Analysis of Cyberattacks against the National Bank of Malawi
1、Overview
Recently, Antiy CERT (Computer Emergency Response Team) found a number of samples of phishing email attacks against the National Bank of Malawi during the relevant security incidents. The Republic of Malawi is a landlocked country in southeastern Africa with a land area of 118,000 square kilometers. As of September 2017, its national population totaled 28.4 million, one of the countries with the highest population density in sub-Saharan Africa. Its national economy has long relied on agricultural exports. The government has been rated by the United Nations as one of the poorest countries in the world (from Wikipedia). The National Bank is the largest commercial bank in the country.
Through comprehensive analysis of attack samples and related clues, Antiy found that this is a series of targeted attacks with cross-infiltration through e-mails. The attacker uses the kill-free technique for the old vulnerabilities to construct the attack payload execution entry, and the attack payload is to rewrite and recompile the multiple open source code, embedding the binary remote control Trojan encryption to implement memory execution, to avoid killing and bypassing. The effect of the security mechanism.
In this series of attacks, four local branches of the National Bank of Malawi became an important target for attackers. The official guest mailbox of the Southern District (Southend) has been stolen by attackers. The attacker used an official mailbox password stolen from a branch of the National Bank in advance to send an email with a malicious document attachment to other branch staff. The malicious document attached as an attachment used the CVE-2014-6352 vulnerability [1] to launch an attack. This vulnerability can bypass the security of the Sandworm vulnerability (SandWorm) patch MS14-060. After the exploit is successful, the sample executes an executable called “Target.scr”. The program is compiled and generated by the attacker based on the open source code [2]. The attacker rewrites the main function code. The program does not call the original function of the open source code, but the memory expands and executes the embedded DarkComet far. Control the Trojan, and then launch an attack on the target system.
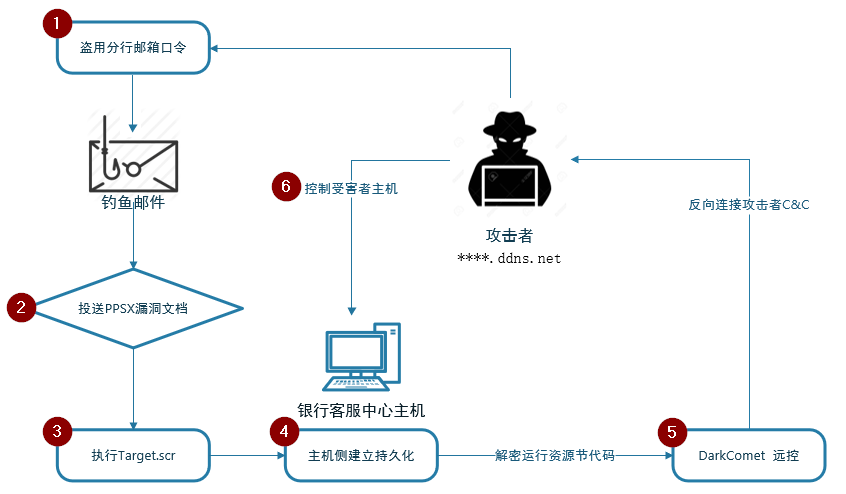
Figure 1-1 Attack process diagram
This series of emails comes from a fixed host and a relatively fixed IP network segment. By searching the attacker’s active network segment, we found that the two IPs involved (185.82.***.*** and 185.82.***.***), the physical location is shown in New Zealand. In early October this year, a series of temporary second-level domain names provided by dynamic domain name vendors were bundled and used as a backhaul C&C server for remote control Trojans; IP 185.82.***.*** of the same network segment was in early October this year, used to mount the well-known ransomware GandCrab.
1.1 Phishing Email Details
The phishing email <1> was sent to the official email address <southend@ managed by an employee of the Southern District Customer Service Center of the National Bank of Malawi on Thursday, October 4, 2018 (Thursday) at 10:43 am. In natbankmw.com> (may be due to geographical proximity and management costs, the Southern District customer service center is incorporated into the Lilongwe regional branch). The sender appears to be “Yousef Syda”, an employee of the Malawi National Bank Salima branch, whose mailbox was alleged to have been stolen.
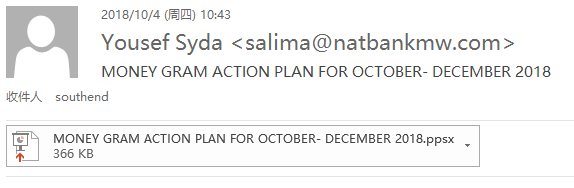
Figure 1-2 Phishing email <1> content
The phishing email <2> was sent to the official mailbox zomba@natbankmw managed by Thomas Chimkowola, manager of the Zomba branch of Malawi National Bank, at 10:52 am on Thursday, October 4, 2018. The sender is still “Yousef Syda”, which is about 9 minutes later than the phishing email <1>.
