is :
66 39 71 3c 0f 85 99 81 20 19 35 43 fe 9a 84 11
Address of the original 16 key in file is the same length as the original 16-bit key of Windows.
Due to that Solaris and Windows samples generate the same algorithm of network communication sub-key, it can generate a sub key:
E9 BE CD E0 A8 9F 4D DB C3 42 AC 2B 24 77 AB CB 5A C1 52 F8 5B 3E F0 78 CB 01 0A 69 29 8F 85 8C
03 9C 7C EF 5E 36 0E 8B C0 40 76 28 9C 9C F2 24 81 9D 02 72 4F 6A BB B5 5B 42 73 14 88 F2 73 75
8B F9 37 98 3B 9F 64 2B A3 C4 FF C7 8A 40 67 C1 25 9F 65 54 45 36 48 FF E2 86 05 1A F4 94 AC 2B
08 D5 E5 83 BE 2C AD EE D0 A6 98 CB 8D 35 ED EE C4 F0 8C F2 CD BA 87 03 54 27 3D 13 A7 9B 6A 05
C7 02 30 21 05 67 58 3B E6 A1 44 0A 37 16 3C 86 E9 BC 8B 20 1A 98 7E 28 E6 7F F7 CA F7 9E 38 31
7F F0 2F 93 11 2B 28 F0 FF 11 B7 FC 1C 63 86 CB
This sub key is used for encrypting and decrypting to send and receive data.
4.3.5 Network control instruction
In the analysis of Solaris samples, we found its function is less than Windows sample orders. There are only seven instructions on Solaris whose function is roughly the same as Windows. Here is the comparison of IDA on two platforms. It can be seen that the instructions of the samples on Solaris is much less and easier than that on Windows.
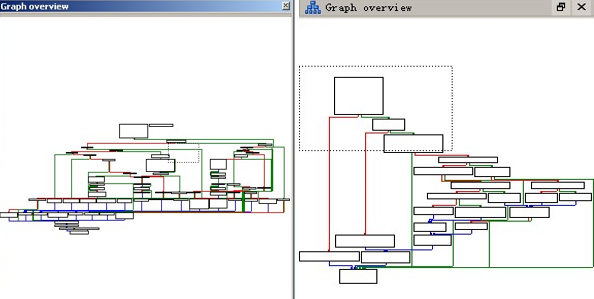
Figure 18 Comparison of network instruction on Windows and Solaris
After analysis, we found that the Solaris sample instruction function is not implemented above. At first, we thought that the instruction function of Solaris sample has not yet been completed, but after further analysis, we found that Solaris samples uses a special kind of dynamic calculation to jump to a different branch instruction code, the red part below is the jump instruction after dynamic calculation.
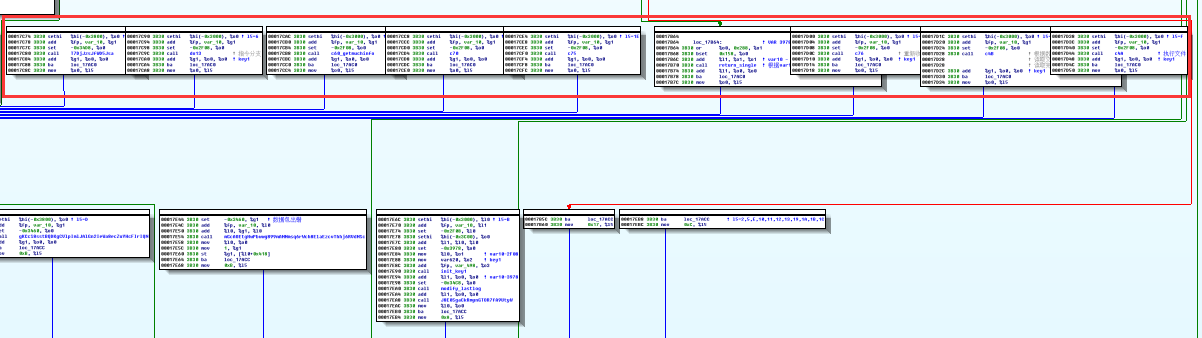
Figure 19 Solaris Branch instruction function
The functions of Solaris instructions are described as below, which is generally the same as Windows instructions:

The download executable samples are the same as Windows, use the same instruction tag through three steps (create, write, execute) to complete the download and execution function, which is different only in code structure. Solaris integrates three instructions to a function.
When executing file, escalate privilege of file first, then use the excele function with parameter executable files,
Parameter 1:file B path
Parameter 2:file B or “sendmail”(relates to mails suspected)
Parameter 3:0
Parameter 4:PATH=%PATH% (environment variable)
For instance: execle(“/usr/bin/sample”,”sample”, NULL, %envp%);
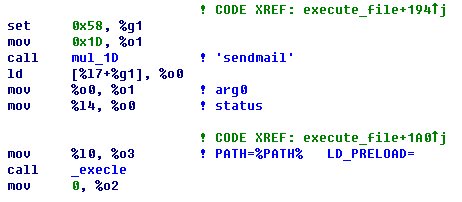
Figure 20 Executable file parameter
The instruction function and packet format of Solaris samples is the same as Windows samples, the full explanation of instruction function and packet format are in section 3.5.6: analysis of instructions of Windows samples.
The collected system information of Solaris samples is slightly different from that of Windows, as follows:

5 Summary
5.1 Improvement based on real threats
Our disclosures of great attack organizations’ capabilities that cover all functional platforms proved to be a real threat not fictitious.
The complicated techniques of attack load, precise design depth and comprehensive environment covering platform have shown the technical capabilities of Equation attacks. The persistent attacks targeting at various certain goals also embody the attackers’ firmly attacking intention. In previous studies, Antiy defined the organizations that equipped with this kind of ability as A2PT and summarized many characteristics of similar attacks from malware payload perspective. These standards are conforming to the behavior and ability of Equations.
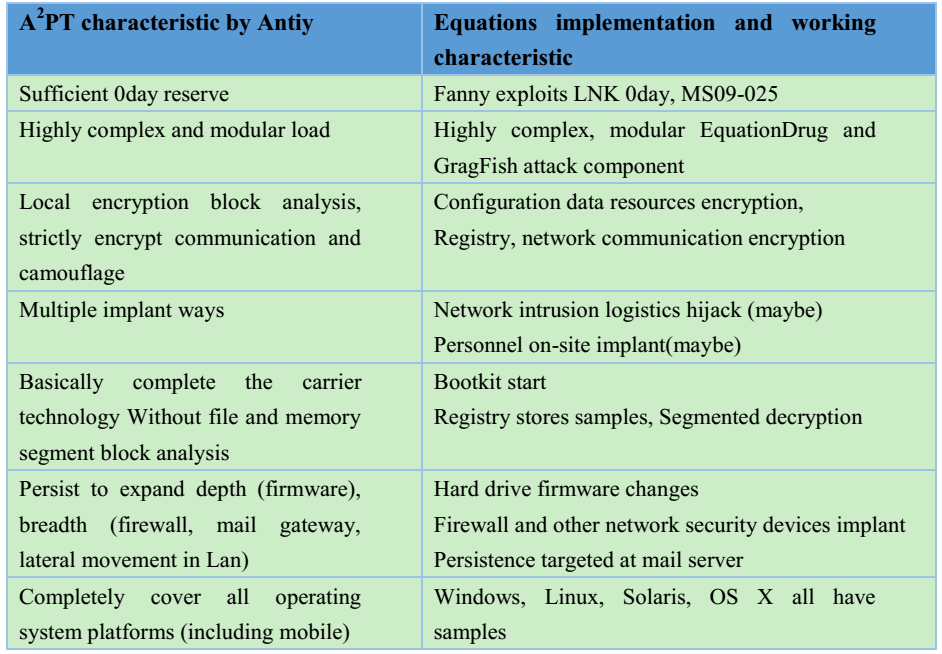
As we have previously outlined, the related attack organizations own ” organic network attack teams and huge supporting engineering system and structured attack arsenal, powerful vulnerability collection and analysis and exploration capacity, and associated resources reserves, as well as systematic operation procedures and manuals, with features as equipment system covering the whole situation, exploitation tools and malicious code that covers the whole platform, persistent ability covering the whole link. In face of such systematic, industrial-strength and highly targeted attacks, perpetual motion must be stop and silver bullet misfiring. Only a clear strategy, full cost investment, defense against systematic [11] attacks, through long-term, solid hard work and ability construction can gradually achieve the initiative.
In some domestic reports about Equation, they read the persistent implant targeting at firmware in high-value targets as that all the current hard disk owns backdoor, which is a misunderstanding. However, when an organization’s ability is big enough and only can be speculated and imaged, it can cause panic, which results in the query of “abuse of supply chain and information chain advantage”.
5.2 Antiy’s efforts
Antiy focuses on the next generation threat detection engine, highly customized in-depth analysis, interactive visual analysis and knowledge and intelligence support targeted at assets and threats.
Antiy also sees the difficulty to against strong organizations, determination and attack cost. Only active collaboration and mutual recognition among vendors that advocate a competency-based security can effectively achieve the mission. In previous analysis in response to “ Cyber Attacks from the Subcontinent” which named as “White Elephant” by Anity, 360 Enterprise Security named it as “APT-C-09”, but the two parties carried on an effective communication and mutual recognition to the other party, which is a good start. We believe that there will be more competency-based security vendor cooperations.