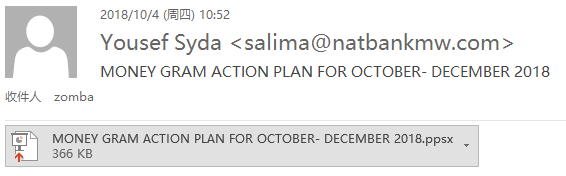
Figure 1-3 Phishing email <2> content
The stolen mailbox Yousef Syda <salima@natbankmw.com>, the IP address of both emails is 185.82.***.***.
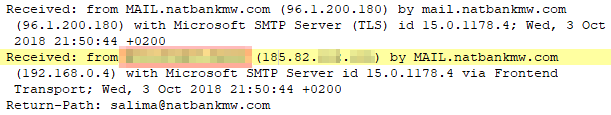
Figure 1-4 IP address of the stolen mailbox
Both messages carry the same title “MONEY GRAM ACTION PLAN FOR OCTOBER- DECEMBER 2018 (MoneyGram Remittance Plan October-December 2018)”, no text, mail title character set attribute is UTF-8, with the same malicious document “MONEY GRAM ACTION PLAN FOR OCTOBER- DECEMBER 2018.ppsx”, which exploits vulnerability CVE-2014-6352[1], and bypasses the security of the Sandworm vulnerability (SandWorm) patch MS14-060 . After the recipient double-clicks to open the ppsx document, it will automatically start the Slide Show playback mode, trigger the Verb action, and execute the malicious code “Target.scr” released in the temporary directory.
1.2 Attacker Information
The victim’s email domain name “natbankmw.com” belongs to the National Bank of Malawi [3]. Founded in 1971, the National Bank of Malawi was formed by merging South Africa’s Standard Bank and DCO (Dominion Colonial Overseas). It now has 850 employees and is headquartered in Malawi. And the business center of Blantyre. As of December 2016, the bank’s total asset value was 314 billion MWK (Malawi Kwacha, approximately $440 million) and is the largest commercial bank in Malawi [4].

Figure 1-5 Malawi National Bank Headquarters Building (latitude: -15.8 Longitude: 35.0)
As of April 2018, the National Bank of Malawi has maintained more than 30 branches throughout the country, referred to as “Service Centers”. However, due to the lack of funds and operational problems in the bank, the management of many“customer service centers”is confusing. In 2016, the employees of the Balaka regional branch were arrested for stealing millions of MWK bank deposits [5]. The cyber attack incident is also the first case for the weak points of regional branches about stealing branch mailboxes and sending phishing emails to other branch employees.

Figure 1-6 One of the victims of the attack, the Lilongwe branch of the National Bank of Malawi

Figure 1-7 One of the victims of the attack, the Zomba branch of the National Bank of Malawi

Figure 1-8 Stolen mailbox affiliated branch: Salima branch of Malawi National Bank
The three mailboxes related to the event are managed by the employees of the three regional branches of the National Bank,“Salima Malawi”, “Zomba Malawi”and“Lilongwe Malawi”. The email address can be obtained from the official website of the bank’s official website and stolen. It is the first employee of Yousef Syda <salima@natbankmw.com>, which may be the first breakthrough for an attacker.
Figure 1-9 Public customer service information published on the National Bank official website
2、Sample analysis
2.1 Sample analysis
The sample “MONEY GRAM ACTION PLAN FOR OCTOBER- DECEMBER 2018.ppsx” was delivered by phishing mail, utilizing the well-known “SandWorm” vulnerability patch bypass vulnerability CVE-2014-6352 [1]. Sandworm vulnerability is an OLE package management INF arbitrary code execution vulnerability. It exists in the OLE package manager on Microsoft Windows servers. This vulnerability affects Win Vista, Win7 and other operating systems. Attackers use PowerPoint as an attack vector. By exploiting this vulnerability, a similar INF external file can be downloaded and executed in the OLE package file (packer.dll), so that the attacker can execute arbitrary commands. Microsoft released the MS14-060 patch for the vulnerability, but by constructing a special CLSID and Verb action, the patch can be bypassed by the vulnerability CVE-2014-6352. Microsoft then released the MS14-064 patch for CVE-2014-6352.
Table 2-1 ppsx sample tags used in events
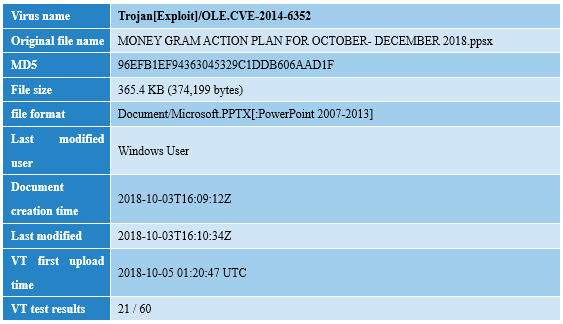
Figure 2-1 The content of the PPSX vulnerability attack document after opening is empty.
The content of the PPSX related files are empty, and no related content construction and disguise are performed. Unzip the PPSX document and find “\ppt\slides\ slide1.xml” to specify the ID of the embedded OLE object as rId3.
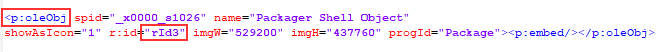
The document “\ppt\slides\_rels\ slide1.xml.rels” specifies the oleObject1.bin under rId3 corresponding to the directory “\ppt\embeddings\”
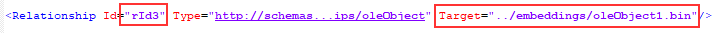
The file “\ppt\embeddings\oleObject1.bin” is an OLE Package object embedded with the PE executable.
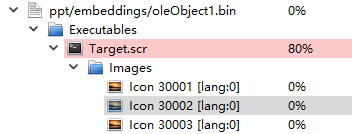
Figure 2-2 The sample is embedded with an OLE object containing PE
The “Olen0Native” stream of the OLE Package object contains a complete PE file. The stream begins with the string to see the original save path of the PE file on the attacker’s machine “C:\Users\Analiz\Desktop\Target.scr” and release The path “%TEMP%\Target.scr”.
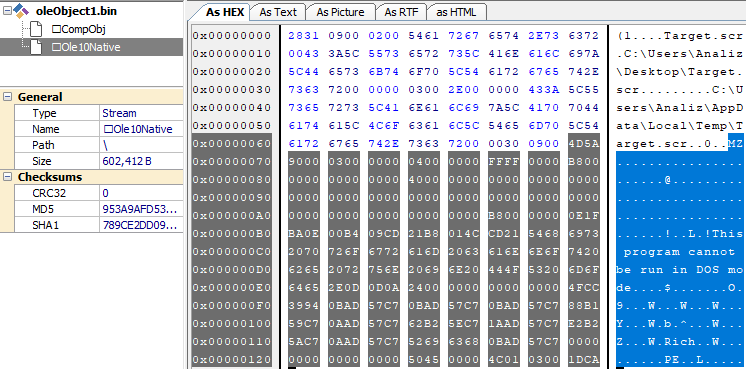
Figure-2-3 The OLE object contains the complete PE data “Target.scr” and the original save path information.
When the module packager.dll calls CPackage::Load to read the OLE Package object, it first calls ReadClassStg to get the CLSID judgment file type of the OLE compound document. The CLSID of the sample OLE object: {0003000c-0000-0000-00c0-000000000046}.
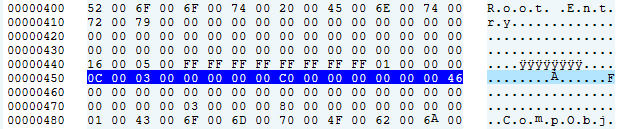
The CLSID corresponds to the OldPackage type, so then call CPackage::PackageReadFromStream→CPackage::EmbedReadFromStream→ CopyStreamToFile to copy the stream data to the temporary directory specific file.
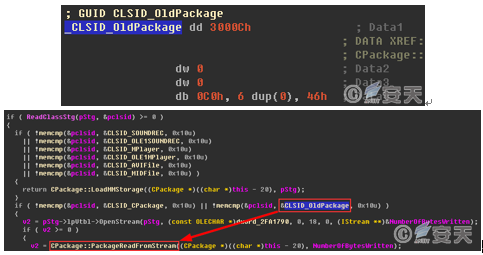
Figure-2-4 The OLE object is judged to be of the OldPackage type, and the stream data is read in.
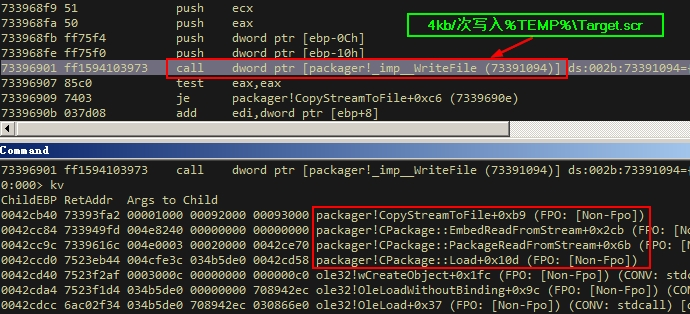
Figure-2-5 OLE object stream data is written to the temporary file “%TEMP%\Target.scr”
In order to fix the “Sandworm” vulnerability CVE-2014-4114, Microsoft released the patch MS14-060 [6],add MarkFileUnsafe function after CopyStreamToFile, the temporary file is processed by MOTW, and its Security Zone is marked as an untrusted source. When the installation is run, the UAC security warning window [7] pops up.