Antiy focuses on the next generation threat detection engine, highly customized in-depth analysis, interactive visual analysis and knowledge and intelligence support targeted at assets and threats.
5.3 Future work
The recent leakage of Equations code and exposure of ANT equipped system enable us to believe that relevant reserves of exploits and attack mentality have flowed into network crime, and even terrorist organizations. Due to the low reproduction cost of existing network attack technology, there exist more serious cyber arms proliferation risks. Therefore, if superpowers can reasonably control their arms development speed and scale of network and effectively prevent and control network arms proliferation that caused by lack of responsibility are the key factors to reach a more secure network.
The recent leakage of Equations code and exposure of ANT equipped system enable us to believe that relevant reserves of exploits and attack mentality have flowed into network crime, and even terrorist organizations. Due to the low reproduction cost of existing network attack technology, there exist more serious cyber arms proliferation risks. Therefore, if superpowers can reasonably control their arms development speed and scale of network and effectively prevent and control network arms proliferation that caused by lack of responsibility are the key factors to reach a more secure network.
We are looking forward to a more secure network world!
Appendix 1: References
[1] Equation Group Cyber Weapons Auction – Invitation
https://github.com/theshadowbrokers/EQGRP-AUCTION
[2] Shadow Brokers reveals list of Servers Hacked by the NSA
http://thehackernews.com/2016/10/nsa-shadow-brokers-hacking.html
[3] Antiy The Trojan modifying firmware Exploration in attack components of Equation Group
http://www.antiy.com/response/EQUATION_ANTIY_REPORT.html
[4] Antiy Analysis of encryption skills used in Equation Group attack components
http://www.antiy.com/response/Equation_part_of_the_component_analysis_of_cryptographic_techniques.html
[5] Kaspersky:Equation: The Death Star of Malware Galaxy
http://securelist.com/blog/research/68750/equation-the-death-star-of-malware-galaxy/
[6] Kaspersky:A Fanny Equation: “I am your father, Stuxnet”
http://securelist.com/blog/research/68787/a-fanny-equation-i-am-your-father-stuxnet/
[7] Kaspersky:Equation Group: from Houston with love
http://securelist.com/blog/research/68877/equation-group-from-houston-with-love/
[8] Kaspersky:Equation group questions and answers
https://securelist.com/files/2015/02/Equation_group_questions_and_answers.pdf
[9] The SPARC Architecture
https://en.wikipedia.org/wiki/SPARC
[10] The Solaris System
https://en.wikipedia.org/wiki/Solaris_(operating_system)
[11] Huang Sheng: Thoughts on Network Defense in Depth
http://www.antiy.com/wtc/2015/02_Joe.pdf
Appendix 2:About Antiy
Starting from antivirus engine research and development team, Antiy now has developed into a group level security enterprise with Antiy Labs as headquarters and both enterprise security company and mobile security company as two wings. Antiy always adheres to the belief of securing and protecting user value and advocates independent research and innovation, forming the layout of the capacity of the whole chain in the following aspects: security detection engine, mobile security, network protocol reduction analysis, dynamic analysis, terminal protection, and virtualization security and so on. Antiy has fostered nationwide detection and monitoring capability with our products and services covering multiple countries. With effective combination of techniques and products of both big data analysis and security visualization, Antiy expands the group work competence of engineers and shortens the product response cycle by massive automation sample analysis platform. With years’ continual accumulation of massive security threat knowledge library, Antiy promotes the solution of situational awareness and monitoring and early warning that targets against APT and at scale network and critical infrastructure, combining with the experience of integrated application of big data analysis and security visualization.
More than 30 famous security vendors and IT vendors select Antiy as their partner of detection capability. The antivirus engine of Antiy has provided security protection for nearly a hundred thousand network devices and security devices and nearly two hundred million mobile phones. The mobile detection engine of Antiy was the first Chinses product that won AV-TEST reward in the world. The technical strength of Antiy has been recognized by industry management organizations, customers and partners. Antiy has consecutively been awarded the qualification of national security emergency support unit four times and one of the six of CNNVD first-level support units. Antiy is the significant enterprise node of China emergency response system, which has provided alarms, in-depth analysis or systematic solution in a few severe security incidents, such as Code Red, Dvldr, Stuxnet, Bash Shellcode, Sandworm, and Equation and so on.
| More information about Antiy Labs: | http://www.antiy.com(Chinese)
https://www.antiy.net (English) |
| More information about enterprise security company: | http://www.antiy.cn |
| More information about Antiy AVL TEAM: | http://www.avlsec.com |