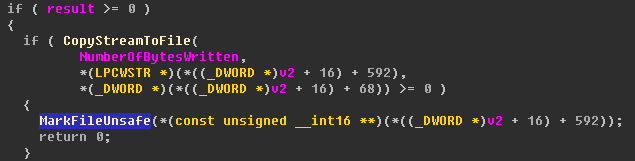
Figure-2-6 Method CPackage::EmbedReadFromStream adds MarkFileUnsafe tag
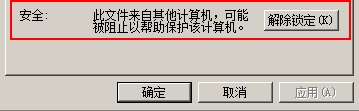
Figure-2-7 “%TEMP%\Target.scr” is marked as untrusted
At this point, “%TEMP%\Target.scr” has been released in the temporary directory. If we open the PPSX sample by double-clicking, the autoplay mode will be enabled, and the Cpackage::DoVerb method of the module packager.dll will check the sample designation. The value of the Verb action “cmd” is assigned to the variables nVerb and nTrueVerb to determine how to handle the embedded file “Target.scr”.
The common method used here is to construct a “cmd” value of 3, which simulates the popup menu operation and executes the second item of the right-click menu “Run with administrator privileges” [8]. Finally, the SHELL32!CDefFolderMenu::InvokeCommand method is called to execute “Target.scr”.
However, the sample “\ppt\slides\ slide1.xml” specifies the Verb action “cmd=0”, and another process is adopted.
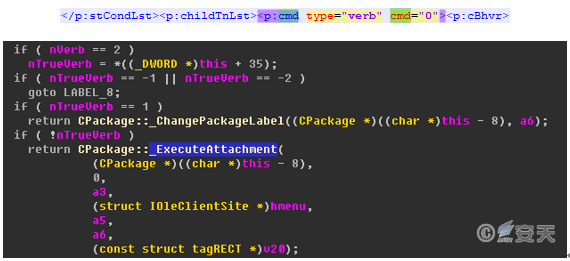
In the debugger we also see that nTureVerb has been assigned a value of 0 and starts executing the function CPackage::_ExecuteAttachment.
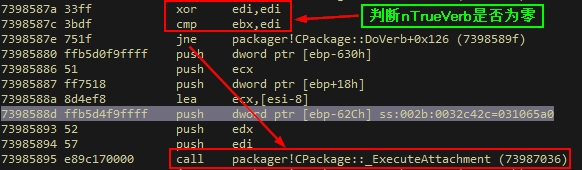
Enter CPackage::_ExecuteAttachment, and we see that it calls the dangerous CPackage::_ActivateEmbeddedFile method, which continues to call the shdocvw!CAttachmentServices::Execute method internally.
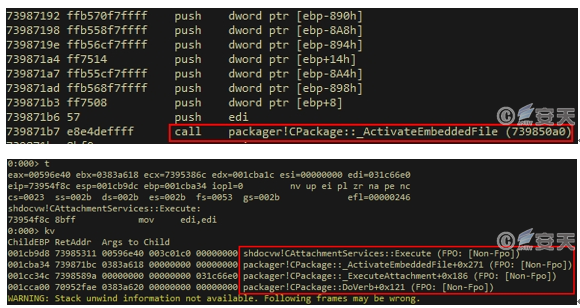
Figure-2-8 The dangerous CPackage::_ActivateEmbeddedFile method is called when “cmd=0”
Shdocvw!CAttachmentServices::Execute calls _OpZoneCheck to check the Security Zone tag of “%TEMP%\Target.scr”, and finally calls _OpUserTrust to pop up the UAC security warning window to remind the user to choose whether to execute “%TEMP%\Target.scr”:
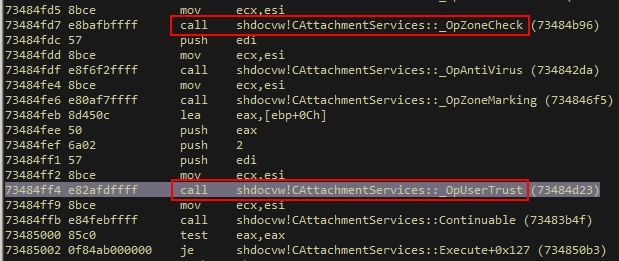
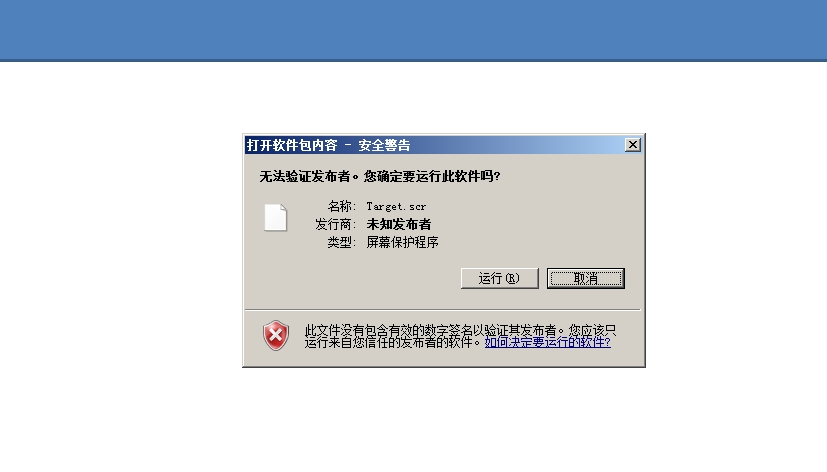
Figure-2-9 Start the Security Zone tag check, and the PPT page pops up the UAC security warning window.
Because the sandworm is a link execution vulnerability, rather than the common format document overflow vulnerability, the memory security defense mechanism such as DEP is invalid. The UAC level is raised to have a certain defense effect on similar vulnerabilities. If the attacker chooses to continue running “Target.scr” at this time, the malicious code will be executed. If the attacker’s system has UAC control turned off or if administrator privileges are obtained, the security warning window will not pop up and “Target.scr” will be executed silently and without warning.
Note: More details on the “Sandworm” vulnerability and its bypass vulnerability CVE-2014-6352 can be found in the analysis articles of Antiy [8] and 360-Day Lab [9] and McAfee [10].
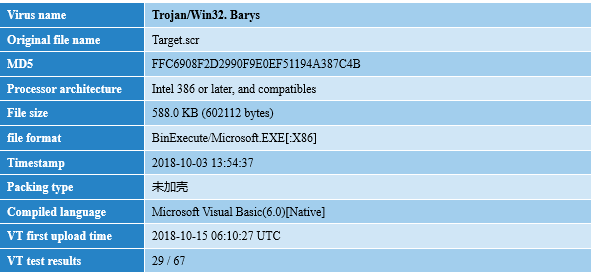
2.2 Target.scr Sample analysis
The Target.scr sample is disguised as a screen saver, written by Visual Basic 6.0 and unpacked. See Table 2-2 for basic information:
Table 2-2 Target.scr sample label
The decompilation analysis found that the original file of the sample was described as “Gate Pass Management System (Klash (Pvt) Ltd.)”:
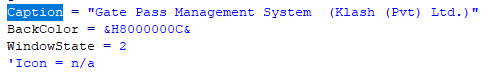
Figure-2-10 After the sample is decompiled, the description “Gate Pass Management System” is displayed.
More of the sample decompiled code is the various database manipulation functions that cannot be called, as well as a large number of database manipulation statements. These database function codes and statements can connect to the database and add, delete, and modify management accounts and inventory records.
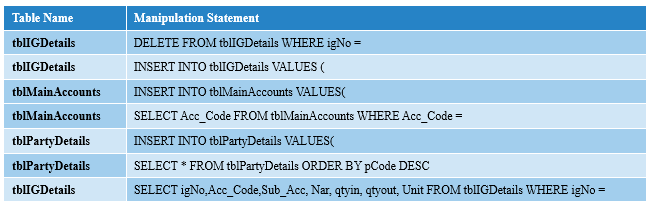
For example, the functions AddNewIGPass() and DeleteIGPass() can add and delete inventory records by manipulating the “tblIGMaster” and “tblIGDetails” tables via SQL statements:
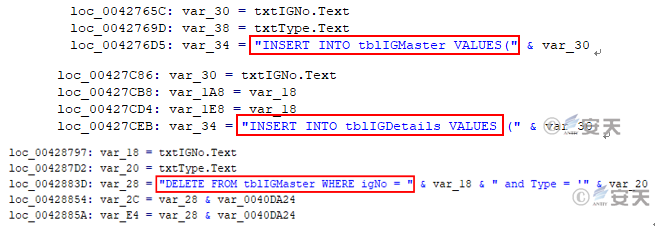
Figure-2-11 Add and delete inventory records via “INSERT” and “DELETE” statements
Table 2-3 List of operated table names and manipulation statements of some databases
Through the comparison of Antiy homologous analysis system, we found the corresponding open source code[2]. According to the project description, this code is applicable to the company’s inventory management system :
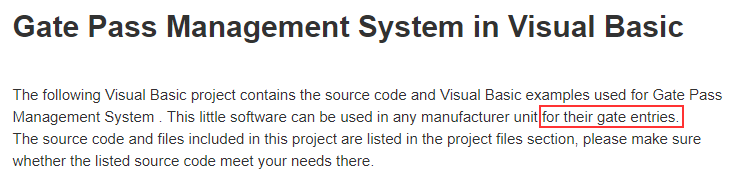
Figure 2-12 Description of the Visual Basic project (this code is applicable to the company’s inventory management system)
This project was developed by “Muhammad Assir Nadeem” who is the IT manager of Klash Private Limited, a garment company within Pakistan. According to our comprehensive analysis, there is no reason to suspect that the company and the project developer were involved in this attack:
Figure 2-13 Personal introduction of the developer of “IGOG Gate Pass System”
The attacker did not use any function calls in the open source code, but embed the encrypted DarkComet remote control Trojan into relevant codes as a data block. Modifying the code of Main function Main_441770() could run the Trojan, and none of the related functions of open source code would be executed. As for the purpose of using normal database management client source code for modification, according to the analysis of more related samples in Section 2.3, it can be considered that this is a deceptive Anti Anti-Virus method.
The modification of function Main_441770() is mainly for two actions:
One is to copy the file “Target.scr” in %TEMP% directory to the startup directory and establish persistence on the host side:
File path: “%AppData%\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\patakia.exe”
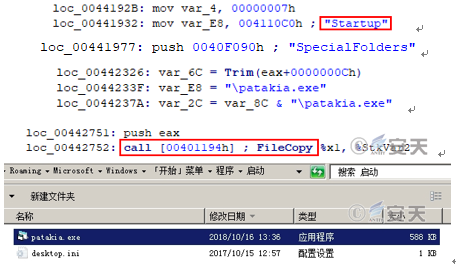
Figure 2-14 Copy itself to the startup directory “patakia.exe”
The relevant Version information of “ptatakia.exe” file is completely in conformity with the open source code:
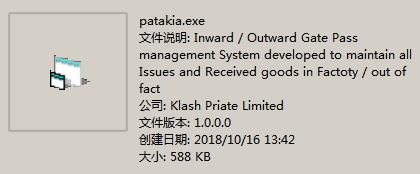
Figure 2-15 Description of the file “patakia.exe”
The other is to decrypt and execute the malicious codes in resource section. The sample modifies the actuating logic based on original database management client source code, and decrypts and executes the encrypted Darkcomet remote control Trojan embeded in resource section in actual operational process. “arkComet RAT”, also known as “Dark Comet” Trojan, which has many functions such as remote control, keystroke log, camera monitoring, file stealing and DDoS attack, is a very common Trojan category in dark industry activities. Because the function code in original open source code will not be called and executed, and the location of the file copy is not in the corresponding program directory, the guess that the attacker establishes persistence entrance to replace the IT tools in original host environment can be excluded basically.
The resource section (where ID=109) for the sample “patakia.exe” contains 32,219 bytes of junk data and 276,995 bytes of encrypted data (header is [++…–…+]):
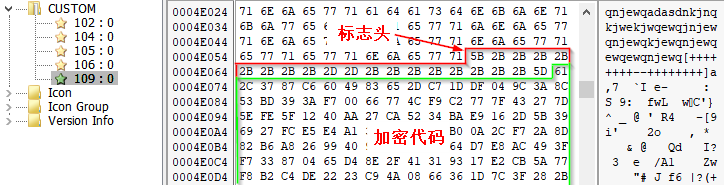
Figure 2-16 Encrypted data contained in resource section ID=109
The encrypted data will be loaded, decrypted, and expanded into a complete Darkcomet Trojan PE file in memory:

Figure 2-17 Load the data that starts with a header from resource section ID=109
Figure 2-18 The PE dumped from memory contains typical Darkcomet Trojan features.
The Trojan tries to backward link to the attacker’s C&C server (desk1pc.ddns.net:700), which current resolves as IP185.82.***.*** . That is the IP of the two phishing emails. It can be considered that the attacker has relatively limited resources.
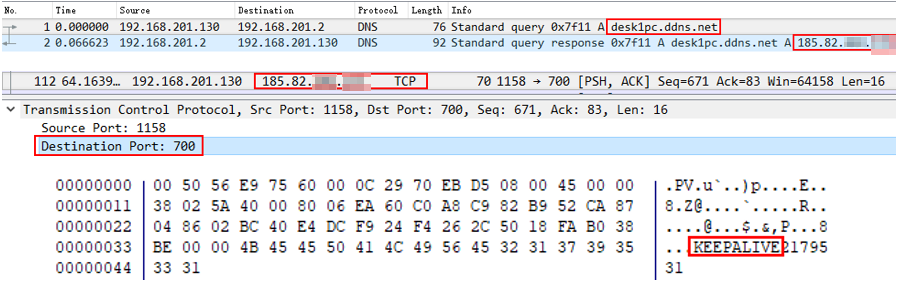
Figure 2-19 “KEEPALIVE+Number” contained in TCP request is for maintaining the network connection with C&C
2.3 Expansion line analysis
According to the information extension in section 1.1 of this report, we can find some other similar techniques with the same attack target-malicious emails of banks. The emails were not sent out from the mailbox of staffs in the National Bank of Malawi, but the mailbox of staffs in other financial institutions was stolen, and the sender of emails came from the same attacker’s host.
One of the letters’ addressee was the Ncalo branch of the National Bank of Malawi. The earliest email was sent via the stolen mailbox Justin Akwuasaba
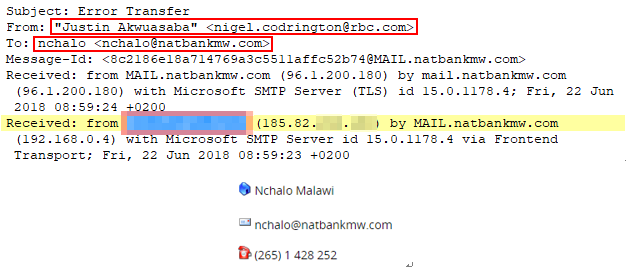
Figure 2-20 The attack mail received by the Nalalah branch of the National Bank of Malawi
There are also bank targets of other countries in attack emails, such as an email sent from mailbox “Audit Dept mgmt@prabhugroupusa.com”, which is the work email of employee in a major financial services (inter-bank remittance and transfer) company “Prabhu”[11] in American. The sending time is “10:19 on Saturday, August 25, 2018”. The IP is “185.82.***.***” which is consistent with the IP of the first email above. The mailbox receiving emails is yenisey.salahov@ibar.az which is the work email of employee in The International Bank of Azerbaijan.
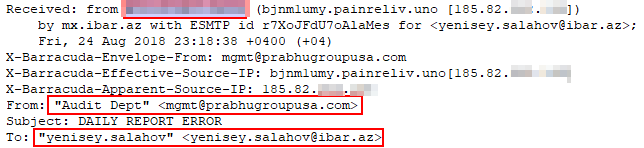
Figure 2-21 The similar attack mail received by The International Bank of Azerbaijan
The two PPSX file attachments of the two emails are the same as the sample described in Section 1.1, they all exploit CVE-2014-6352 vulnerability. “Ole10Native” streams of OLE object all contain complete PE data (“Document.scr”,” Document.exe”), and a new path “C:\Users\kboy\” appears in the original save path. The Verb actions are also set at “cmd=0” to execute the normal program that is bound to malicious codes and released in the temporary directory.
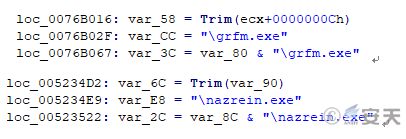
Figure 2-22 The file name of the released PE after copying to the startup directory
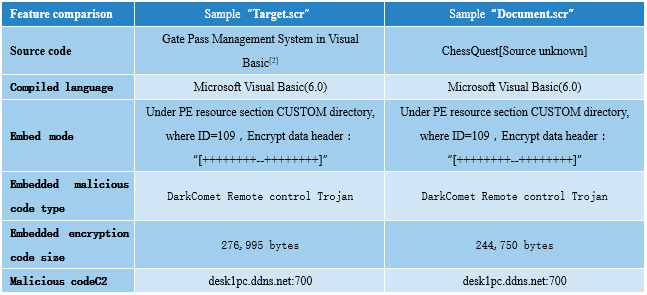
The samples “Document.scr” and “Document.exe” have the same construction technique as the “Target.scr” in Section 2.2. They respectively insert DarkComet Trojan into the source code of the open source program “Tech2ks NComputing Caffe[12]” and chess game “ChessQuest”, even the C2 for passing back of the Trojan share the same domain name and port: “desk1pc.ddns.net:700”. Taking the sample “Document.exe” as an example, feature comparison with the sample “Target.scr” in Section 2.2 can show more similarities:
Table 2-4 Feature comparison of the extension line samples
By checking IP in 185.82.***.***~***, we found that IP 185.82.***.*** and 185.82.***.*** have been used as C&C servers for passing back (They are all bound to temporary second-level domain names kango.ddns.net, kinging.ddns.net, segun.ddns.net, and desk1pc.ddns.net) for three Visual Basic samples and other remote control Trojans described above in early October this year. While IP 185.82.***.*** was used to mount the well-known ransomware GandCrab in early October this year.
According to the expansion line analysis, the attacker used various open source programs as shields to spread malicious codes. Since the source codes can not work properly and the open source programs used are not applications or tools software in common financial scenarios, we believe that the attacker did not replace user’s original program to achieve persistence, but as a technique for Anti Anti-Virus and interference analysis.
3、Summary
According to the given information, cyberattacks on the National Bank of Malawi and financial institutions in many other countries used the same technique. This series of cyberattacks that targeted financial institutions based on the preliminary judgment were criminal behaviors with the purpose of destorying financial assets. At present, besides the judgment that relevant mailboxs of the National Bank of Malawi have been attacked and used to attack, it is still impossible to judge whether the customer service staffs of several branches related to this incident have triggered the attack process and caused actual losses. In view of the vulnerabilities, loads, address resources, and social engineering skills used by attackers, individual attackers or criminal gangs with certain technical capabilities will be more likely.
The operation of financial institutions highly depends on information systems, and traditional financial institutions rely more on physical space security methods to ensure the security of information systems. However, in the age of Internet, due to services provided to a large number of Internet users and business such as inter-bank transnational remittance and transfer, the information systems of financial institutions have already been systems actually with multiple exposed surfaces on the Internet. The service websites, online banking interfaces, work e-mails used by staffs, and inter-bank transfer services in financial systems have been the attack entrances in existing attacks. Especially, as the e-mails of financial institutions are directly exposed information assets, they are easily to be attack entrances for attackers. At the same time, the attacks on the mailboxes of staffs can easily implement attacks based mail trust chain internally and cause chain reaction.
Compare to other cyberattacks on financial institutions analyzed by Antiy previously, such as cyberattacks on Bangladesh Bank, Tien Phong Bank and other countries’ SWIFT systems, this is a low-level attack. As attackers did not use 0day vulnerabilities, and the payloads were not disguised by digital signature theft or other ways, it was an attack that could be effectively restrained and resisted at infrastructure security and defense-in-depth. If relevant financial institutions implement strict security policies and do elemental work well such as patch upgrade and configuration reinforcement, and matched deployments have terminal defense software with active defense capabilities and keeping updates and upgrades, the execution probability of related loads would be greatly reduced. This event objectively represents those financial institutions in some underdeveloped countries which have lower protection level, relatively poor cyber security investment capacity and inadequate risk resistance capacity. The risks caused by cyberattacks may turn into national financial apocalypse.
With the fast development of the whole financial informatization currently at home, China has accumulated a large number of models and experiences in cyber security protection, but in the meantime China needs to cope with the higher security risks and the cyberattacks launched by threat actors in the countries/regions with ultra high capability. These actors have a firm will to attack and can bear huge attack costs. Under the support of a large-scale engineering system, systematic attack operations are carried out. The representative event is that TAO attacked the largest SWIFT service organization in the Middle East. To defend against this kind of cyberattack, capacity-oriented building and a high-level defense capability forming in accordance with the security concept of “comprehensive development, in-depth combination, complete coverage, and dynamic integration” are needed. In this process, China’s competent security vendors should not only do a good job in the present, but also take a global view gradually. They should accumulate security protection concept, experience and solutions together with Chinese financial institutions to provide support and assistance with cyber security capability to financial institutions in underdeveloped countries in the future.
Appendix 1: References
[1]CVE: CVE-2014-6352
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6352
[2]Freesourcecode:Gate Pass Management System in Visual Basic
http://freesourcecode.net/vbprojects/21006/Gate-Pass-Management-System–in-Visual-Basic#.W8PphtlR2Ht
[3]Natbankmw:The official website of The National Bank of Malawi
https://www.natbankmw.com
[4]Wikipedia:National_Bank_of_Malawi
https://en.wikipedia.org/wiki/National_Bank_of_Malawi
[5]Malawi24:workers-steal-millions-from-national-bank
[6]Microsoft:Microsoft Security Bulletin MS14-060 – Important
https://docs.microsoft.com/en-us/security-updates/securitybulletins/2014/ms14-060
[7]Microsoft:Microsoft TechNet
https://technet.microsoft.com/en-us/ms537628(v=VS.71)
[8]Antiy:Sandworm(CVE-2014-4114)The comprehensive analysis report of related threats
http://www.antiy.com/response/cve-2014-4114.html
[9]Freebuf:CVE-2014-6352 The analysis of vulnerability and APT sample
http://www.freebuf.com/vuls/106853.html
[10]McAfee:Bypassing Microsoft’s Patch for the Sandworm Zero Day: Even ‘Editing’ Can Cause Harm
https://securingtomorrow.mcafee.com/mcafee-labs/bypassing-microsofts-patch-for-the-sandworm-zero-day-even-editing-can-cause-harm/
[11]Prabhu:about us
https://www.prabhuonline.com/information/why-us
[12]Freesourcecode:Tech2ks NComputing Caffe in Visual Basic newer version
http://freesourcecode.net/vbprojects/17691/Tech2ks-NComputing-Caffe-in-Visual-Basic#.W_vKmLEzZaQ
